APM - How to create a keytab file with multiple SPNs
Hi, I have run into a problem using Kerberos Authentication when using CNAMEs in DNS. You can search the web but basically if you use a CNAME record like "www CNAME www1" and then A records "www1 A 10.10.10.1" and "www2 A 10.10.20.1", when IE or .NET needs to authenticate it forms the request to "www1" (or "www2") and not "www". Now, you can add the additional SPNs on the Domain Controllers using the MS tool "setspn" with the "-A" switch no problem against the same service account. The instructions for creating the keytab file only cover the use of the MS tool "ktpass". This tool can only create a keytab file with a single SPN and when you use this with APM it will only work for "www" and break for anything else. I'm unfamiliar with the Kerberos utilities on BIG-IP but I have seen that there are several (kadmin, kinit, ktutil). Can anyone give me a working example of how I can create a keytab file which will work using these tools for all 3 SPNs which will work with MS AD. Thanks.3.8KViews0likes5CommentsKerberos 401 authentication with form fallback
Hello, we are using APM for SAML authentication. Domain joined machines should authenticate transparently with Kerberos, users without the ability to use Kerberos (non domain joined, Firefox without negotiate-settings) should receive a form to login. Kerberos works fine, but users with non domain joined machines receive a browser authentication prompt and "Authentication required to access the resources.". Does anybody has set up such a scenario? Any help is appreciated.3KViews0likes39CommentsSAML SP ACS Post back resulting in a 404
Hello, I have one application configured to use APM via SAML authentication, the SP & IdP are both running directly on our F5 - this setup is working for many applications only for this one i have problems with the SAML flow. So only some web ressources from this app are protected, we used here an iRule in order to handle this, when i access one of the protected URIs i will be redirected to our IdP in order to get the authentication (KRB Ticket), this is still working i get a session for it (Allowed state) and see also the correct SP in the reference. But the bost pack from Idp to the SP to the ACS /saml/sp/profile/post/acs is resulting in a 404 Accessing protected web ressource -> www.app1.com/protected No session right now so i will be redirected to Idp -> idp.com/saml/idp/profile/redirectorpost/sso (Post; State 302) Redirect back to SP -> www.app1.com/saml/sp/profile/post/acs (Post; State 404) Anybody an idea how to solve this or where i can start with the error search? Thanks, ChristophSolved2KViews0likes4CommentsInvalid Session ID. Your session may have expired - during kerberos auth
I have an IdP setup that is doing client side kerberos auth before then sending on a SAML token to an SP. I have an intermittant issue were sometimes using the kerberos auth It seems to fail and send me to a logout page with an error .../my.logout.php3?errorcode=20 Your session could not be established. The session reference number: 23f22713 Invalid Session ID. Your session may have expired. In the logs I can see: Session deleted (security_check). Sometimes the Kerberos is ok and sometimes not, any ideas where to look for the cause of this? Thanks2KViews0likes5CommentsProblems with using Kerberos Authentication
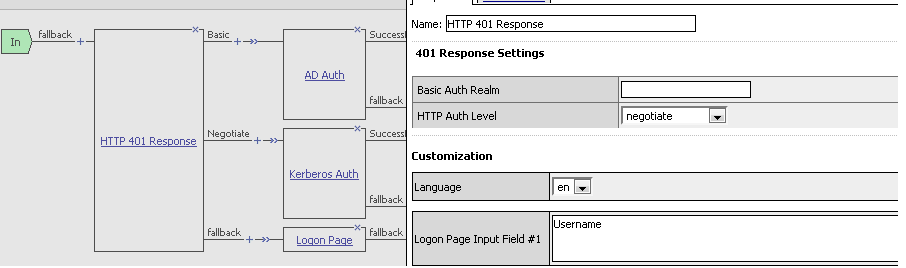
Hi Everyone, Trying to get Kerberos Authentication to work through a APM policy. I am not trying to get SSO to work (well, not yet anyway) - just trying to get Kerberos authentication from a domain attached Windows 7 client. Have followed the documents and created a service account with appropriate settings and imported a keytab file. There is a 'HTTP 401 Response' and a 'Kerberos Auth' step in my pipeline, but it just falls straight through to 'fallback' and denies access. In the APM logs I see: Nov 7 09:48:55 auhof51 debug apd[6907]: 01490000:7: modules/Authentication/Kerberos/KerberosAuthModule.cpp func: "display_status_1()" line: 84 Msg: 850bee9c : GSS-API error gss_acquire_cred: d0000 : Unspecified GSS failure. Minor code may provide more information Nov 7 09:48:55 auhof51 debug apd[6907]: 01490000:7: modules/Authentication/Kerberos/KerberosAuthModule.cpp func: "display_status_1()" line: 84 Msg: 850bee9c : GSS-API error gss_acquire_cred: 186a4 : Is there any way to work out what the GSS-API error number 186a4 might mean? Thanks, Jason1.4KViews0likes8CommentsClient side Kerberos problem with Mac OSX 10.9 and Safari 7.0.2
Hi all, I've got a working client side SSO access policy in APM providing access to an internal intranet. It works perfectly with Windows clients (with the right browser config) and I can get it working on Chrome on our Macs, once the macs have been issued with an initial kerberos ticket for the user's AD account (our KDC is Windows AD 2003). Safari just throws up an APM error page when the user connects with it saying, "Invalid Session ID: Your session may have expired." Checking the APM log even in debug mode doesn't show anything obvious for that session, you just see a message saying the session has been deleted, no kerberos processing begins. On the client side, in a HTTP trace I see this: Request GET /my.policy HTTP/1.1 Host: www.victoria.ac.nz Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8 Connection: keep-alive Proxy-Connection: keep-alive Cookie: LastMRH_Session=77c8fbae; MRHSession=d5087e7f0252687cc231819f77c8fbae; TIN=272000; __utma=189107500.700714022.1406696059.1406696059.1406696059.1; __utmb=189107500.3.10.1406696059; __utmc=189107500; __utmz=189107500.1406696059.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none) User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0) Accept-Language: en-us Referer: http://www.victoria.ac.nz/ Accept-Encoding: gzip, deflate Response HTTP/1.1 401 Unauthorized Server: Apache Content-Type: text/html; charset=utf-8 X-Frame-Options: DENY Pragma: no-cache Cache-Control: no-cache, must-revalidate Accept-Ranges: bytes Connection: close Date: Wed, 30 Jul 2014 04:54:09 GMT Content-Length: 335 WWW-Authenticate: Basic realm="staff.vuw.ac.nz" WWW-Authenticate: Negotiate Set-Cookie: LastMRH_Session=77c8fbae;path=/;secure Set-Cookie: MRHSession=ef9605c9ed0bca0206113f6077c8fbae;path=/;secure Request GET /my.policy HTTP/1.1 Host: www.victoria.ac.nz Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8 Connection: keep-alive Authorization: Negotiate key Snipped for securityYIIHXwYGKwYBBQUCoIIHUzCCB0+gITAfBgkqhkiG9xIBAgIGBiqFcCsOAwYKKwYBBAGCNwICCqKCBygEggckYIIHIAYJKoZIhvcSAQICAQBuggcPMIIHC6ADAgEFoQMCAQ6iBwMFAAAAAACjggYGYYIGAjCCBf6gAwIBBaERGw9TVEFGRi5WVVcuQUMuTlqiJTAjoAMCAQOhHDAaGwRIVFRQGxJ3d3cudmljdG9yaWEuYWMubnqjggW7MIIFt6ADAgEXoQMCAQSiggWpBIIFpdLbJ9FpJ//Bjl+ixeKwBjDZ/1uVgsnoQr4l+kqMazjtr/AILRjfY57mL4hSHX8EWgOObQ+6NlP=******** Proxy-Connection: keep-alive Cookie: LastMRH_Session=77c8fbae; MRHSession=d5087e7f0252687cc231819f77c8fbae; TIN=272000; __utma=189107500.700714022.1406696059.1406696059.1406696059.1; __utmb=189107500.3.10.1406696059; __utmc=189107500; __utmz=189107500.1406696059.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none) User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0) Accept-Language: en-us Referer: http://www.victoria.ac.nz/ Accept-Encoding: gzip, deflate Response HTTP/1.0 302 Found Server: BIG-IP Connection: Close Content-Length: 0 Location: /my.logout.php3?errorcode=20 Set-Cookie: LastMRH_Session=77c8fbae;path=/;secure Set-Cookie: MRHSession=d5087e7f0252687cc231819f77c8fbae;path=/;secure So it looks like Safari is presenting its Kerb ticket, but the F5 doesn’t like it. Anyone got any clues? Thanks, Gavin1.3KViews0likes10CommentsKerberos: can't get S4U2Self ticket for user Exch2016@MYDOMAIN.COM - Server not found in Kerberos database (-1765328377)
We are publishin Exchange 2016 in F5 APM. We are facing an issue for Outlook Anywhere as NTLM authentication is used. I have used latest available iApp for the exchange 2016 deployment and followed deployment guide. Configured Machine Account as well as NTLM Auth configuration. Created delegation account in AD. User is not getting authenticated while accessing Outlook client from outside the office. following error logs I can see from APM Nov 1 13:00:58 F5APM info websso.3[8870]: 014d0011:6: 6cbcede9: Websso Kerberos authentication for user 'Exch2016' using config '/Common/exch_2016.app/exch_ntlm_kerberos_edge_sso' Nov 1 13:00:58 F5APM debug websso.3[8870]: 014d0046:7: 6cbcede9: adding item to WorkQueue Nov 1 13:00:58 F5APM debug websso.3[8870]: 014d0021:7: sid:6cbcede9 ctx:0x87b57e0 SPN = HTTP/mymail.mydomain.com@ABC.NET Nov 1 13:00:58 F5APM debug websso.3[8870]: 014d0023:7: S4U ======> ctx: 6cbcede9, sid: 0x87b57e0, user: Exch2016@MYDOMAIN.COM, SPN: HTTP/mymail.mydomain.com@ABC.NET Nov 1 13:00:58 F5APM debug websso.3[8870]: 014d0001:7: Getting UCC:Exch2016@MYDOMAIN.COM@ABC.NET, lifetime:36000 Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: fetched new TGT, total active TGTs:1Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: TGT: client=svc_apm@ABC.NET server=krbtgt/ABC.NET@ABC.NET expiration=Tue Nov 1 23:00:58 2016 flags=40610000Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: TGT expires:1478030458 CC count:0Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: Initialized UCC:Exch2016@MYDOMAIN.COM@ABC.NET, lifetime:36000 kcc:0x9177068 Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: UCCmap.size = 1, UCClist.size = 1 Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: S4U ======> - NO cached S4U2Proxy ticket for user: Exch2016@MYDOMAIN.COM server: HTTP/mymail.mydomain.com@ABC.NET - trying to fetch Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: S4U ======> - NO cached S4U2Self ticket for user: Exch2016@MYDOMAIN.COM - trying to fetch Nov 1 13:00:58 F5APM err websso.1[8768]: 014d0005:3: Kerberos: can't get S4U2Self ticket for user Exch2016@MYDOMAIN.COM - Server not found in Kerberos database (-1765328377) Nov 1 13:00:58 F5APM err websso.1[8768]: 014d0024:3: 6cbcede9: Kerberos: Failed to get ticket for user Exch2016@MYDOMAIN.COM Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: ctx: 0x9037f10, SERVER: TMEVT_NOTIFY Nov 1 13:00:58 F5APM err websso.1[8768]: 014d0048:3: 6cbcede9: failure occurred when processing the work item Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: ctx: 0x9037f10, SERVER: TMEVT_RESPONSE Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: 6 headers received Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: http header *[:status][401 Unauthorized] (len=16) Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: http header *[WWW-Authenticate][NTLM] (len=4) Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: http header [Server][Microsoft-IIS/8.5] (len=17) Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: http header [Date][Tue, 01 Nov 2016 10:02:13 GMT] (len=29) Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: http header [request-id][e006ab17-b82a-48aa-91a2-dadcd6e5d604] (len=36) Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: http header [Content-Length][0] (len=1) Nov 1 13:00:58 F5APM debug websso.1[8768]: 014d0001:7: Halted SSO retry for request It would be appreciated if anyone have an idea about issue. Nelgin1.3KViews0likes4CommentsKerberos SSO : Server not found in Kerberos database (-1765328377)
Hi, I am trying to configure Kerberos SSO between F5/APM ans IIS. I am getting this error message : Feb 8 18:17:00 bigip12 info websso.3[2776]: 014d0011:6: /Common/Kerb:Common:7828fdf8: Websso Kerberos authentication for user 'testaccount' using config '/Common/SSO-kerberos' Feb 8 18:17:00 bigip12 debug websso.3[2776]: 014d0046:7: /Common/Kerb:Common:7828fdf8: adding item to WorkQueue Feb 8 18:17:00 bigip12 debug websso.3[2776]: 014d0018:7: /Common/Kerb:Common:7828fdf8: ctx:0x8ef0f38 server address = ::ffff:XXX.XXX.XXX.XXX (IP Adresse masqued) Feb 8 18:17:00 bigip12 debug websso.3[2776]: 014d0021:7: /Common/Kerb:Common:7828fdf8: ctx:0x8ef0f38 SPN = HTTP/iis.ad.test.fr@AD.TEST.FR Feb 8 18:17:00 bigip12 debug websso.3[2776]: 014d0023:7: S4U ======> /Common/Kerb:Common:7828fdf8: ctx: 0x8ef0f38, user: testaccount@AD.TEST.FR, SPN: HTTP/iis.ad.test.fr@AD.TEST.FR Feb 8 18:17:00 bigip12 err websso.3[2776]: 014d0005:3: Kerberos: can't get S4U2Self ticket for user testaccount@AD.TEST.FR - Server not found in Kerberos database (-1765328377) Feb 8 18:17:00 bigip12 err websso.3[2776]: 014d0024:3: /Common/Kerb:Common:7828fdf8: Kerberos: Failed to get ticket for user testaccount@AD.TEST.FR Feb 8 18:17:00 bigip12 err websso.3[2776]: 014d0048:3: /Common/Kerb:Common:7828fdf8: failure occurred when processing the work item I tried to follow Kevin Stewart and Cody Green advises but it is still not working (if you read my guys, please do not hesitate to answer :o)). I tried to use this command : kinit -f And it is working. But this one is not: knvo -C -U KNVO is not reconized. Help is welcome, Thanks MD1.2KViews0likes1CommentKerberos Authentication from Multiple Forests
I've set up an F5 APM device with some Kerberos auth using the steps here - http://support.f5.com/kb/en-us/products/big-ip_apm/manuals/product/apm-aaa-auth-config-11-3-0/3.html and it is working for AD accounts in the forest where I have followed the steps. I have struck an issue though with being able to get accounts in another AD forest (that is fully trusted - in the AD sense) to authenticate, or even find log info on why the kerb auth fails. Anybody have any ideas on how to get some log details on why the kerb auth fails, and whats needed to allow accounts from multiple AD Forests?961Views0likes6CommentsKerberos Authentication with different UPN than Kerberos Realm
Using the Exchange 2013 iApp to allow the big ip (v12.0) load balance a pool of Client Access Servers with APM providing authentication, users are receiving Matching Credentials Cannot be Found after successful certificate validation using a Smart Card. Authentication steps include client certificate validation using a smart card and then Kerberos authentication to the domain. Any thoughts? Kerberos: cant get S4U2Self ticket for user 123456@nnn - Matching credentials not found (-1765328243) Kerberos Realm = Test.Lab Domain Controller = dc.test.lab Kerberos Delegation = host/user@test.lab UPN of user account= @nnn835Views0likes2Comments