Prevent BIG-IP Edge Client VPN Driver to roll back (or forward) during PPP/RAS errors
If you (like some of my customers) want to have the BIG-IP Edge Client packaged and distributed as a software package within your corporate infrastructure and therefore have switched off automatic component updates in your connectivity profiles, you might still get the covpn64.sys file upgraded or downgraded to the same version as the one installed on the BIG-IP APM server. Background We discovered that on some Windows clients the file covpn64.sys file got a newer/older timestamp in and started to investigate what caused this. The conclusion was that sometimes after hibernation or sleep, the Edge Client is unable to open the VPN interface and therefore tries to reinstall the driver. However, instead of using a local copy of the CAB file where the covpn64.sys file resides, it downloads it from the APM server regardless of if the version on the server and client match each other or not. In normal circumstances when you have automatic upgrades on the clients, this might not be a problem, however when you need to have full control on which version is being used on each connected client, this behavior can be a bit of a problem. Removing the Installer Component? Now you might be thinking, hey… Why don't you just remove the Component Installer module from the Edge Client and you won't have this issue. Well the simple answer to this is the fact that the Component Installer module is not only used to install/upgrade the client. In fact, it seems like it's also used when performing the Machine Check Info from the Access Policy when authenticating the user. So by removing the Component Installer module result in other issues. The Solution/workaround The Solution I came up with is to store each version of the urxvpn.cab file in an IFile and then use an iRule to deliver the correct version whenever a client tries to fetch the file for reinstallation. What's needed? In order to make this work we need to Grab a copy of urxvpn.cab from each version of the client Create an IFile for each of these versions Install iRule Attach iRule to the Virtual Server that is running the Access Policy Fetching the file from the apmclients ISOs For every version of the APM client that is available within your organization a corresponding iFile needs to be created. To create the iFiles automatically you can do the following on the APM server. Login to the CLI console with SSH Make sure you are in bash by typing bash Create temporary directories mkdir /tmp/apm-urxvpn mkdir /tmp/apm-iso Run the following (still in bash not TMSH) on the BIG-IP APM server to automatically extract the urxvpn.cab file from each installed image and save them in the folder /tmp/apm-urxvpn. for c in /shared/apm/images/apmclients-* do version="$(echo "$c" | awk -F. \ '{gsub(".*apmclients-","");printf "%04d.%04d.%04d.%04d", $1, $2, $3, $4}')" && \ (mount -o ro $c /tmp/apm-iso cp /tmp/apm-iso/sam/www/webtop/public/download/urxvpn.cab \ /tmp/apm-urxvpn/URXVPN.CAB-$version umount /tmp/apm-iso) done Check the files copied ls -al /tmp/apm-urxvpn Import each file either with tmsh or with GUI. We will cover how to import with tmsh below. If you prefer to do it with the GUI, more information abour how to do it can be found in K13423 You can use the following script to automatically import all files cd /tmp/apm-uxrvpn for f in URXVPN.CAB-* do printf "create sys file ifile $f source-path file:$(pwd)/$f\ncreate ltm ifile $f file-name $f\n" | tmsh done Save the new configuration tmsh -c “save sys config” Time to create the iRule when CLIENT_ACCEPTED { ACCESS::restrict_irule_events disable } when HTTP_REQUEST { set uri [HTTP::uri] set ua [HTTP::header "User-Agent"] if {$uri starts_with "/vdesk" || $uri starts_with "/pre"} { set version "" regexp -- {EdgeClient/(\d{4}\.\d{4}\.\d{4}\.\d{4})} $ua var version if {$version != ""} { table set -subtable vpn_client_ip_to_versions [IP::client_addr] $version 86400 86400 } else { log local0.debug "Unable to parse version from: $ua for IP: [IP::client_addr] URI: $uri" } } elseif {$uri == "/public/download/urxvpn.cab"} { set version "" regexp -- {EdgeClient/(\d{4}\.\d{4}\.\d{4}\.\d{4})} $ua var version if {$version == ""} { log local0.warning "Unable to parse version from: $ua, will search session table" set version [table lookup -subtable vpn_client_ip_to_versions [IP::client_addr]] log local0.warning "Version in table: $version" } if {$version == ""} { log local0.warning "Unable to find version session table" HTTP::respond 404 content "Missing version in request" "Content-Type" "text/plain" } else { set out "" catch { set out [ifile get "/Common/URXVPN.CAB-$version"] } if {$out == ""} { log local0.error "Didn't find urxvpn.cab file for Edge Client version: $version" HTTP::respond 404 content "Unable to find requested file for version $version\n" "Content-Type" "text/plain" } else { HTTP::respond 200 content $out "Content-Type" "application/vnd.ms-cab-compressed" } } } } Add the iRule to the APM Virtual Server Known Limitations If multiple clients with different versions of the Edge Client are behind the same IP address, they might download the wrong version. This is due to the fact that the client doesn't present the version when the request for the file urxvpn.cab reaches the iRule. This is why the iRule tries to store IP addresses based on the source IP address of other requests related to the VPN. More information about this problem can be found in K0001327351.4KViews4likes2Comments[Workaround]: Prevent iRule Managers to accidentally enter invalid characters into a Data Group
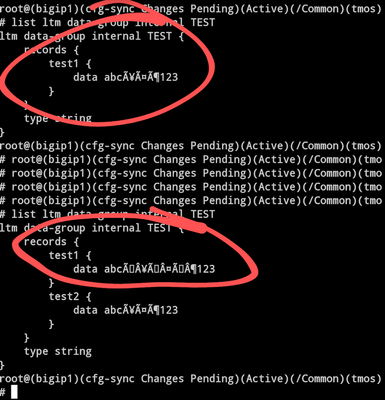
We realized some time ago that the BIG-IP GUI does not handle UTF-8 encoded strings very well in Data Groups which result in ever growing data records for everytime the Data Group is saved. This is an example on how to reproduce the problem and to see it in action: Start by creating an empty new data group named TEST of the type string. Add a line with the key test1 and the value abcåäö123 (copy and paste if you don't have a nordic keyboard) Click finish Check with tmsh list ltm data-group internal TEST You will see that it doesn't handle the UTF-8 data and you will se two characters for each > 7-bit character. Now go to the GUI again and add a second line with the key test2 and the same value abcåäö123 Click update Once again check tmsh and you will see that not only has test2 been added but test1 has also been updated, now including even more wrong characters. This is a screenshot of how it will look: The result of this is that eventually you will receive the following error from the BIG-IP (even if you only update lines that are not containing 8-bit ascii characters). Workaround Luckily we require the iRule Managers to login to an APM portal (webtop) where we have published a Portal Access to the administrative GUI of the BIG-IP, and since we do that, we can inject some JavaScript the will check the data before it saved. iRule PREVENT_INVALID_DATA_IN_DATAGROUP-IRULE This iRule will inject some JavaScript code that will prevent these mistakes from happening when HTTP_REQUEST { set inject_code 0 if {[HTTP::path] ends_with "/tmui/tmui/skins/Default/scripts/skin.js"} { set inject_code 1 STREAM::disable HTTP::header remove "Accept-Encoding" } } when HTTP_RESPONSE { if {$inject_code == 1} { set s1 "this.form.submitError\ =\ formSubmitError;" set r1 "this.form.submitError\ =\ formSubmitError;\n" append r1 "if\ (document.location.href.indexOf('datagroup')\ >\ -1)\ {\n" append r1 "select\ =\ document.getElementById('class_string_item');\n" append r1 "if\ (select\ !=\ null)\ {\n" append r1 "console.log('We\ found\ the\ select');\n" append r1 "for\ (option\ of\ select.children)\ {\n" append r1 "key\ =\ option.value.substr(0,\ option.value.indexOf('\\\\x0a'));\n" append r1 "if\ (!\ /^\[\\x00-\\x7F\]*\$/.test(key))\ {\n" append r1 "alert('String\ \"'+key+'\"\ contains\ invalid\ characters!');\n" append r1 "return\ false;\n" append r1 "}\n" append r1 "if\ (!\ /^\[\\x00-\\x7F\]*\$/.test(option.value))\ {\n" append r1 "alert('Value\ of\ \"'+key+'\"\ contains\ invalid\ characters!');\n" append r1 "return\ false;\n" append r1 "}\n" append r1 "}\n" append r1 "}\n" append r1 "}\n" STREAM::expression "@$s1@$r1@" STREAM::enable } } Now if you add a streaming profile to your APM Virtual Server and add this iRule the user will be presented with a popup informing them about the invalid data and also prevent them from submitting it. Hope this can be of help until F5 fixes this in the BIG-IP1.2KViews2likes1CommentOutbound iRule / BGP routing
Hey sirs, I would like to ask a question about the order of precedence/execute of a connection that consumes a forwarding virtual server/routing table. Currently, we have a forwarding any:0 virtual server, which load balances internet outgoing traffic through a pool_default_gateway that has the IP of 3 routers from different ISP associated with it, including some irules that make the SNAT decision based on LAN-segment. We are planning to include the F5 pair in the BGP neighbors of each ASN ISP and receive the default route and advertise the Virtual Server public IP. Does anyone know if the F5 when reads the dynamic routing table obtained via BGP, the traffic that is handled by the virtual servers of forwarding any:0, including those that are manipulated via iRule can show any kind of intermittence? thanks in advance526Views1like4CommentsGeolocation accept per url path
Hello team! i'm very new in iRule, and i need to understand if is possible to make an Irule that accept geolocation traffic from a specific URL path, for example : example.com/ (Accept traffic only from US) example.com/admin (Accept traffic only from US,AUS,BRA). Is there any way to do this rule via iRule ? Kind Regards!Solved704Views1like2CommentsiRule table usage in FLOW_INIT event
Hi, According tohttps://clouddocs.f5.com/api/irules/table.html table command is valid for all events except RULE_INIT Valid Events: ALL, exceptRULE_INIT I'm trying to use table command in FLOW_INIT event but always get empty value, while at CLIENT_ACCEPTED event the table return non empty value. when FLOW_INIT { set srcip [IP::client_addr] set test_ip [table lookup -subtable "blacklist" $srcip] log local0. "$srcip , table value: $test_ip" } log is "192.0.0.1 , table value: " while same code in CLIENT_ACCEPTED event when CLIENT_ACCEPTED{ set srcip [IP::client_addr] set test_ip [table lookup -subtable "blacklist" $srcip] log local0. "$srcip , table value: $test_ip" } log is "192.0.0.1 , table value: block" Thanks513Views1like1CommentClient-Certificate and IP-Whitelisting via Policy or iRule?
We have a requirement to verify for a valid client-certificate (not expired and issued from a trusted CA), but also accept a bypass if the source-IP is trusted. I have the following questions for the two different configuration options: Policy In the condition section for "SSL certificate" it says "common name with index", is this the number of the certificate (same as the iRule command "SSL::cert <index>")? Does this mean I can only verify the standard CN of it? In the documentation it's only mentioned "Inspects the properties of an SSL certificate", which sounds to me I can also verify e.g. issuer name, serial number of the issuer or expiration dates. So which value do I have to enter here? Or in other words, how can I check that the presented client-certificate is really issued from a trusted CA and not from a fake CA with the same CN? Assuming the first question can be answered positively, is it correct, that I simply create two rules based on "first match" to forward traffic (first rule for client-cert check, second rule for IP-whitelisting) and if none of the rules are matching, traffic will be blocked? Assuming above mentioned policy-setup is not possible, I would configure the client-cert check within an iRule. iRule Is the option "Trusted Certificate Authorities" from the clientSSL-profile used if I set "Client Certificate" to request? And if so, do I have to use any special iRule commands to do this? If the list of trusted CA from the clientSSL-profile can't be used within the iRule, which other commands best "simulate" this kind of check? I mean a string comparison for the issuer CN name is not a good option, because I can create my own CA, if I know the allowed CA-name. Is the serial number a better option? Or in other words, same question as above,how can I check that the presented client-certificate is really issued from a trusted CA and not from a fake CA with the same CN? The IP-whitelisting can be simply added in an else branch then, right? Thank you! Regards Stefan 🙂Solved1.8KViews1like7CommentsIs there Limitation of irule "virtual".. can we do it like this?
Hi We have BIG-IQ and BIG-IP AWAF. I see that BIG-IQ application dashboard is show only 1 application per virtual server. But in BIG-IP AWAF.. we config it as 1 virtual server 100 application (multi domain vip+use irule to check host header and send it to specific pool and choose specific waf policy) So we can't see each application metric in BIG-IQ.... This is our issue. I understand we need to config each vip for each application so BIG-IQ can retrive data from each vip per application but we can't use that many public ip. So I found that we have irule "virtual" which can send traffic to another virtual server. Can we do it like this? Instead of when HTTP_REQUEST { if {[HTTP::host] equals "abc.example.com"} { ASM::enable /Common/abc.example.com >>>> choose pool and waf policy by host header pool /External/Pool_abc.example.com } ------------------------------------ Change to when HTTP_REQUEST { if {[HTTP::host] equals "abc.example.com"} { virtual VS_abc.example.com >>> send it to private ip virtual server by host header which craete a new. } and in virtual server VS_abc.example.com we use private ip and assign pool and waf policy normally so we can add VS_abc.example.com in BIG-IQ application dashboard and see metric per application. But is there any limitation on how to use irule "virtual" like this? Is this practical?717Views1like3CommentsCreate a IFile {system level} via API - Powershell
Hi All, Attempting the following: 1: Create iFile system level 2: Update existing iRule-> iFile referance the the file uploaded in step 1. Im getting stuck at step 1, any assistance creatly apprecuated. What I have tried: Get Auth Token: # Get API token $big_ip = 'https://[REDACTED]' $url = "{0}{1}" -f $big_ip, '/mgmt/shared/authn/login' $body = @{ username = "[REDACTED]" password = '[REDACTED]' loginProviderName = "tmos" } | ConvertTo-Json $result = Invoke-RestMethod -Method 'POST' -Uri $url -ContentType 'application/json' -Body $body $token = $($result.token.token) Works. Next, Upload my file: $File_Name = 'MyFile' $File_Upload = 'C:\Temp\MyFile' $url = "{0}{1}{2}" -f $big_ip, "/mgmt/shared/file-transfer/uploads/", $File_Name $filelength = (Get-Item $File_Upload).length $headers = @{ 'Content-Type' = 'application/octet-stream' 'X-F5-Auth-Token' = $token 'Content-Range' = "0-$($filelength-1)/$filelength" } $result = Invoke-RestMethod -Method Post -Uri $url -Headers $headers -InFile $File_Upload Works fine too I am returned with: remainingByteCount : 0 usedChunks : @{0=46321} totalByteCount : 46321 localFilePath : /var/config/rest/downloads/MyFile temporaryFilePath : /var/config/rest/downloads/tmp/MyFile generation : 0 lastUpdateMicros : 1661257236246203 Next is where im stuck, creation of the iFile system level from the uploaded file. Ive re-typed the below from the Curl samples here:Syncing local repositories and ifiles using iContr... - DevCentral (f5.com) ### Create a iFile {system level} - does not yet work $File_Name = 'MyFile' $url = "{0}{1}{2}" -f $big_ip, "/mgmt/tm/sys/file/ifile/", $File_Name $headers = @{ 'Content-Type' = 'application/json' 'X-F5-Auth-Token' = $token } $body = @{ 'name' = $File_Name 'source-path' = "file:///var/config/rest/downloads/$File_Name" } | ConvertTo-Json $result = Invoke-RestMethod -Method put -Uri $url -Headers $headers -Body $body Next I am recieving that the file cannot be found. So this query is incorrectly tructured ? Translated these examples to powershell: Syncing local repositories and ifiles using iContr... - DevCentral (f5.com) Invoke-RestMethod : {"code":404,"message":"01020036:3: The requested iFile (/Common/MyFile) was not found.","errorStack":[],"apiError":3} At line:1 char:11 + $result = Invoke-RestMethod -Method put -Uri $url -Headers $headers - ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidOperation: (System.Net.HttpWebRequest:HttpWebRequest) [Invoke-RestMethod], WebException + FullyQualifiedErrorId : WebCmdletWebResponseException,Microsoft.PowerShell.Commands.InvokeRestMethodCommand Any assistance appreated with the above & next up updating the iRule file refence.Solved1.9KViews1like10CommentsIssues to forward requests with 'start with' due to similar contexts under same domain
Hi everybody, A network request that seemed to be simple is giving some trouble to our network team, I'd appreciate some help. Here's a summary of the rules to be put in place: 1) example.domain.com/cali --> forward to server1 2) example.domain.com --> forward to server2 When creating the rule with "URI starts with" from web interface it works, but there's a side effect: requests like example.domain.com/california are matching rule 1) and therefore failing, since that context is managed by some Apache at server2. They've tried using 'IS' instead 'STARTS WITH' for /cali but then, when trailing slash is not added, it fails. It also fails when calling something like /cali/ad Since we don't know what other possible contexts might be requested, we want just to add a rule for /cali and leave everything else (/california , /calisthenics, ...) under rule 2) What's the issue here? Is something like it possible just using the web interface or are iRules needed? Any examples? Thanks a lot in advanceSolved2KViews1like4Comments