Keycloak as IDP for F5 APM via SAML
I have a requirement from our customer to do MFA authentication on F5 APM module and use Keycloak as Identity provider to control their access to web application. Since the keycloak is operate by different team, the internal operation team don’t have an authorize to do MFA on keycloak. They will use F5 APM to perform MFA instead. Existing environment. Solution Protect your web application by deploy F5 as web proxy. Configuration Import your SAML metadata to F5 APM Start by login to your keycloak console and downlond SAML metadata Make sure you have right realm selected. Save as you metadata Navigate to External IDP connector Create External IDP connector Upload your Metadata previously downloaded and name your SAML IDP connector Create your web.f5test.com certificate. Navigate to SSL Certificate list console Create your new certificate Configuration your parameter and click finish Create your Local SP Service Navigate to local SP service console Click create new SP service Input name, EntityID and SP name setting Config POST as assertion consumer service binding Configuration security setting with certificate generated earlier and click OK Binding your SP service with IDP connector Select your newly SP service created Add new row and select you IDP connector profile. Import your SP service to Keycloak Export your SP service Create new client on Keycloak Select file downloaded from previous section Click save3.2KViews0likes1CommentSAML SP ACS Post back resulting in a 404
Hello, I have one application configured to use APM via SAML authentication, the SP & IdP are both running directly on our F5 - this setup is working for many applications only for this one i have problems with the SAML flow. So only some web ressources from this app are protected, we used here an iRule in order to handle this, when i access one of the protected URIs i will be redirected to our IdP in order to get the authentication (KRB Ticket), this is still working i get a session for it (Allowed state) and see also the correct SP in the reference. But the bost pack from Idp to the SP to the ACS /saml/sp/profile/post/acs is resulting in a 404 Accessing protected web ressource -> www.app1.com/protected No session right now so i will be redirected to Idp -> idp.com/saml/idp/profile/redirectorpost/sso (Post; State 302) Redirect back to SP -> www.app1.com/saml/sp/profile/post/acs (Post; State 404) Anybody an idea how to solve this or where i can start with the error search? Thanks, ChristophSolved2KViews0likes4CommentsInvalid Session ID. Your session may have expired - during kerberos auth
I have an IdP setup that is doing client side kerberos auth before then sending on a SAML token to an SP. I have an intermittant issue were sometimes using the kerberos auth It seems to fail and send me to a logout page with an error .../my.logout.php3?errorcode=20 Your session could not be established. The session reference number: 23f22713 Invalid Session ID. Your session may have expired. In the logs I can see: Session deleted (security_check). Sometimes the Kerberos is ok and sometimes not, any ideas where to look for the cause of this? Thanks2KViews0likes5CommentsAPM Create SAML Idp from META-data fails. MCP Error: 01070734:3
Hi, im running into a wierd problem. Im trying to import an external Idp connector from META-data. But im getting an error that i don't understand. I have tried to search in the forum and on the web for an answer but it seems like no one ever had this problem: "MCP Error: 01070734:3: Configuration error: apm aaa saml-idp-connector /Common/etj-ver : Signature verification failed. File contents changed" Anyone know what it means? Im guessing there is something wrong in the META-data but its quite hard to make anything out of this error message. The Idp have a wildcard certificate in it, could that be a problem for APM? Cheers // MattiasSolved1.2KViews0likes8CommentsSAML IdP - Can you have one APM support multiple SAML IdPs?
We have setup one vip and one APM that we want to use for all SAAS logins. We are currently federating with about four saas cloud vendors (Salesforce, box, and others). I don't want to create multiple virtual servers or APMs but for the APM you can only pick one SSO configuration. Each SAML IdP services shows up as it's own SSO configuration. Will I need to do an iRule to switch between them? Also in the documentation it says that you can have multiple IdP for a virtual server. Current Setup SAML IdP Connfiguration * IdP Services -> idp_salseforce (bound to sp connector) sp_connector_salesforce * IdP Services -> idp_box (bound to sp connector) sp_connector_box VirtualServer_SSO_SAML -> APM_SSO_SAML -> SSO Configuration -> Only allowed to pick one idp services (this is the problem)Solved1.2KViews0likes12CommentsSAML Idp-Initiated Connections
I am new to the whole SAML thing and have been playing around with it. I have setup my saleforce dev account to work with our BigIp device and it works perfectly. Since I am still super new to this beg my forgiveness if I mix up any terms, and feel free to let me know. I setup a BigIP as Idp for SalesForce and configured all the settings in the Local Idp Service tab. I then created an External SP connector and connected the Service to that connector. I believe that this is SP-Initiated SAML correct? This allows me to use our AAA (AD) to login to SalesForce. Now I am playing with another vendor that only supports Idp-Initiated Connections. My question is how do I go about creating a Idp Initiated Connection to SP? Thanks!1KViews0likes20CommentsSAML IDP-initiated without webtop
so i have 1 SP initiated SAML setup and working. i have another request to setup an IDP initiated SAML connection. i have get it to work successfully following the guide but after signing into the F5 the users have to click the link in the webtop. from research i know i should be able to send them directly to the correct SAML resource but i have not been able to figure it out. any help would be great? this is the guide i followed https://support.f5.com/kb/en-us/products/big-ip_apm/manuals/product/apm-saml-config-guide-11-3-0/2.htmlunique_882574450886Views0likes16Commentstcl logic in SAML Attribute value field possible?
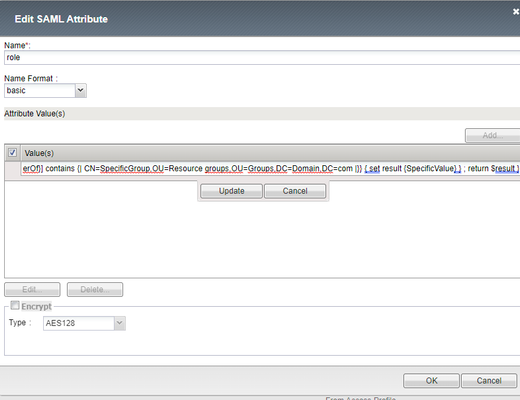
Hi. We're running BigIP as a SAML IDP. Can I somehow issue tcl logic in a SAML attributes? I'm talking about the Access ›› Federation : SAML Identity Provider : Local IdP Services, editing an object, under SAML Attributes. Based on what's in the memberOf attribute, I need to issue as a value either empty string or "SpecificValue". I am familiar with the %{session.variable} construct, but I don't want to clutter the session with more variables if I can avoid it, as that impacts all sessions using our IDP (30 or so federated services on the same VIP and AP). I tried these two approches: %{ set result {} ; if { [mcget {session.ad.last.attr.memberOf}] contains {| CN=SpecificGroup,OU=Resource groups,OU=Groups,DC=Domain,DC=com |}} { set result {SpecificValue} } ; return $result } expr { set result {} ; if { [mcget {session.ad.last.attr.memberOf}] contains {| CN=SpecificGroup,OU=Resource groups,OU=Groups,DC=Domain,DC=com |}} { set result {SpecificValue} } ; return $result } Expected result: An issued claim with the value "" or "SpecificValue" Actual result: An issued claim with the above code as the value As I mentioned, we've set it up using one VIP that is hosting 30 or so services. We're running 16.1.3.1. They are using the same SSO configuration and there's an iRule triggerd at ACCESS_POLICY_AGENT_EVENT, which does some magic to extract issuer and suchlike, and that helps to make decisions later in the Access Policy. It also populates a few session variables under the session.custom namespace for use in the Access Policy. Additional session variables are being populated in the Access Policy, such as resolved manager and their email address. I have looked briefly at the ASSERT::saml functions, but even if it would bepossible to manipulate that way, I wish to keep this set up as stream lined as possible and with as few new "special cases" in an iRule. So while I appreciate pointers along that route as well, I would first of all like to know if there is a way to do it natively in the SAML attribute value field. And if there are any options I have not yet explored here?861Views0likes5CommentsAPM - SAML Attributes Blank
Hello, I am working on implementing a SAML IDP, however I'm running into an issue where the SAML payload is not showing values for the attributes. Example: <saml2:AttributeStatement> <saml2:Attribute Name="uid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"></saml2:Attribute> <saml2:Attribute Name="email" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"></saml2:Attribute> <saml2:Attribute Name="displayname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"> <saml2:AttributeValue xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">email@email.com</saml2:AttributeValue> </saml2:Attribute> The attributes as defined in the IDP Config are: displayname = %{session.logon.last.logonname} email = %{session_logon_last_email} uid = %{session.ad.last.attr.sAMAccountName} What am I missing here?786Views0likes0CommentsBig-IP SAML2.0 IdP to same SP back-end for multiple host aliases
Description I'm wondering how it can be achieved to configure SAML2.0 on APM as IdP in a way to preventNo RelayState mapping found for RelayState value xxxerrors when coming from an FQDN for which SAML2.0 hasnotbeen configured. Example Havingabc123xyz.acme.comexporting SP Metadata and importing IdP Metadata based on this host alias, for which SAML2.0 is operating as expected. Now our customer arenotable to remindabc123xyz.acme.com, so we are offeringfancypad.acme.com(super easy to remind) but getting back RelayState error, which is obvious because forfancypad.acme.comalias no SP IdP relation has been configured. Question Its possible on SP side to configure the IncomingRequest parameters to send theapplication URL, for example, but it will depend if the f5 IdP can differentiate it and send to the same host that did the request? There are customers having used a BIG-IP or other appliances which mentioned forwarding requests to the correct SPs based on specific host aliases and Service-URLs. Thus the URL was appropriately masked and rewritten by the reverse proxy. The host header was replaced with the host value extracted from the matched ACS URI of the internal SP. Would lead to the following example which illustrates the Assertion Consumer Service endpoints for an SP that is only using the SAML2 HTTP-POST binding. BindingEndpointStatus urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POSThttps://abc123xyz.acme.com/sso/SAML2/POSTPre-existing urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POSThttps://fancypad.acme.com/sso/SAML2/POSTNeed to add The question is, how to overcome this behaviour which is leading to 'No RelayState mapping found for RelayState value xxx'? Any help would be greatly appreciated, best wishes Florian778Views0likes0Comments