[Workaound] User required to manually start EPI and VPN in browsers
After upgrading to version 16.1.4 the users need to manually start the End Point Inspector and the Web Initiated VPN by clicking on a "Start" button. This is describe in this KB. I created a user-common.js that will automatically click on the start button for the user. However, please note that this workround works as of 3rd of November 2023, but might stop working in the future in different browsers. In order to activate the workaround you need to have an Access Policy of the Moden type. Then go to Customizations -> Advanced -> Acces Profiles -> <Your Access Profile> -> Common Add the followinf to the file user-common.js define(["require", "exports", "apmui"], function (require, exports, apmui_1) { "use strict"; Object.defineProperty(exports, "__esModule", { value: true }); var app = apmui_1.App.get(); app.subscribe(apmui_1.EventType.EPS_CHECK_PROGRESS, function (_, store) { var btns = document.getElementsByClassName("apmui-button"); if (btns.length == 0) { console.log("Failed to find button..."); return; } btns[0].click(); }); app.subscribe(apmui_1.EventType.DIALOG_OPEN, function (_, store) { setTimeout(function () { var dialog = document.getElementById("sna_auto_start_not_supported"); if (dialog == null) { console.log("Didn't find the right dialog"); return; } var btns = dialog.getElementsByClassName("apmui-button"); if (btns.length == 0) { console.log("Didn't find the start button"); return; } btns[0].click(); }, 100); }); }); If you have a better solution to this, please let me know. This was just what I came up with when asked by customers that the new "Start" button had created confusion among their users.Solved1.2KViews5likes3CommentsF5 APM VPN Support For Microsoft O365 Split-Tunneling
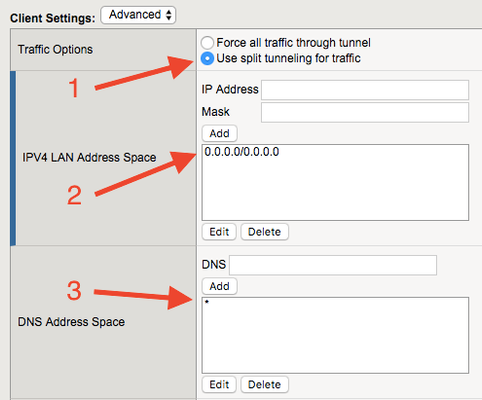
We ran into a significant issue with remote VPN client performance when our Microsoft Office products moved to the O365 cloud offering. Our current limitation of "no split-tunneling" per corporate policy, prevented our users from establishing connectivity to their geographically preferable O365 cloud. Instead, their traffic could/would route back to the corporate F5 APM VPN BigIP and then out to the internet. Much longer path and real-time services such as Teams/Skype calls suffered greatly. Other vendors were also having issues with this such as ForcePoint (Websense) and McAfee. Those vendors released O365 specific patches to permit a better performance through various rules and methods. Our F5 APM VPN was the bottle-neck and we had to address this quickly. Approval was granted to permit ONLY O365 products to be split-tunneled. Luckily, Microsoft has fielded this question/requirement many times and they had a ready answer: https://docs.microsoft.com/en-us/office365/enterprise/urls-and-ip-address-ranges Unfortunately, there's +500 IPv4 networks alone. Many are overlapping and some could be combined into a supernet. Not pretty, but workable. Using node.js, we developed a script that will pull-down the Microsoft IPv4 space, perform a CIDR clean on the networks, log into the F5 BigIP and push the Network Access exclude IP list, then apply the Access Policy in one shot. You can see the repo here: https://github.com/adamingle/f5O365SplitTunnelUpdateScript If you'd like to use the repo, please note the "settings.json" file. You will need to update according to the README.md Additionally, you will need to configure the allowable/tunneled traffic for the Network Access on VPN. If you only specify the exclusion space, there will be no inclusion space and no traffic will traverse the tunnel. Enable split-tunneling by checking the "Use split tunneling for traffic" radio button Add ALL networks to the "IPV4 LAN Address Space" with the IP Address 0.0.0.0 and Mask 0.0.0.0 Specify wildcard/asterisk for the "DNS Address Space" After you have the split-tunneling enabled on your Network Access Lists in F5 APM and you have correctly modified the "settings.json" file of your local f5O365SplitTunnelUpdateScript repo, you should be able to execute your O365 split-tunneling address exclusion changes. Use Jenkins or other automation tool to run the script automatically. Definitely worth a watch: https://channel9.msdn.com/Events/Ignite/2015/BRK3141 *This has been tested/used successfully with the Edge 7.1.7.1 client on v13.1.11.6KViews2likes7CommentsF5Access | MacOS Sonoma
I upgraded my MacOS to Sonoma (the latest version of MacOS) and now F5 Access does not open When I try to open the application, nothing happens. The icon in the up menu bar does not appear. Is anyone passing through the same situation? Thanks! Thanks!2.2KViews2likes45Commentscant access to management interface after vpn using apm established
i had configured network access vpn using APM module, i tried to split tunneling the network of my management access, but unfortunately when the vpn established i cant connect to my f5 management interface. i tried to add VS with my pool member is my f5 management ip address, where VS ip address is 1 network with my VPN user, the service is https, and the pool member is my f5 management ip address with service port is 443. and then the result is i can ping my VS but i cant connect to my VS which have the pool member is my f5 management ip address with port 443 any idea how can i access to my F5 after vpn using APM established? really appreciate your help thank you1.7KViews1like4CommentsAPM sessions broken out by access policy?
I don't believe this is possible, but I'll ask just to be sure... For VPN, based on their user ID or an Active Directory query, etc., a user is assigned an APM access policy appropriate for their level of access. Is it possible, beyond running a custom report via the GUI, to display/track the current number of users connected via one access policy or another? I've used "tmsh show /apm license" to see how many licenses are consumed, and have also run reports via the GUI to see how many people have connected via a specific APM policy, but this is a bit beyond that. I'd think there would have to be some mechanism to tally not only connections via an APM policy, but one to update the total whenever a session terminates. Thanks!Solved557Views1like2CommentsVPN - Disallow networks accessible via access policy "exclude" or via APM ACL instead?
From what I can tell, there are two ways to block access to certain networks via VPN; either by adding them to the "exclude" section of the access policy they're assigned, or by adding an ACL step in APM. An excluded network will still be pushed to the client, but the metric assigned will tell it to go out the "local" connection rather than the VPN tunnel. With an ACL, it's just blocked at the F5. My question is, beyond the example above, is there a reason to use one method over the other? I'm thinking an ACL would be preferable if one wants to "hide" the network(s) they don't want VPN users going to. Thanks!Solved598Views1like1CommentActive directory cannot resolve remote ssl vpn computer
Gents, I hope you can help me with this. Is it possible a remote vpn computer can be seen by AD ?. VPN works, AD can ping the remote computer, but cannot resolve its hostname. Those are corporate computers that have been joined to the domain already. Please advise.320Views1like2CommentsSNAT based on source and destination
Greetings, I am working on Forwarding (IP) VS. I have used the next: when CLIENT_ACCEPTED { if { [class match [IP::client_addr] equals VPN-SUBNET] } { if {[class match [IP::remote_addr] equals APP1]} { snat 10.13.0.25 } } else { forward } } And also this one: when CLIENT_ACCEPTED { if { [class match [IP::client_addr] equals VPN-SUBNET] and [class match [IP::remote_addr] equals APP1]} { snat 10.13.0.25 } else { forward } } Both of them do not work, there is no error while building the policy, just the traffic does not get snated to 10.13.0.25. This one works, but snat all the traffic to 10.13.0.25, and I need only for a specific destination: when CLIENT_ACCEPTED { if { [class match [IP::client_addr] equals VPN-SUBNET] } { snat 10.13.0.25 } else { forward } } Could you advise how SNAT from an specific source and destination ? Thanks, Edouard.Solved563Views1like2CommentsF5 VPN Broken on Ubuntu 18.04 LTS
Heads up, the Ubuntu package for the F5 VPN is broken under the upcoming Ubuntu 18.04 LTS. The dependencies are clearly wrong since there has been an ABI change between Qt5.5 (as advertised) and Qt5.9 (installed) - The UI doesn't even show up. Listed dependencies: libqt5core5a (>= 5.5), libqt5network5 (>= 5.5), libqt5widgets5 (>= 5.5), libqt5gui5 (>= 5.5), libqt5dbus5 (>= 5.5), libqt5sql5 (>= 5.5), libqt5webkit5 (>= 5.5), libqt5opengl5 (>= 5.5), libqt5printsupport5 (>= 5.5) Since the package will likely be used on different debian-compatible architectures, it would be advisable to statically compile the library and remove the dependecy alltogether instead of relying on people having an ABI-compatible version that you compiled with. A timely update is appreciated, thanks.1.5KViews1like10Comments