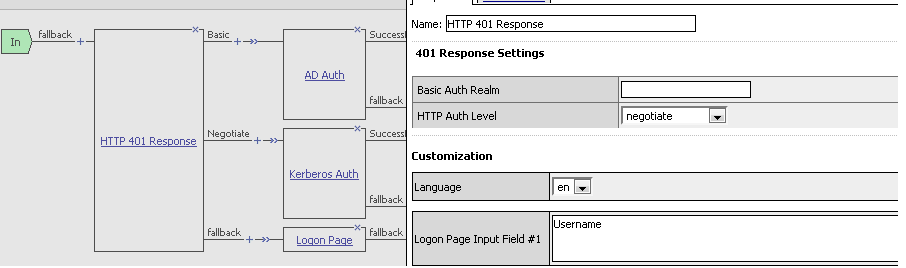
Kerberos 401 authentication with form fallback
Hello, we are using APM for SAML authentication. Domain joined machines should authenticate transparently with Kerberos, users without the ability to use Kerberos (non domain joined, Firefox without negotiate-settings) should receive a form to login. Kerberos works fine, but users with non domain joined machines receive a browser authentication prompt and "Authentication required to access the resources.". Does anybody has set up such a scenario? Any help is appreciated.3KViews0likes39CommentsSAML Cookie Persistence after browser/system restart and across service providers
I am fairly new to the F5 world and in the beginning of setting up our LTM's as SAML IdP's for a variety of services. Our first use-case is Jive, which we have working and all the attributes are pulling across just fine, authentication is fine, everything is functional as is. I'm having a hard time translating what we want the user experience to be into the next phase of the configuration. Our hope was that we could authenticate a user to the LTM, they would be provided a cookie that was set to expire in 24 hours, that cookie would provide SSO access to other services that we'll be adding, and once the 24 hours is up the user would be asked to authenticate again regardless of which service they are logging in to. I've set the Maximum Session Timeout to 86400 seconds (24 hours) and set the cookie to persistent, but when I log in with a test account I don't see a new cookie created on the user system and closing the browser loses the session. In addition, I don't have another sandbox service provider to test with currently to ensure that the cookie we are hoping will be creating would be valid for that other service as well. Am I wrong in thinking that the F5 can provide a persistent cookie that survives beyond browser or systems restarts? Can the F5 only provide SSO for that time period and across SAML partners as long as that browser session is open? I presume I'm asking some pretty elementary stuff so forgive my lack of current knowledge. Any pointers on where I can read up on that or help managing my expectations would be appreciated.1.6KViews0likes17CommentsiRule - jwt is generated prior to authentication
Hoping you guys could shed some light on this, all our efforts have failed so far Scenario: Client hits https://service.com/example Initial uri is stored in an sessions variable called session.server.landinguri Client is redirected to IdP(F5 SAML federation with IDP) Authentication takes place and if completed the client is redirected to the landinguri and a jwt is signed and generated via an iRule (signature, username etc) jwt is passed to the URI (yes, the applications requires this. HTTP header via authorization header is not supported) We have tried generating the jwt in the APM but are unable to decrypt it in to proper format for appending to the URI. This is why we are doing this in an iRule Our problem is that the iRule jwt is being generated at the start of the APM in the initial session BEFORE the authentication is taking place which results in e.g an empty username being displayed. We have been experimenting withACCESS_POLICY_AGENT_EVENT but cant get things to work as it still picks up the jwt that is generated prior to SAML authentication. When debugging we can see 3 jwts being generated in the flow, the first one with an empty username, the following 2 (after successful auth) contain the correct info. Any advice on troubleshooting this is highly appreciated!Solved1.6KViews0likes2CommentsBIG-IP APM: RADIUS and SSO mapping broken
Hi All I think that using a combination of RADIUS authentication (with one-time token) and SSO credential mapping within APM is broken. Credentials entered on the logon page are stored in the username & password session variables. If you do a RADIUS authentication with one-time token, the password variable will be overwritten with the token. So an SSO credential mapping after the RADIUS authentication will get a wrong password. You can prevent this with either putting the SSO credential mapping before the RADIUS block, or "caching" the initial password in a separate variable with variable assign before ( password2 = password ) and after ( password = password2 ) the RADIUS block. However, this fix will not work if the user enters the wrong password initially. The RADIUS block will reload the login page and show you the "wrong credential" warning as often as you define, but the SSO credential mapping or variable assign defined BEFORE the RADIUS authentication won't be updated with the correct password. I know that I could set the "max. attempts allowed" to 1 and have a completely new APM session after every wrong credential or I could build a loop and lose the "wrong credential" message, but those 2 options are not that pretty in my opinion. I'm just wondering if someone has a nice solution to this problem. Cheers PatrickSolved1.5KViews1like4CommentsClient side Kerberos problem with Mac OSX 10.9 and Safari 7.0.2
Hi all, I've got a working client side SSO access policy in APM providing access to an internal intranet. It works perfectly with Windows clients (with the right browser config) and I can get it working on Chrome on our Macs, once the macs have been issued with an initial kerberos ticket for the user's AD account (our KDC is Windows AD 2003). Safari just throws up an APM error page when the user connects with it saying, "Invalid Session ID: Your session may have expired." Checking the APM log even in debug mode doesn't show anything obvious for that session, you just see a message saying the session has been deleted, no kerberos processing begins. On the client side, in a HTTP trace I see this: Request GET /my.policy HTTP/1.1 Host: www.victoria.ac.nz Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8 Connection: keep-alive Proxy-Connection: keep-alive Cookie: LastMRH_Session=77c8fbae; MRHSession=d5087e7f0252687cc231819f77c8fbae; TIN=272000; __utma=189107500.700714022.1406696059.1406696059.1406696059.1; __utmb=189107500.3.10.1406696059; __utmc=189107500; __utmz=189107500.1406696059.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none) User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0) Accept-Language: en-us Referer: http://www.victoria.ac.nz/ Accept-Encoding: gzip, deflate Response HTTP/1.1 401 Unauthorized Server: Apache Content-Type: text/html; charset=utf-8 X-Frame-Options: DENY Pragma: no-cache Cache-Control: no-cache, must-revalidate Accept-Ranges: bytes Connection: close Date: Wed, 30 Jul 2014 04:54:09 GMT Content-Length: 335 WWW-Authenticate: Basic realm="staff.vuw.ac.nz" WWW-Authenticate: Negotiate Set-Cookie: LastMRH_Session=77c8fbae;path=/;secure Set-Cookie: MRHSession=ef9605c9ed0bca0206113f6077c8fbae;path=/;secure Request GET /my.policy HTTP/1.1 Host: www.victoria.ac.nz Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8 Connection: keep-alive Authorization: Negotiate key Snipped for securityYIIHXwYGKwYBBQUCoIIHUzCCB0+gITAfBgkqhkiG9xIBAgIGBiqFcCsOAwYKKwYBBAGCNwICCqKCBygEggckYIIHIAYJKoZIhvcSAQICAQBuggcPMIIHC6ADAgEFoQMCAQ6iBwMFAAAAAACjggYGYYIGAjCCBf6gAwIBBaERGw9TVEFGRi5WVVcuQUMuTlqiJTAjoAMCAQOhHDAaGwRIVFRQGxJ3d3cudmljdG9yaWEuYWMubnqjggW7MIIFt6ADAgEXoQMCAQSiggWpBIIFpdLbJ9FpJ//Bjl+ixeKwBjDZ/1uVgsnoQr4l+kqMazjtr/AILRjfY57mL4hSHX8EWgOObQ+6NlP=******** Proxy-Connection: keep-alive Cookie: LastMRH_Session=77c8fbae; MRHSession=d5087e7f0252687cc231819f77c8fbae; TIN=272000; __utma=189107500.700714022.1406696059.1406696059.1406696059.1; __utmb=189107500.3.10.1406696059; __utmc=189107500; __utmz=189107500.1406696059.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none) User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0) Accept-Language: en-us Referer: http://www.victoria.ac.nz/ Accept-Encoding: gzip, deflate Response HTTP/1.0 302 Found Server: BIG-IP Connection: Close Content-Length: 0 Location: /my.logout.php3?errorcode=20 Set-Cookie: LastMRH_Session=77c8fbae;path=/;secure Set-Cookie: MRHSession=d5087e7f0252687cc231819f77c8fbae;path=/;secure So it looks like Safari is presenting its Kerb ticket, but the F5 doesn’t like it. Anyone got any clues? Thanks, Gavin1.3KViews0likes10CommentsSAML SSO Using Logged In Windows Credentials
Trying to configure our F5 hosted IdP to authenticate clients using their logged in Windows credentials. The SP is an external vendor, we do not need to use Kerberos to authenticate to the application, just trying to use it to get the logged in credentials. Using 401 Response to get logged in credentials, LDAP Query to get variables, and assigning the SAML Resource at the Full Resource Assign. The LDAP lookup appears to be working and I can view the accounts AD variables in the APM report, however the SAML assertion is not being sent. I didn't see any SAML references in the logs so I don't know why, although there was and entry for Could not find SSO domain, check variable assign agent setting We do get the following Kerberos references in the logs KERBEROS agent: ENTER Function executeInstanceKERBEROS module: ENTER Function authenticateUsermodules/Authentication/Kerberos/KerberosAuthModule.cpp func: "display_status_1()" line: 84 Msg: : GSS-API error gss_accept_sec_context: d0000 : Unspecified GSS failure. Minor code may provide more informationmodules/Authentication/Kerberos/KerberosAuthModule.cpp func: "display_status_1()" line: 84 Msg: : GSS-API error gss_accept_sec_context: 186a5 :: KERBEROS agent: LEAVE Function executeInstanceExecuted agent '/Access_Policy_act_kerberos_auth_ag', return value 0 Is what we are trying to do possible? We can get the username from the HTTP 401 Response and set the variables, however SAML assertion not being sent.954Views0likes10CommentsProblem with stream iRule and SAML idp redirect
Running into following issue here. We have a sharepoint site with web servers listening on some high port and using internal hostname. On the SharePoint virtual server I am applying fallowing iRule to do the html parsing and host header translation: when HTTP_REQUEST_RELEASE { Disable the stream filter for all requests by default STREAM::disable LTM does not uncompress response content, so if the server has compression enabled and it cannot be disabled on the server, we can prevent the server from sending a compressed response by removing the compression offerings from the client HTTP::header remove "Accept-Encoding" if {[info exists stream_expr]}{ unset stream_expr } This we want replace set stream_expr "@http://sharepoint.something.somedomain.root:14775@https://sharepoint.somedomain.com@" make sure we have a var to crosscheck before we enable the rewrite in the response set SPresponse 1 } when HTTP_RESPONSE { nable the rewrite to fix the hostnames if {[info exists SPresponse]}{ Check if response type is ... if {[HTTP::header value Content-Type] contains "application/json" || [HTTP::header value Content-Type] contains "text/html" || [HTTP::header value Content-Type] contains "text/xml"} { if {[info exists stream_expr]} { STREAM::expression $stream_expr STREAM::enable}}}} When SP initiated, SAML IDP process request and redirect me back to my SharePoint Site. However, it seems like before the redirect from IDP gets processed by SAML SP, it gets translated by the irule and SAML authentication process never comes to the completion resulting in 404. When iRule is not being applied it seems like SAML authentication comes to completion but of course the site would not work. Any idea how to work around this issue.Solved940Views0likes11CommentsiRule switch pool based on URI
Hello A request was made to re-write/redirect traffic to a different pool based on URI. That is fairly simple with HTTP_REQUEST, and switch. However, this site is using SSO, so if I try something similar it just dumps you back out after authentication. For example: when HTTP_REQUEST { ### # Static variables ### set default_pool "sample-site.com-HTTPS" set non_default_pool "sample-site.com-NON-DEFAULT" set hostlist [list sample-site.com] if { [lsearch $hostlist [string tolower [HTTP::host]]] ne -1 } { switch -glob [string tolower [HTTP::uri]] { "/non-default-page/" { pool $non_default_pool } "/non-default-page/*" { pool $non_default_pool } default { pool $default_pool } } } } That kinda of thing works fine with a normal site. I also looked into doing that with a local traffic policy, but I got the same result. The intent is to keep left side of the URL the same, but I am not exactly sure if that is possible.935Views0likes4CommentsAPM SSO -Kerberos Decrypt integrity check failed
Hi, I have been facing an issue with APM SSO "Kerberos Decrypt integrity check failed" Here are Log details: S4U ======> - fetched S4U2Self ticket for user: xpto@DOMAIN.COM Kerberos: can't decrypt S4U2Self ticket for user xpto@DOMAIN.COM - Decrypt integrity check failed (-1765328353) For this reason the SSO is failing.Any help would be very much appreciated.812Views0likes3CommentsAPM Forms SSO V2 disable password save prompt
When using APM Forms SSO V2 (Client-Side JavaScript) I observe the the browser prompts to save the users password. However the password being submitted is the f5-sso-token marker that APM uses to perform password substitution as the request flows to the backend. This is obviously not the correct password that the browser should cache. Is there a way to indicate that this password should not be saved?792Views0likes4Comments