Power of tmsh commands using Ansible
Why is data important Having accurate data has become an integral part of decision making. The data could be for making simple decisions like purchasing the newest electronic gadget in the market or for complex decisions on what hardware and/or software platform works best for your highly demanding application which would provide the best user experience for your customer. In either case research and data collection becomes essential. Using what kind of F5 hardware and/or software in your environment follows the same principals where your IT team would require data to make the right decision. Data could vary from CPU, Throughput and/or Memory utilization etc. of your F5 gear. It could also be data just for a period of a day, a month or a year depending the application usage patterns. Ansible to the rescue Your environment could have 10's or maybe 100 or even 1000's of F5 BIG-IP's in your environment, manually logging into each one to gather data would be a highly inefficient method. One way which is a great and simple way could be to use Ansible as an automation framework to perform this task, relieving you to perform your other job functions. Let's take a look at some of the components needed to use Ansible. An inventory file in Ansible defines the hosts against which your playbook is going to run. Below is an example of a file defining F5 hosts which can be expanded to represent your 10'/100's or 1000's of BIG-IP's. Inventory file: 'inventory.yml' [f5] ltm01 password=admin server=10.192.73.xxx user=admin validate_certs=no server_port=443 ltm02 password=admin server=10.192.73.xxx user=admin validate_certs=no server_port=443 ltm03 password=admin server=10.192.73.xxx user=admin validate_certs=no server_port=443 ltm04 password=admin server=10.192.73.xxx user=admin validate_certs=no server_port=443 ltm05 password=admin server=10.192.73.xxx user=admin validate_certs=no server_port=443 A playbook defines the tasks that are going to be executed. In this playbook we are using the bigip_command module which can take as input any BIG-IP tmsh command and provide the output. Here we are going to use the tmsh commands to gather performance data from the BIG-IP's. The output from each of the BIG-IP's is going to be stored in a file that can be referenced after the playbook finished execution. Playbook: 'performance-data/yml' --- - name: Create empty file hosts: localhost gather_facts: false tasks: - name: Creating an empty file file: path: "./{{filename}}" state: touch - name: Gather stats using tmsh command hosts: f5 connection: local gather_facts: false serial: 1 tasks: - name: Gather performance stats bigip_command: provider: server: "{{server}}" user: "{{user}}" password: "{{password}}" server_port: "{{server_port}}" validate_certs: "{{validate_certs}}" commands: - show sys performance throughput historical - show sys performance system historical register: result - lineinfile: line: "\n###BIG-IP hostname => {{ inventory_hostname }} ###\n" insertafter: EOF dest: "./{{filename}}" - lineinfile: line: "{{ result.stdout_lines }}" insertafter: EOF dest: "./{{filename}}" - name: Format the file shell: cmd: sed 's/,/\n/g' ./{{filename}} > ./{{filename}}_formatted - pause: seconds: 10 - name: Delete file hosts: localhost gather_facts: false tasks: - name: Delete extra file created (delete file) file: path: ./{{filename}} state: absent Execution: The execution command will take as input the playbook name, the inventory file as well as the filename where the output will be stored. (There are different ways of defining and passing parameters to a playbook, below is one such example) ansible-playbook performance_data.yml -i inventory.yml --extra-vars "filename=perf_output" Snippet of expected output: ###BIG-IP hostname => ltm01 ### [['Sys::Performance Throughput' '-----------------------------------------------------------------------' 'Throughput(bits)(bits/sec)Current3 hrs24 hrs7 days30 days' '-----------------------------------------------------------------------' 'Service223.8K258.8K279.2K297.4K112.5K' 'In212.1K209.7K210.5K243.6K89.5K' 'Out21.4K21.0K21.1K57.4K30.1K' '' '-----------------------------------------------------------------------' 'SSL TransactionsCurrent3 hrs24 hrs7 days30 days' '-----------------------------------------------------------------------' 'SSL TPS00000' '' '-----------------------------------------------------------------------' 'Throughput(packets)(pkts/sec)Current3 hrs24 hrs7 days30 days' '-----------------------------------------------------------------------' 'Service7982836362' 'In4140403432' 'Out4140403234'] ['Sys::Performance System' '------------------------------------------------------------' 'System CPU Usage(%)Current3 hrs24 hrs7 days30 days' '------------------------------------------------------------' 'Utilization1718181817' '' '------------------------------------------------------------' 'Memory Used(%)Current3 hrs24 hrs7 days30 days' '------------------------------------------------------------' 'TMM Memory Used1010101010' 'Other Memory Used5555545453' 'Swap Used00000']] ###BIG-IP hostname => ltm02 ### [['Sys::Performance Throughput' '-----------------------------------------------------------------------' 'Throughput(bits)(bits/sec)Current3 hrs24 hrs7 days30 days' '-----------------------------------------------------------------------' 'Service202.3K258.7K279.2K297.4K112.5K' 'In190.8K209.7K210.5K243.6K89.5K' 'Out19.6K21.0K21.1K57.4K30.1K' '' '-----------------------------------------------------------------------' 'SSL TransactionsCurrent3 hrs24 hrs7 days30 days' '-----------------------------------------------------------------------' 'SSL TPS00000' '' '-----------------------------------------------------------------------' 'Throughput(packets)(pkts/sec)Current3 hrs24 hrs7 days30 days' '-----------------------------------------------------------------------' 'Service7782836362' 'In3940403432' 'Out3740403234'] ['Sys::Performance System' '------------------------------------------------------------' 'System CPU Usage(%)Current3 hrs24 hrs7 days30 days' '------------------------------------------------------------' 'Utilization2118181817' '' '------------------------------------------------------------' 'Memory Used(%)Current3 hrs24 hrs7 days30 days' '------------------------------------------------------------' 'TMM Memory Used1010101010' 'Other Memory Used5555545453' 'Swap Used00000']] The data obtained is historical data over a period of time. Sometimes it is also important to gather the peak usage of throughout/memory/cpu over time and not the average. Stay tuned as we will discuss on how to obtain that information in a upcoming article. Conclusion Use the output of the data to learn the traffic patterns and propose the most appropriate BIG-IP hardware/software in your environment. This could be data collected directly in your production environment or a staging environment, which would help you make the decision on what purchasing strategy gives you the most value from your BIG-IP's. For reference: https://www.f5.com/pdf/products/big-ip-local-traffic-manager-ds.pdf The above is one example of how you can get started with using Ansible and tmsh commands. Using this method you can potentially achieve close to 100% automation on the BIG-IP.11KViews4likes3CommentsWAFaaS with SSL Orchestrator
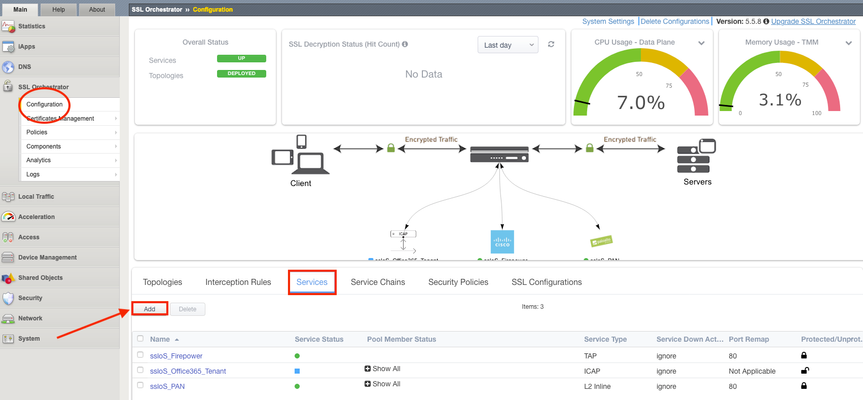
Introduction Note: This article applies to SSL Orchestrator versions prior to 11.0. If using version 11.0 refer to the articleHERE This use case allows you to insert F5 WAF functionality as a Service in the SSL Orchestrator inspection zone. WAFaaS is the ability to insert ASM profiles into the SSL Orchestrator Service Chain for Inbound Topologies.This configuration is specific to a WAF policy running on the SSL Orchestrator device.WAF and SSL Orchestrator consume significant CPU cycles so care should be given when deploying both together.It is also possible to deploy WAF as a service on a separate BIG-IP device, in which case you’d simply configure an inline transparent proxy service.The ability to insert F5’s WAF into the Service Chain presents a significant customer benefit. This guide assumes you already have WAF/ASM profile(s) configured, licensed and provisioned on BIG-IP and wish to add this functionality to an Inbound Topology.In order to run WAF and SSL Orchestrator on the same device you will need an LTM license with SSL Orchestrator as an add-on option.You cannot add a WAF license to an SSL Orchestrator stand-alone license. SSL Orchestrator does not directly support inserting F5 WAF policies into the Service Chain.However, the F5 platform is flexible enough to handle many custom use cases.In this case, the ICAP service configuration exposes a framework that is useful for any number of specialized patterns, including adding a WAF policy to an SSLO service chain.We will configure an ICAP Service and attach the WAF policy to it. Steps: Create ICAP Service Disable Strictness on the Service Disable TCP monitor for the ICAP Pool ICAP Adapt profiles removed from the Virtual Server Application Security Policy enabled and a Policy assigned under Security Step #1: Create ICAP Service Note: These instructions assume an SSL Orchestrator Topology and Service Chain are already deployed and working properly.These instructions simply add WAFaaS to the existing Service Chain.It is entirely possible to create the WAFaaS during the initial Topology creation, in which case you would create the service during the workflow, then make the necessary changes after the topology has been created. From the SSL Orchestrator Guided Configuration click Services then Add Scroll to the bottom, select Generic ICAP Service and click Add Give it a name, WAFaaS in this example For ICAP Devices click Add on the right Enter an IP Address, 198.19.97.1 in this example and click Done. Note:the IP address you use does not have to be the one above.It’s just a local, non-routable address used as a placeholder in the service definition.This IP address will not be used. IP addresses 198.19.97.0 to 198.19.97.255 are owned by network benchmark tests and located in private networks. Scroll to the bottom and click Save & Next. The next screen is the Services Chain List.Click the name of the Service Chain you wish to add WAF functionality to, ssloSC_ServiceChain in this example. Note: The order of the Services in the Selected column is the order in which SSL Orchestrator will pass decrypted data to the device.This can be an important consideration if you want some devices to see, or not see, the actions taken by the WAF Service. Select the WAFaaS Service and click the right arrow to move it to Selected.Click Save. Click Save & Next Click Deploy You should receive a Success message Step #2: Disable Strictness on the Service From the SSL Orchestrator Configuration screen select Services.Click the padlock to Unprotect Configuration. Note:Disabling Strictness on the ICAP Service is needed to modify it and attach the WAFaaS policy.Strictness must remain disabled on this service and disabling strictness on the service has no effect on any other part of the SSL Orchestrator configuration. Click OK to Unprotect the Configuration Step #3: Disable tcp monitor for the ICAP Pool From Local Traffic select Pools > Pool List Select the WAFaaS Pool Under Active Health Monitors select tcp and click >> to move it to Available.This removes the Pool’s Monitor because otherwise it would be marked as down or unavailable. Click Update Note:The Health Monitor needs to be removed because there is no actual ICAP service to monitor. Step #4: ICAP Adapt profiles removed from the Virtual Server From Local Traffic select Virtual Servers > Virtual Server List Locate the WAFaaS ICAP service that ends in “-t-4”virtual server and select it Set the Request Adapt Profile and Response Adapt Profile to None to disable the default ICAP Profiles Click Update Step #5: Application Security Policy enabled and a Policy assigned under Security For the WAFaaS-t-4 Virtual Server click the Security tab Set Application Security Policy to Enabled Select the Security Policy you wish to use.Click Update when done Note: In specific versions of SSL Orchestrator there is one extra configuration item that needs to be modified. This is NOT required in other versions. If this change is made, when performing an upgrade it is not necessarily required to back out this change. Required versions: SSLO version 5.9.15 available on TMOS 14.1.4 SSLO versions 6.0-6.5 available on TMOX 15.0.x Navigate to “Local Traffic››Profiles : Other : Service” Select the Service profile named “ssloS_WAFaaS-service” Change the “Type” from “ICAP” to “F5 Module” Conclusion The configuration is now complete.Using the WAFaaS this way is functionally the same as using it by itself.There are no known limitations to this configuration.2KViews5likes8CommentsOur Five Senses on Sensors
Aristotle (384 - 322 BC) is credited as the first person to classify our five sense organs: sight, smell, taste, touch, and hearing and Immanuel Kant, a famous philosopher from the 1700s said that our knowledge of the outside world depends on our modes of perception. Our highly developed organs of the eyes, ears, nose, tongue and the skin on your hand provide the sensing equipment necessary to send that information to the brain. In some cases, one of the sensors might not work properly in the case of the blind or deaf, yet the four other senses are heightened and exceed normal operation to make up for the missing information. Daniel Kish, for example, uses echolocation like a bat to see the imprint of the sound waves as they bounce back. Pretty cool, eh? Today, we're building gadgets that are used in conjunction with or completely taking over the the tasks of the eyes, ears, nose, tongue and hands. Things that were always part of our body are being replaced with micro-chipped things that act like, attach to - or better yet - integrate with our body. Sight: Of course there are security cameras to help us see our homes when we are away and most of us have heard of Google Glass but there are now eyeglasses being prototyped by BMW’s Mini division. They are combining the wearable with the connected car. These glasses communicate with the car via WiFi and offers a heads-up display like no other. While you can still see the real world, the glasses offer an overlay of speed, navigation, backup cameras and more. You can see just how close you are to the curb from the wheel's point of view. You can also look at a street sign and have it come to life with other overlays or additional info. While most of the data is just telemetry for now, engineers are looking to possibly incorporate driving features within the view. This is where IoT gets interesting - where one is used to compliment another. Also, Swiss engineers have developed a camera based on the human retina. Understanding the biology of the real thing, they've made a more efficient camera. Smell: Although there were attempts earlier, in the 1940-50's, Hans Laube created a system called Smell-O-Vision which would emit odors during the movie so the audience could smell what was happening in the movie. It was only used once. GE also developed a system in 1953 that they called Smell-O-Rama. Now you can get a smell app on your phone. ChatPerf is a thumb-drive-sized atomizer that plugs into your mobile device so it can be triggered to release specific odors on command. But those are scents out. Machines that can whiff stuff in have been around awhile. Think of your smoke, carbon-monoxide or radon detectors. Today we have wearable vapor sensors that can smell diabetes. Scientists have figured out how to use a sensor to identify the odor from melanoma to detect this form of skin cancer. Those human skin cells give off an odor that doctors can pick up with a sensor. And scientists in Israel who have already developed a nanotechnology breath analyzer for kidney failure are working on one that can distinguish between the breath of a lung cancer patient verses a healthy exhale. Crazy! Hearing: According to U.K. firm Wifore Consulting, Hearable technology alone will be a $5 billion market by 2018. Roughly the size of the entire wearable market today. Ears are able to capture things like oxygen levels, electrocardiograms, and body temperature. While sound drives the bulk of technology within this space, those ear buds could soon have technology that not only sends sounds but also captures some of your body information. And it is small enough and discrete to wear everywhere rather than carrying a mobile device. Initial uses trend with fitness. Ear buds that play music but also give you feedback on your workout. There are also smart earrings that monitor heart rate and activity. I've always said that there will come a time when we all have IPv6 chips in our ear and we'll just tug the lobe to answer a call. Carol Burnett would be proud. Touch: Want to give a robot the ability to feel? Done. Researchers have developed a flexible sensor able to detect temperature, pressure and humidity simultaneously and a big leap towards imitating the sensing features of the human skin. While still in the early stages, future sensors could be embedded into the "electronic skin" of prosthetics, allowing amputees sense environmental changes. Another is BioTac, a fingertip that can sense force, temperature, and vibration—in some cases better than a human finger. With laser 3D printing, some orthotics can be delivered in hours rather than months. Taste: Sweet, sour, salt and bitter used to be the domain of the tongue. Soon, electronic 'tongues' could be used to monitor the quality control of bottled water. Using chemical sensors, researchers in Texas have demonstrated that the electronic tongue can 'taste' different solutions. The sensors responded to different combinations of the four artificial taste elements with unique color combinations of red, green and blue. This enabled the device to analyze for several different chemical components simultaneously. I've written about smart chopsticks that can detect oils containing unsanitary levels of contamination, a fork that monitors how many bites you take and a smart cup that counts the amount and calories you drink. This is the Internet of Food. Wearables make technology personal and our five senses are what helps us navigate life, gives us perspective. Who would have thought that an individual's perspective would someday become embedded within coded software. ps Related: Wearables + Connected Cars = IoT Heaven Five ways retailers can start using IoT today Lesson: How Do Human Sensors Work? Hearables - the next big thing in wearable tech Human Touch: Sensor Lets Robots 'Feel' They've Got It Licked - Artificial Sensors Can Taste What's In A Complex Mixture Innovative Technology Powers the Wearables Movement My IoT Articles Technorati Tags: iot,wearables,senses,sensors,things,humans,hearables,sight,sound,smell,touch,taste,silva,f5 Connect with Peter: Connect with F5:1.6KViews0likes0Comments2022 DevCentral MVP Announcement
Congratulations to the 2022 DevCentral MVPs! Without users who take time from their busy days to share their experience and knowledge for others, DevCentral would be more of a corporate news site and not an actual user community. To that end, the DevCentral MVP Award is given annually to the outstanding group of individuals – the experts in the technical F5 user community who go out of their way to engage with the user community. The award is our way of recognizing their significant contributions, because while all of our users collectively make DevCentral one of the top community sites around and a valuable resource for everyone, MVPs regularly go above and beyond in assisting fellow F5 users.We understand that 2021 was difficult for everyone, and we are extra-grateful to this year's MVPs for going out of their ways to help others. MVPs get badges in their DevCentral profiles so everyone can see that they are recognized experts. This year’s MVPs will receive a glass award, certificate, exclusive thank-you gifts, and invitations to exclusive webinars and behind-the-scenes looks at things like roadmaps, new product sneak-previews, and innovative concepts in development. The 2022 DevCentral MVPs are: Aditya K Vlogs AlexBCT Amine_Kadimi Austin_Geraci Boneyard Daniel_Wolf Dario_Garrido David.burgoyne Donamato 01 Enes_Afsin_Al FrancisD iaine jaikumar_f5 Jim_Schwartzme1 JoshBecigneul JTLampe Kai Wilke Kees van den Bos Kevin_Davies Lionel Deval (Lidev) LouisK Mayur_Sutare Neeeewbie Niels_van_Sluis Nikoolayy1 P K Patrik_Jonsson Philip Jönsson Rob_Carr Rodolfo_Nützmann Rodrigo_Albuquerque Samstep SanjayP ScottE Sebastian Maniak Stefan_Klotz StephanManthey Tyler.Hatton1.2KViews8likes0CommentsIs 2015 Half Empty or Half Full?
With 2015 crossing the half way point, let's take a look at some technology trends thus far. Breaches: Well, many databases are half empty due to the continued rash of intrusions while the crooks are half full with our personal information. Data breaches are on a record pace this year and according to the Identity Theft Resource Center (ITRC), there have been 400 data incidents as of June 30, 2015. One more than this time last year. And, 117,576,693 records had been compromised. ITRC also noted a 85% increase in the number of breaches within the banking sector. From health care to government agencies to hotel chains to universities and even Major League Baseball, breaches and attacks are now a daily occurrence. Cloud: Who would've thought back in 2008 that this cloud thing would now be half full? Over the last couple years, the 'cloud' has become a very viable option for organizations large and small. It is becoming the platform for IoT and many organizations such as Google and GE are now moving critical corporate applications to the cloud. While hybrid is the new normal remember, The Cloud is Still just a Datacenter Somewhere. DNS: While IPv4 addresses are now completely empty, DNS seems to be half to almost full in 2015. DNS continues to be a target for attackers along with being an enabler for IoT. It is so important that Cisco recently acquired OpenDNS to help fight IoT attacks and the courts got a guilty plea from an Estonian man who altered DNS settings on infected PCs with the DNSChanger malware. I think of DNS as a silent sufferer - you really don't care about it until it doesn't work. Start caring this year. Internet: Full but still growing. As noted above, IPv4 addresses are gone. Asia, Europe, Latin America and now North America have run out of IPv4 addresses and have exhausted their supplies. If you're wondering how to handle this glass, F5 has some awesome 4to6 and 6to4 solutions. IoT: Things, sensors and actuators are all the buzz and are certainly half full for 2015. At this time last year, IoT was at the top of the Gartner Hype Cycle and it has certainly not disappointed. Stories abound about Internet of Things Security Risks and Challenges, 10 of the biggest IoT data generators, the Top 10 Worst Wearable Tech Devices So Far, The (Far-Flung) Future Of Wearables, along with the ability to Smell Virtual Environments and if We Need Universal Robot Rights, Ethics And Legislation. RoboEthics, that is. Mobile: We are mobile, our devices are mobile and the applications we access are now probably mobile also. Mobility, in all it's connotations, is a huge concern for enterprises and it'll only get worse as we start wearing our connected clothing to the office. The Digital Dress Code has emerged. Mobile is certainly half full and there is no empting it now. Privacy: At this point with all the surveillance, data breaches, gadgets gathering our daily data and our constant need to tell the world what we're doing every second, this is probably bone dry. Pardon, half empty, sticking to the theme. That's what I got so far and I'm sure 2015's second half will bring more amazement, questions and wonders. We'll do our year in reviews and predictions for 2016 as we all lament, where did 2015 go? There is that old notion that if you see a glass half full, you're an optimist and if you see it half empty you are a pessimist. Actually, you need to understand what the glass itself was before the question. Was it empty and filled half way or was it full and poured out? There's you answer! ps Related: It's all contained within the blog. Technorati Tags: f5,breach,security,cloud,dns,iot,mobile,2015,silva,empty or full Connect with Peter: Connect with F5:1KViews0likes2CommentsThe Analog Generation
From Baby Boomers to Gen X, Y, & Z, there are certain characteristics that define, at least according to demographers and historians, each generation. Generation X, specifically, might also remember a Rush song called The Analog Kid. While not as frequently played as Tom Sawyer or Subdivisions, it has always been my favorite Rush song. Driving bass, awesome guitar solo, amazing imagery and Peart. I am that Generation. The Analog Generation. With all of our digital things getting connected, including things on and in our body, I started thinking that I'm part of the generation that transitioned from analog to digital. Not that analog or analog signals are disappearing anytime soon, but as a kid, there were way more analog things than digital, that's for sure. Audiophiles will also argue that analog recordings are better at capturing the true representation of sound due to it being continuous, rather than specific values to represent sound, as in the discrete digital. I wondered if I was the only one who figured this out - highly doubtful - so I searched. And actually, there are a few people who have made the connection. One who argues that today's kids, at least his kids, are very analog. They love playing outside, playing board games and other non-digital activities. He talks about the importance of parents giving their children attention in the real world. And the other one specifically talks about the analog things we remember as a kid - records, 8mm, rotary phones, black & white TV, VHS and others verses the CDs, DVDs, iPhones and HD TVs today's kids live with. Some feel that Rush's The Analog Kid is about a more innocent time with less technology in the world, longing for the simpler days. A cautionary tale. One person notes, 'Perhaps Peart's social comment with the two songs is how technology and science creates incredible wonders, but there's a cruel price to pay if there's no heart to guide it.' The other song he references is Digital Man, also on the Signals album. When I hear The Analog Kid it immediately takes me back to 1982 and whatever I was doing in high school. It is interesting that I took my first computer class in high school around that time...while still learning how to type...on a real typewriter. If you remember those, with the little IBM ball to change fonts, you're analog. The last lines of the song are: Too many hands on my time Too many feelings Too many things on my mind When I leave I don't know What I'm hoping to find When I leave I don't know What I'm leaving behind... We are certainly entering a new realm with IoT with a lot of hopes, dreams and ideas of things to come. And while they all might help us automatically adjust home temperatures, become a little healthier, auto drive our car, keep an eye on our home, and cook better dinners, we can't forget that humans are social creatures, not necessarily social media darlings, and our real family, friends and loves are what really matter. We're already forging a new frontier but we must tread carefully. ps Related The Analog Generation Analog vs. Digital Generations Is IoT Hype For Real? Internet of Things OWASP Top 10 The Top 10, Top 10 Predictions for 2015 OK 2015, Now What? The Digital Dress Code Welcome to the The Phygital World Technorati Tags: f5,analog,digital,rush,music,the analog kid,iot,things,sensors,humans,society,generations,silva Connect with Peter: Connect with F5:916Views0likes0CommentsIntelligent DNS Animated Whiteboard
DNS will become even more important as additional sensors, monitors, actuators and other 'things' connect to the internet. It helps those devices like refrigerators and automobiles get their updates and helps us people find those things in our digital world. Here is a short Whiteboard explaining how F5 can help solve DNS challenges. And check out our Intelligent DNS Scale Reference Architecture which delivers the peace of mind that comes with knowing that your web applications will respond to all DNS queries—keeping your content and applications available to your users wherever and whenever they want to access them. ps Related CloudExpo 2014: The DNS of Things GartnerDC 2013: Intelligent DNS Scale Reference Architecture The DNS of Things DNS Does the Job A Living Architecture Technorati Tags: dns,f5,iot,things,reference architecture,availability,silva Connect with Peter: Connect with F5:759Views0likes0CommentsProtecting Beyond DNS Flood & DDoS
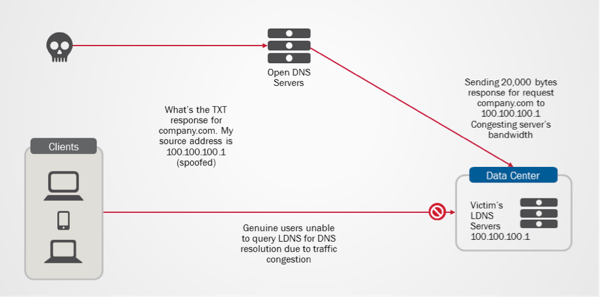
The recent slate of cyber-attacks involving DNS and NTP systems has again prompted questions about the comprehensiveness of DNS infrastructure’s security protection. Besides mitigating volumetric attacks such as DNS flood & DDoS, many organizations have realized the need for a more comprehensive DNS security protection, which helps in preventing DNS-related security frauds and non-volumetric based attacks such as amplification and cache poisoning attacks. On DNS Amplification & DNS Reflection Attacks You might concur that increasing DNS performance with adequate DNS rate limiting mechanism is probably one of the best approaches to tackle the problem of overwhelming DNS traffic and DNS DoS attacks. However, this does not address the issue of DNS Amplification and DNS reflection attacks, which has been made popular through the Spamhaus-Cyberbunker attack incident. In this incident, CyberBunker took the advantage of open DNS resolvers to launch DNS amplification attacks, causing Spamhaus to be unreachable at times. DNS amplification and reflection attacks are typically sent to DNS servers as legitimate DNS request, in hope to receive large data size responses. The huge data size responses will eventually use up all the available bandwidth causing congestion to genuine DNS queries and responses. As such, DNS query rate limiting mechanism and higher QPS performance will not be able to counter the attack since the attacks typically come in small numbers of DNS requests. One of the ways to limit such attacks is to filter the request based on query type. Typically, DNS amplification and reflection attacks will request for ‘TXT’ or ‘ANY’ Query Type which tends to return responses with significant data size. By applying bandwidth rate limit to these query type request and large-data-size query responses, we will be able to prevent bandwidth congestion caused by these attacks. Worried about the complexity of the bandwidth rate limiting solution? Well, it only takes less than 10 lines of iRules (shown as below) on F5 DNS platform to get this enforced and implemented. when DNS_REQUEST { if { ([DNS::question type] eq "TXT") } { rateclass dns_rate_shape } } when DNS_RESPONSE { if { ([DNS::len] value > 512) } { rateclass dns_rate_shape } } Diagram 1: DNS Reflection attacks blocking genuine users from accessing LDNS server. Cache Poisoning Attacks DNSSEC is poised as the eventual and ultimate solution to counter DNS cache poisoning attacks. Though the adoption rate of DNSSEC is encouraging, it takes all parties to deploy DNSSEC signing and validation to fully protect against cache poisoning. While waiting for DNSSEC adoption rate to mature, is there any interim solution to reduce or prevent cache poisoning attacks? Based on DNS RFC standards, name servers are required to treat domain names request with case-insensitivity. In other words, the names www.foo.com and WWW.FOO.COM should resolve to the same IP address. However, most name servers will preserve the original case when echoing back the domain name in the response. Hence, by randomly varying the case of characters in domain names queried, we will be able to add entropy to requests. With this verification mechanism, the name server response must match the exact upper and lower case of every character in the name string; for instance, wWw.f5.CoM or WwW.f5.COm, which significantly reduces the success rate of cache poisoning attacks. With F5’s DNS solution, this mechanism can be enabled with just a check box on the management pane. The packet capture of the query case randomization process by F5 DNS is shown as below. As depicted in the diagram, for queries to www.google.com, F5 Cache DNS will randomize the character case of the query prior sending the query to Google’s authoritative DNS server. This greatly reduces the chances of unsolicited queries matching the domain name and DNS request transaction ID, which causes the poisoning of cached DNS records. Diagram 2: Character case randomizer in F5 DNS solution dramatically reduces the possibilities of DNS cache poisoning attacks DNS is among the hoariest of internet services that is still widely used today. Its usage continues to grow due to its simplicity and proliferation of smart devices. Hence, it is truly important that proper solution design and architecture approach are being put in place to protect the infrastructure. After all, the protection investment might be only a fraction of what you are paying for during an attack.635Views0likes5CommentsBIG-IP Edge Client v1.0.6 for iOS 7
With all your other iOS 7 updates (if you've made the plunge), if you are running the BIG-IP Edge Client on your iPhone, iPod or iPad, you may have gotten an AppStore alert for an update. If not, I just wanted to let you know that version 1.0.6 of the iOS Edge Client is available at the AppStore with iOS 7 support. Customers who use UDID in their access policies should have users update to this version. The BIG-IP Edge Client application from F5 Networks secures and accelerates mobile device access to enterprise networks and applications using SSL VPN and optimization technologies. Access is provided as part of an enterprise deployment of F5 BIG-IP Access Policy Manager, Edge Gateway, or FirePass SSL-VPN solutions. BIG-IP Edge Client for iOS Features: Provides accelerated mobile access when used with F5 BIG-IP Edge Gateway. Automatically roams between networks to stay connected on the go. Full Layer 3 network access to all your enterprise applications and files. ps Related: Manual: BIG-IP Edge Apps Client Compatibility Matrix BIG-IP Edge Client and BIG-IP Edge Portal for Apple iOS and Android software support policy Release Note: BIG-IP Edge Client for iOS 1.0.6 Advanced Edge Client Installation for Windows–The Mysteries of Windows Installer Revealed F5 BIG-IP Edge Client F5 BIG-IP Edge Portal F5 BIG-IP Edge Client for Android Technorati Tags: f5,big-ip,edge client,ssl-vpn,mobile,smartphone,ios7,apple,iphone,ipad,silva,remote access,security,secure access,apm Connect with Peter: Connect with F5:601Views0likes1CommentIs IoT Hype For Real?
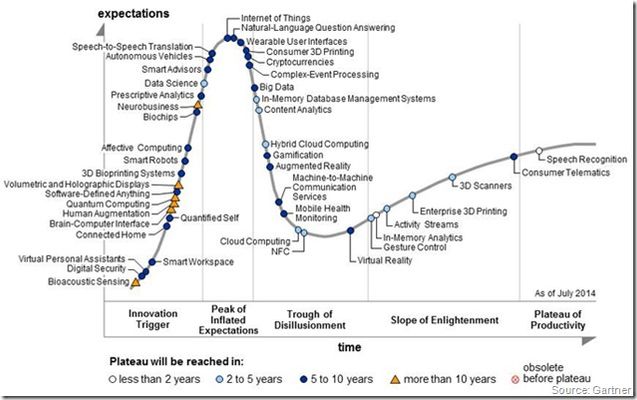
It is only fitting that the 20th anniversary of the Gartner Hype Cycle has the Internet of Things right at the top of the coaster. IoT is currently at the peak of Inflated Expectations. The Gartner Hype Cycle give organizations an assessment of the maturity, business benefit and future direction of more than 2,000 technologies. The theme for this year's Emerging Technologies Hype Cycle is Digital Business. As you can see, being at the top really means that there is a ton of media coverage about the technology, so much so that it starts to get a little silly. Everyone is talking about it, including this author. What you can also so is the downward trend to follow. This is the trough of disillusionment. Gamification, Mobile Health Monitoring and Big Data all fall into this area. It means that they already hit their big hype point but doesn't necessarily mean that it's over. The slope of enlightenment shows technologies that are finally mature enough to actually have reasonable expectations about. Each of the technologies also have a time line of when it'll mature. For IoT, it looks like 5 to 10 years. So while we're hearing all the noise about IoT now, society probably won't be fully immersed for another decade...even though we'll see gradual steps toward it over the next few years. Once all our people, places and things are connected, you can also get a sense of what else is coming in the Innovation Trigger area. Come the 2025 time frame, things like Smart Robots, Human Augmentation and a Brain Computer Interface could be the headlines of the day. Just imagine, instead of having to type this blog out on a keyboard, I could simply (and wirelessly) connect my brain chip to the computer and just think this. Hey, Stop reading my mind!! ps Related: Gartner's 2014 Hype Cycle for Emerging Technologies Maps the Journey to Digital Business Chart of the Week: The hype cycle of emerging technologies The Internet of Things and DNS F5 Predicts: Internet of Things Drives Demand for 'Social Intelligence' Internet of Things OWASP Top 10 The Icebox Cometh Technorati Tags: iot,things,sensors,nouns,gartner,hypecycle,media,silva,f5598Views0likes0Comments