C3D and header insert
Have a F5 that is a WAF so is performing the break and inspect on user web traffic sending through the ASM module. Since the customers backend requires a user certificate I explained to the user there are two options that can be utilized. Option 1 (preferred) the F5 prompts the user for their certificate, then the F5 performs a header insert to the backend systems (Apache) and then it is up to the customer to extract the certificate from the incoming packets. The user certificate will be the original user certificate (not modified). The backend servers must not send the "certificate request" or else the SSL negotiation will be terminated because the F5 will send a self signed cert. Option 2 (less preferred) is C3D. The customer puts the F5 certificate that will be used for signing into their backend store as a trusted CA. When the user connects the F5 prompts the user for their certificate. Then the F5 communicates to the backend server and the backend send the "certificate request". F5 will resign the user certificate and send the certificate with the F5 being the certificate signer. Customer said their Apache must prompt for the certificate, so have C3D setup on the F5 and the F5 is sending the resigned user certificate. When the customer Apache server sends that resigned certificate to the Oracle backend the Oracle refuses the certificate because the customer is storing the original user certificate in the Oracle backend. I asked why does the Oracle backend need the full certificate, the Oracle can be configured to just use the CN from the certificate. Customer answer is because that is how it works. So now the customer wants to utilize C3D and have the F5 perform a header insert of the user original certificate, I am not sure if that can be done. Even then just does not make any sense and makes things more complicated than required.Solved2.1KViews0likes6CommentsUse the REST proxy on the BIG-IQ system ERROR
Hello, I'm working in a local environment trying to use the REST proxy on the BIG-IQ system with the objective of acquire certain info of a BIG-IP. Once I've obtained the BIG-IQ token, discovered the BIG-IP device, enabled the REST-PROXY feature and obtained the BIG-IP uuid (4ad12733-95ea-47b0-a562-dd6ac6da5adc), which basically consists on following the steps found on that websiteEnabling BIG-IQ Centralized Management as a REST proxy for BIG-IP devices (f5.com);it is time to confirm that the BIGIP has been discovered and included into the BIGIP devices group with the code below. headers = { 'X-F5-Auth-Token': f'{token}' } # Request to confirm that the BIGIP was discovered and is included in the cm-bigip-allDevices group url_id = "https://192.168.1.44/mgmt/shared/resolver/device-groups/cm-bigip-allDevices/devices/4ad12733-95ea-47b0-a562-dd6ac6da5adc" response_id = requests.get(url_id, auth=HTTPBasicAuth('admin', 'psw'), headers=headers, verify=False) The problem is that whenI execute that, there is an output variable that states that "state": "PENDING", when that should be "state": "ACTIVE".Why? Do I left something? Am I doing something wrong? Thanks in advanceSolved2.1KViews0likes5CommentsHow I configure syslog included specific string at /var/log/ltm ?
here is our syslog configuration sys syslog { auth-priv-from notice auth-priv-to emerg clustered-host-slot enabled clustered-message-slot disabled console-log enabled cron-from warning cron-to emerg daemon-from notice daemon-to emerg description none include none iso-date disabled kern-from debug kern-to emerg local6-from notice local6-to emerg mail-from notice mail-to emerg messages-from notice messages-to warning remote-servers { remotesyslog1 { description none host X.X.X.X local-ip X.X.X.X remote-port 514 } } user-log-from notice user-log-to emerg } And i want configure syslog to include specific string on /var/log/ltm how I can do this plz help me2.1KViews0likes13CommentsF5 API access from java certificate error
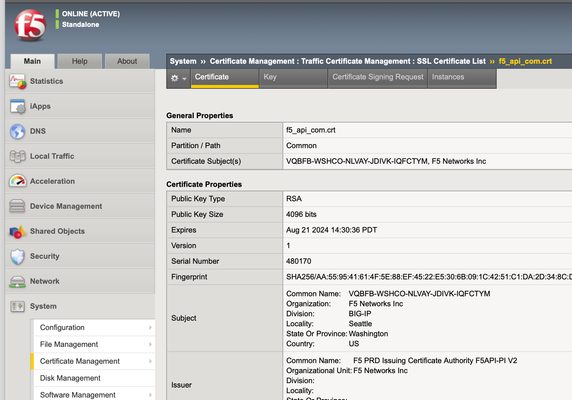
Hi All, I am accessing the F5 API from java, but I get the certificate error on the http request: Caused by: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target But I have downloaded the certificate from the F5 portal and imported in the local java keystore. sudo keytool -importcert -alias f5_api domain -file f5_api_com.crt -keystore cacerts Still i get the above error. Please let me know I am missing anything. Thanks!1.8KViews0likes13CommentsMitigate the Spring Framework (Spring4Shell) and Spring Cloud Vulnerabilities with BIG-IP
UPDATE from F5 Support:Mitigate the Spring Framework (Spring4Shell) and Spring Cloud vulnerabilities with the BIG-IP system You should consider using this procedure under the following condition: You want to secure your applications against the Spring Framework (CVE-2022-22965 aka Spring4Shell) and Spring Cloud vulnerability CVE-2022-22963 with the BIG-IP system. Note: F5 is still actively monitoring the situation and will update this article and/or signatures when more specific information becomes available. Description You can use the BIG-IP system to mitigate the impact of the Spring4Shell and Spring Cloud vulnerabilities in your infrastructure. For more information about these vulnerabilities, refer to K11510688: Spring Framework (Spring4Shell) and Spring Cloud vulnerabilities CVE-2022-22965, CVE-2022-22950, and CVE-2022-22963. Prerequisites You must meet the following prerequisite to use this procedure: To use the BIG-IP ASM/Advanced WAF mitigation, your BIG-IP system must be licensed and provisioned for the BIG-IP ASM/Advanced WAF module. Spring Framework RCE (Spring4Shell): CVE-2022-22965 Spring Framework DoS: CVE-2022-22950 Spring Cloud RCE: CVE-2022-22963 Impact For products withNonein theVersions known to be vulnerablecolumn, there is no impact. For products with**in the various columns, F5 is still researching the issue and will update this article after confirming the required information. F5 Support has no additional information about this issue. AskF5 Article -Spring Framework (Spring4Shell) and Spring Cloud vulnerabilities CVE-2022-22965, CVE-2022-22950, and CVE-2022-22963 F5 Labs Article:What Are The Spring4Shell Vulnerabilities?1.7KViews3likes2CommentsLog4j iRule mitigation as described in K59329043 - which encoding is the regex using ?
Hi Community, just for my understanding - can someone please clarify which encoding is being used in the regex with F5 release under K59329043 in order to mitigate log4j CVEs exploits ? I'm referring to this regex when RULE_INIT { # To switch to a much more aggressive regexp uncomment the first line and comment the second. # set static::log4j_regex {(?i)(\$|\\+(0?44|([u0]00|x)24))'?(\{|\\+(0?173|([u0]00|x)7b))'?} set static::log4j_regex {(?i)(\$|\\+(0?44|([u0]00|x)24))'?(\{|\\+(0?173|([u0]00|x)7b))'?\s*((j|b|\\+(0?1[5140]2|([u0]00|x)[64][a2]))|((\$|\\+(0?44|([u0]00|x)24))?'?(\{|\\+(0?173|([u0]00|x)7b))'?.+?'?(\}|\\+(0?175|([u0]00|x)7d))'?))} } I'm seeing some false positives in the payload of applications where the iRule is at the moment active; nevertheless when I attempt to regex the payload I cannot see any match - so I suspect I might be using the wrong encoding. Thank you for your assistance1.6KViews0likes9Comments201 Recommendations for Study
Hello mates, I am a new member of the forum😀 I have to retake my 201 exam again in February and it´s been a while since the last time I touch a F5 device. I tried to look for the PDF which, as I remember, it was pretty solid material for the exam and the last time, I was able to pass the exam at the first attempt by only using the study guide and a F5 device I had on the lab. But I´ve seen recently that the guide is not longer available where it was: https://clouddocs.f5.com/training/community/f5cert/html/class3/class3.html May you kindly recommend me documentation and good material for my study. Much appreciate it! Regards,1.5KViews0likes6CommentsGet Started with BIG-IP and BIG-IQ Virtual Editions
Try BIG-IP and BIG-IQ Virtual Editions The updated page incudes downloads for AWS, Azure, VMware, Goolge, KVM, Openstack, XEN and HyperV. Deployment templates include Terraform, Azure ARM, Google GDM and Cloudformation. https://www.f5.com/trials/big-ip-virtual-edition1.5KViews6likes2CommentsThe Effect of Persistence on the Round Robin Method
HI F5 Warriors I have a trouble from my costumer.Which in his serveron the server he experiences very different traffic differences between their servers and in the F5 settings he has used the Round Robin method, but in the Persistance Source Address Affiliance profile, so how can the server be able to distribute traffic to the server evenly, due to info from the customer for the apps need persistence profile Thanks for your help!!!1.3KViews0likes4CommentsF5 BIG-IP Automatic email notification for system live update (ASM/AWAF signature)
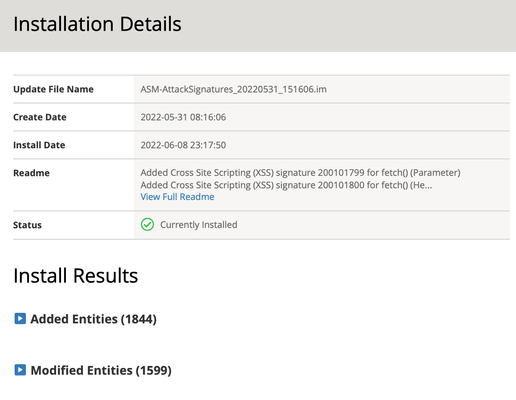
Recently had some request from Security team askingan email to be sent from the F5 BIG-IP when it installs an live update such as ASM signature updates via the automatic schedule. upon looking at KBs it doesn't seem to be a natively embedded function for now. So my idea is to trace system log for signature updates, and generate an SNMP message to trigger email notification. Most syslogs and updates could be found from /log/var/ directory while as some event based log such as Signature updates are located in a different place. https://support.f5.com/csp/article/K82512024 The system live update info is located in /var/log/tomcat/liveupdate.log So the thinking is once the system generate a log after the signature Update, you could try to grab log info and use a unique key word to identify completion of update, and use the key word a customised OID to trigger SNMP trap for system notification. Once you schedule or completed an installation: You should be able to see the log generated with following info: cat /var/log/tomcat/liveupdate.log | grep modifiedEntitiesCount XXXX… {"link":"https://localhost/mgmt/tm/asm/signatures/y5tmU8gG6VdfPFaVbRSPLg","name":"Java code injection - java.util.concurrent.ScheduledThreadPoolExecutor"},{"link":"https://localhost/mgmt/tm/asm/signatures/7KeqKA8hHqv2cfJBXRMz9Q","name":"Java code injection - oracle.jms.AQjmsQueueConnectionFactory"},{"link":"https://localhost/mgmt/tm/asm/signatures/-NXlVMOujg3EvdVKd7PVQA","name":"btoa() (URI)"},{"link":"https://localhost/mgmt/tm/asm/signatures/sqa3ct3N1gOjMZLc3KiNsw","name":"SQL-INJ \"UNION SELECT\" (3) (URI)"},{"link":"https://localhost/mgmt/tm/asm/signatures/J4R4I5KgY8akJtm3TOc55w","name":"\"/etc/php4/apache2/php.ini\" access (Parameter)"},{"link":"https://localhost/mgmt/tm/asm/signatures/S2IcFP11pOpAHjFOSBIi3Q","name":"\"mail\" execution attempt (2) (Header)"},{"link":"https://localhost/mgmt/tm/asm/signatures/HUqMOwJ9SHU6mJF0y3HjBg","name":"SQL-INJ convert(db_name) (Header)"}],"modifiedEntitiesCount":1599} The word: modifiedEntitiesCount seemed to only poppulate upon a installation of signature update completion. so we could use the log key world modifiedEntitiesCount to customise a System OID associate with email alerts https://support.f5.com/csp/article/K3727 add something like the following in to/config/user_alert.conf: alert ASM_update_STATUS " modifiedEntitiesCount(.*)" { snmptrap OID=".1.3.6.1.4.1.3375.2.4.0.xxx" } and create an email alert with SNMP Trap https://support.f5.com/csp/article/K3667 alert BIGIP_SIG_UPDATE_COMPLETE { snmptrap OID=".1.3.6.1.4.1.3375.2.4.0.XXX"; email toaddress="demo@askf5.com" fromaddress="root" body="The Signature has been updated!" } This tricks could also apply to any event based notification you 'd like to sent using keyword from log files. https://support.f5.com/csp/article/K16197 If you would like to put some feed from BIG-IP notification instead of using you log server to filter some tailored events, I hope this could be helpful. Any comments for improvement or correction would be highly appreciated1.3KViews3likes1Comment