APM with EntraID as idP / request signed
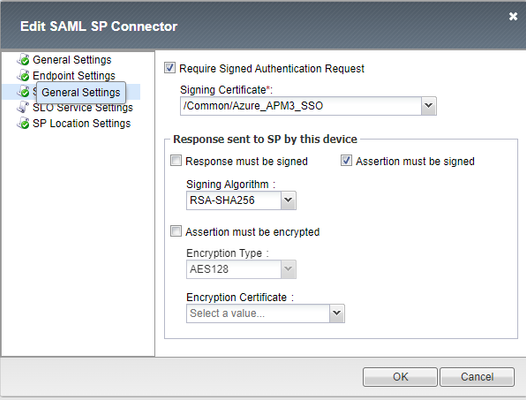
Hi experts. I need your help to solve an issue. I'm configuring a new enviroment with BIG-IP version 15.1.8.2 Build 0.0.17 Point Release 2. I have the APM works fine with SSO using EntraID (AzureAD) as idP. Now, I need to enable the request signed (Enforce signed SAML authentication requests - Microsoft Entra ID | Microsoft Learn). I generated the self signed certificate and import it on my app at Azure and my BIG-IP. I changed my config in Access > Federation > SAML Identity Provider and assigned my self signed certificate (pk included) to assign the request. But, I've received the below error by EntraID: Sign-in error code: 76021 Failure reason: The request sent by client is not signed while the application requires signed requests All attemps was made by browser (SSL VPN). Thank you.47Views0likes1CommentSAML issue with SimpleSAMLphp as IdP, BIG-IP as SP
have been trying to get SAML working, simpleSAMLphp as IdP and BIG-IP as SP. i believe it works up to the point where the IdP sends its auth succesfull data to the SP, once recieved by the SP i get this error: SAML Agent: /Common/saml_act_saml_auth_ag failed to parse assertion, error: Canonicalization of SignedInfo not sure how to continue from there, so many options and so little information on their exact effect. i built the setup as follows, virtual server with access profile with just start --> SAML auth --> Allow, BIGIP as SP profile with an IdP connection based on uri /, created IdP connection based on metadata from IdP. turned off as many signed and secure options as possible, just testing now, will add later on. anyone here that has setup BIG-IP as SP succesfully with SimpleSAMLphp? can you share some experience?552Views0likes7CommentsSAML SP ACS Post back resulting in a 404
Hello, I have one application configured to use APM via SAML authentication, the SP & IdP are both running directly on our F5 - this setup is working for many applications only for this one i have problems with the SAML flow. So only some web ressources from this app are protected, we used here an iRule in order to handle this, when i access one of the protected URIs i will be redirected to our IdP in order to get the authentication (KRB Ticket), this is still working i get a session for it (Allowed state) and see also the correct SP in the reference. But the bost pack from Idp to the SP to the ACS /saml/sp/profile/post/acs is resulting in a 404 Accessing protected web ressource -> www.app1.com/protected No session right now so i will be redirected to Idp -> idp.com/saml/idp/profile/redirectorpost/sso (Post; State 302) Redirect back to SP -> www.app1.com/saml/sp/profile/post/acs (Post; State 404) Anybody an idea how to solve this or where i can start with the error search? Thanks, ChristophSolved2KViews0likes4CommentsF5 APM Single IdP for Multiple SP's (Redirect External VIP to Internal VS's)
Hey there F5 community, I've been trying to wrap my head around this one to see if it is possible, and may be looking at this under the wrong light... We are trying to setup an environment such as idp.domain.com (Externally Available) and be able to route to internal only VIP's/Virtual Servers from it and utilize the Access Policy that resides on whatever virtual server it is redirected to, and handle SAML 2.0 communication policy's from there. We've created internal only VIP's and VS's for each separate SAML service policy and SP Connectors. We have successfully got them working independently when those VIPs were externally available. However we are looking to consolidate and have a single entry point for SP Initiated Connections, then redirect to the Virtual Server bound for each separate SP, and utilize the policy attached to the internal only VS's. I've attempted a few different iRule's that I have seen listed on the board here with very similar requests, but no luck yet. I am unable to bypass the initial policy of idp.domain.com and redirect to the internal only VS. Example: SP Initiated to DNS Pointing app1.domain.com to same External VIP as idp.domain.com app1.corp.domain.com name of Internal VS with Policy, Bound with SP Connector and has own APM Policy when HTTP_REQUEST { switch [string tolower [HTTP::host]] { "app1.domain.com" { virtual app1.corp.domain.com } "app2.domain.com" { virtual app2.corp.domain.com } } } Since it is landing on the External Available VIP for VS idp.domain.com, it is trying to process that policy without redirecting to the true end point VS of app1.corp.domain.com I'm not sure if idp.domain.com needs to have no policy constraints, or if something perhaps in the swap host syntax that doesn't like the "app1.domain.com" { virtual app1.corp.domain.com } Periods in the actual Virtual Server name or something of that sort. Most time I've seen any VS referenced, I noticed everyone seems to use underscores, of course this is after we've previously built out separately with actual names. So I'm not sure if that causes syntax issues. By chance does anyone have any recommendations? Thanks!718Views0likes7CommentsF5 as IDP & SAML Service Provider with multiple ACS Bindings
Version: 11.5.1 HF7 (LTM + APM) Anyone out there using F5 as IDP with a SAML service provider which contains multiple ACS bindings (please find snippet below)? After import of metadata, I can only find one ACS URI in bigip.conf, so I doubt this may be a feature which is currently not supported continue ... continue ... Highly appreciate any feedback on that topic Thx271Views0likes1Commenttcl logic in SAML Attribute value field possible?
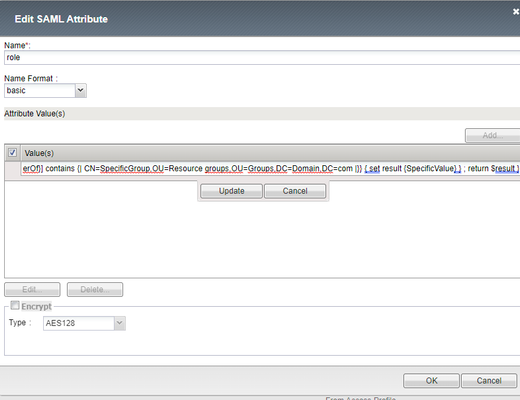
Hi. We're running BigIP as a SAML IDP. Can I somehow issue tcl logic in a SAML attributes? I'm talking about the Access ›› Federation : SAML Identity Provider : Local IdP Services, editing an object, under SAML Attributes. Based on what's in the memberOf attribute, I need to issue as a value either empty string or "SpecificValue". I am familiar with the %{session.variable} construct, but I don't want to clutter the session with more variables if I can avoid it, as that impacts all sessions using our IDP (30 or so federated services on the same VIP and AP). I tried these two approches: %{ set result {} ; if { [mcget {session.ad.last.attr.memberOf}] contains {| CN=SpecificGroup,OU=Resource groups,OU=Groups,DC=Domain,DC=com |}} { set result {SpecificValue} } ; return $result } expr { set result {} ; if { [mcget {session.ad.last.attr.memberOf}] contains {| CN=SpecificGroup,OU=Resource groups,OU=Groups,DC=Domain,DC=com |}} { set result {SpecificValue} } ; return $result } Expected result: An issued claim with the value "" or "SpecificValue" Actual result: An issued claim with the above code as the value As I mentioned, we've set it up using one VIP that is hosting 30 or so services. We're running 16.1.3.1. They are using the same SSO configuration and there's an iRule triggerd at ACCESS_POLICY_AGENT_EVENT, which does some magic to extract issuer and suchlike, and that helps to make decisions later in the Access Policy. It also populates a few session variables under the session.custom namespace for use in the Access Policy. Additional session variables are being populated in the Access Policy, such as resolved manager and their email address. I have looked briefly at the ASSERT::saml functions, but even if it would bepossible to manipulate that way, I wish to keep this set up as stream lined as possible and with as few new "special cases" in an iRule. So while I appreciate pointers along that route as well, I would first of all like to know if there is a way to do it natively in the SAML attribute value field. And if there are any options I have not yet explored here?862Views0likes5CommentsKeycloak as IDP for F5 APM via SAML
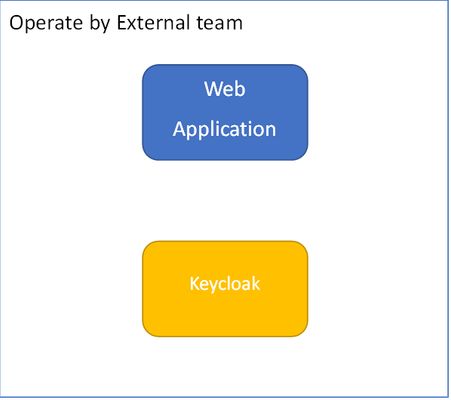
I have a requirement from our customer to do MFA authentication on F5 APM module and use Keycloak as Identity provider to control their access to web application. Since the keycloak is operate by different team, the internal operation team don’t have an authorize to do MFA on keycloak. They will use F5 APM to perform MFA instead. Existing environment. Solution Protect your web application by deploy F5 as web proxy. Configuration Import your SAML metadata to F5 APM Start by login to your keycloak console and downlond SAML metadata Make sure you have right realm selected. Save as you metadata Navigate to External IDP connector Create External IDP connector Upload your Metadata previously downloaded and name your SAML IDP connector Create your web.f5test.com certificate. Navigate to SSL Certificate list console Create your new certificate Configuration your parameter and click finish Create your Local SP Service Navigate to local SP service console Click create new SP service Input name, EntityID and SP name setting Config POST as assertion consumer service binding Configuration security setting with certificate generated earlier and click OK Binding your SP service with IDP connector Select your newly SP service created Add new row and select you IDP connector profile. Import your SP service to Keycloak Export your SP service Create new client on Keycloak Select file downloaded from previous section Click save3.2KViews0likes1CommentAPM - SAML Attributes Blank
Hello, I am working on implementing a SAML IDP, however I'm running into an issue where the SAML payload is not showing values for the attributes. Example: <saml2:AttributeStatement> <saml2:Attribute Name="uid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"></saml2:Attribute> <saml2:Attribute Name="email" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"></saml2:Attribute> <saml2:Attribute Name="displayname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"> <saml2:AttributeValue xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">email@email.com</saml2:AttributeValue> </saml2:Attribute> The attributes as defined in the IDP Config are: displayname = %{session.logon.last.logonname} email = %{session_logon_last_email} uid = %{session.ad.last.attr.sAMAccountName} What am I missing here?786Views0likes0CommentsF5 SAML as IdP - Architecture Question
In the case the F5 being the IdP for any cloud applications, user's request located on the cloud/internet can be redirected to edge F5 IdP that is facing the internet for authentication (usually this is a public IP address). This is understandable but from the architecture point of view, what is the best practice for the internal users located inside the company network? Do they need to be redirected to F5 located at the edge? Do they need tp resolve to that edge F5 public IP? or how the internal requests are handle when the F5 is acting as IdP for those cloud solutions (Office 365, etc) Thanks414Views0likes1CommentHow to create an APM policy for on-prem application that uses SAML
Hello, I would like some guide on how to configure and APM policy and SSO. Basicalli, present a portal to force authentication when accessing https://mysite.example.com for example https://mysite.example.com is an on-prem application which is configure for ADFS saml authentication on an external IdP. Before putting an APM policy the traffic flow goes as follows. User access https://mysite.example.com (this app is behind f5 LTM) mysite.example.com redirects user to authenticate to myadfs.example.com and gets prompted by ADFS for username and password. myadfs.example.com authenticates and redirects back to mysite.example.com User is able to access mysite.example.com. After adding APM policy the traffic flow goes as follows. User access https://mysite.example.com (this app is behind f5 LTM) F5 presents a prompt for username and password (AD authentication) User is successful authenticated. Access is granted to https://mysite.example.com mysite.example.com redirects user to authenticate to myadfs.example.com ("AGAIN", can this be prevented since they already authenticated) and gets prompted by ADFS for username and password. myadfs.example.com authenticates and redirects back to mysite.example.com User is able to access mysite.example.com. Any advice really appreciated. Python datetime (With Examples)433Views0likes1Comment