SSL Client Certification Alert 46 Unknown CA
We are seeing 'Alert 46 Unknown CA' as part of the initial TLS handshake between client & server. From a wireshark capture, the 1st Client Hello is visible, followed by the 'server hello, certificate, server key exchange, certificate request, hello done'. As part of this exchange, TLS version 1.2 is agreed, along with the agreed cypher. The next packet in the flow is an ACK from the source, followed by Alert (Fatal), Description: Certificate Unknown. I cannot see anywhere in the capture a certificate provided by the client This behaviour occurs regardless of the client authentication/client certificate setting (ignore/request/require). I have ran openssl s_client -connect x.x.x.x:443 as a test (from the BIG-IP) and I see the server side certs and 'No client certificate CA names sent' which is expected as no client cert sent. The end client has not reinstalled the client certificate as yet (3 day lead time). Are there any additional troubleshooting steps I can undertake to confirm the client is either rejecting the server certificate and therefore not returning the client certificate? Kind RegardsSolved25KViews0likes17CommentsHow to tell nginx to use a forward proxy to reach a specific destination
Hello. I accidentally closed my previous post, so I recreate this discussion because of the following problem I'm encountering. Here is the situation : I have multiple servers which are in a secure network zone I have another server where nginx is installed and is used as a reverse proxy. The NGINX server has access to a remote destination (a gitlab server) through a forward proxy (squid) So the flow is the following : Servers in secure zone --> Server Nginx as reverse proxy --> Server squid as forward proxy --> an internal gitlab in another network zone. Is it possible to tell nginx to use the squid forward proxy to reach the gitlab server, please ? For the moment, I have this configuration : server { listen 443 ssl; server_name <ALIAS DNS OF NGINX SERVER>; ssl_certificate /etc/nginx/certs/mycert.crt; ssl_certificate_key /etc/nginx/certs/mykey.key; ssl_session_cache shared:SSL:1m; ssl_prefer_server_ciphers on; access_log /var/log/nginx/mylog.access.log; error_log /var/log/nginx/mylog.error.log debug; location / { proxy_pass https://the-gitlab-host:443; } } But it does not work. When I try to perform a git command from a server in secure zone, it fails and in the nginx logs I see a timeout, which is normal, because nginx does not use the squid forward proxy to reach the gitlab server. Thank you in advance for your help ! Best regards.Solved20KViews0likes12CommentsHow to rewrite a path to a backend service dropping the prefix and passing the remaining path?
Hello, I am not sure whether my posting is appropriate in this area, so please delete it if there is a violation of posting rules... This must be a common task, but I cannot figure out how to do the following fanout rewrite in our nginx ingress: http://abcccc.com/httpbin/anything-> /anything (the httpbin backend service) When I create the following ingress with a path of '/' and send the query, I receive a proper response. curl -I -k http://abczzz.com/anything apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: mikie-ingress namespace: mikie spec: ingressClassName: nginx rules: - host: abczzz.com http: paths: - path: / pathType: Prefix backend: service: name: httpbin-service port: number: 8999 What I really need is to be able to redirect to different services off of this single host, so I changed the ingress to the following, but the query always fails with a 404. Basically, I want the /httpbin to disappear and pass the path onto the backend service, httpbin. curl -I -k http://abczzz.com/httpbin/anything apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: mikie-ingress namespace: mikie annotations: nginx.ingress.kubernetes.io/rewrite-target: /$2 spec: ingressClassName: nginx rules: - host: abczzz.com http: paths: - path: /httpbin(/|$)(.*) pathType: Prefix backend: service: name: httpbin-service port: number: 8999 Thank you for your time and interest, Mike17KViews0likes15Commentssnat vs automap, whats the difference?
I'm trying to see the difference between the snat and automap for the Source Address Translation option. Currently I have traffic coming in to the F5 using automap. What though specifically does that mean? And why wouldn't I use SNAT? All the nodes, (servers in our lan), are not configured to have the F5 as its default gateway. I have a lot of virtual servers configured and I'm not sure how the self-ip plays a role in the nating or snating if at all. From what I understand (but could be wrong) an external client request is directed to the vip ip (since our firewall nats it there) and the destination IP is that of the vip. The F5 then translates the destination IP to that of the IP of the pool member. Then on the way back out the source is translated to the of the vip. But what about the selfip? Can someone please explain all this? Thanks!14KViews0likes8CommentsHow to import a SSL Cert and Key to F5.
I'm browsing the SSL certificate list which I got from Comodo, and there are different types of Contents with the below mentioned extentions. I have experience in uploading certificates to F5 which is in .pfx format that contains both certificate and key in a single file but the newly received CA certificates giving me a hard time understanding which one is a cert file and which one is key file. Can someone help. xyz_com.cer xyz_com.crt xyz_com.p7b xyz_cert.cer xyz_com_interm.cer13KViews0likes4CommentsIncrease DH key exchange to 2048
I'm trying to move from cipher lists in the ssl profile to cipher rules and groups in order to support TLS1.3 I would like to only enable strong cipher suites. So far I've found this list TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 So far I've come up with this string to reproduce the list: ECDHE+AES-GCM:DHE+AES-GCM:CHACHA20-POLY1305 Each time I test it the DHE+AES-GCM gets flagged because it is only 1024 bits. Removing it means removing a lot of clients from the compatibility list. After days of reseach I can't find the place to increase my DH group strength. Only a 5 year old article which says that I can't increase it. Does anyone know if it is possible to increase DH group strength in either 13.1.1 or 14.1.2, and where to do it?Solved11KViews0likes16CommentsSSL Handshake failed for TCP
We are seeing a ton of these messages in our logs. Several per minute from legit client IPs. However, the clients are not reporting any issues. SSL Handshake failed for TCP x.x.x.x:11555 -> x.x.x.x:443 These particular messages are NOT followed up a connection error message about an unsupported version as you might expect (for example: Connection error: ssl_hs_rxhello:7699: unsupported version (40)). I am trying to understand what is occurring. I did a pcap but was not able to get much out of it since there was a lot of normal traffic in there as well since these are good source IPs. I did not find any fatal handshake errors. Anything else I could look for in a pcap to see what is occurring? What other instances would you see a message like this? The frequency of the messages increase/decrease with peak and off peak times. The application is a typical IIS web app where the client uses a browser to access.10KViews0likes3CommentsHow to disable weak cipher from Client SSL Profile
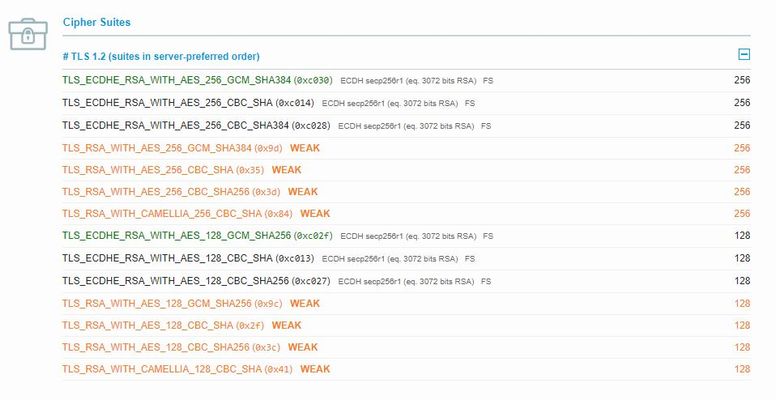
Hi, We have disabled few ciphers and we have rating "A" in qualys ssl checker portal. We have a requirement to disable weak ciphers as well. Could some one advice how to disable weak ciphers. Please find the attachment for reference. ThanksSolved10KViews1like25Comments