BigIP APM Oauth - set to 'Failed to perform curl: Failure when receiving data from the peer'
We've been dealing with a issue when an Oath token is sent to Azure for authentication using XXX.session.oauth.client.last.auth_redirect: login.windows.net/XXXXX/XXXX session.oauth.client.last.auth_resule 0 We are constantly seeing the error and causing out Oath Client to be denied. We are able to perform a "discover" in the Provider and able to "dig" to the Azure Enterprise.Our DNS Resolver is able to resolve DNS as per guide. Has anybody come across this and can point us in the right direction? The only way we can make is work is to change the APM policy to "fallback" Allow OAuthClientToAzureAD_act_oauth_client_ag: OAuth Client: failed for server '/DC-TEST/Azure_Oauth_Server' using 'authorization_code' grant type (client_id=XXXXXXXXXXXXXXXX), error: Failed to perform curl: Failure when receiving data from the peer Session variable 'session.oauth.client./DC-TEST/OAuthClientToAzureAD_act_oauth_client_ag.authresult' set to '0' Session variable 'session.oauth.client./DC-TEST/OAuthClientToAzureAD_act_oauth_client_ag.errMsg' set to 'Failed to perform curl: Failure when receiving data from the peer Session variable 'session.oauth.client.last.authresult' set to '0' OAuthClientToAzureAD_act_oauth_client_ag: OAuth: Request parameter 'client_secret=********'OAuthClientToAzureAD_act_oauth_client_ag: OAuth: Request parameter 'grant_type=authorization_code' OAuthClientToAzureAD_act_oauth_client_ag: OAuth: Request parameter 'redirect_uri=https://our.test.website.com/oauth/client/redirect OAuthClientToAzureAD_act_oauth_client_ag: OAuth: Request parameter 'code=********' OAuthClientToAzureAD_act_oauth_client_ag: OAuth Client: failed for server '/DC-TEST/Azure_Oauth_Server' using 'authorization_code' grant type (client_id=XXXXXXXXXXXXXXX), error: Failed to perform curl: Failure when receiving data from the peer If we change the Access Policy "fallback" to "Allow" the user is then allowed to reach the backend application but would have otherwise been denied. It seem during the Oauth Client process the token request is rejected Previously we were seeing the error below which we resolved by making sure the DNS resolver could resolve DNS correctly. OAuthClientToAzureAD_act_oauth_client_ag: OAuth Client: failed for server '/DC-TEST/AzureAD_Server' using 'authorization_code' grant type (client_id=d7b3f856-6053-462b-a8f3-c2820e2a4c6c), error: HTTP error 503, DNS lookup failed731Views0likes5CommentsAPM HTTP auth - POST
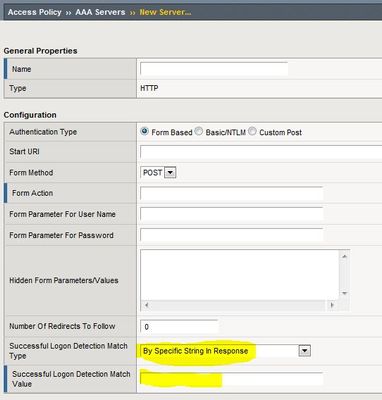
with APM, I need to build the following flow - user logs on APM logon page, credentials are validated with LDAP auth - those credentials are sent to an existing auth webserver, with a POST (HTTP auth) - that auth webserver replies with the same username (as the one sent in the form) if authorized Question: can we use session variable in the "Successful Logon detection match value" field, as we look for "specific string in response"? Anyone successfully implemented that?174Views0likes0CommentsNTLM Machine Account Issues - APM
Good afternoon - I am hoping someone can point me in the right direction. I'm trying to use the iApp to deploy RDP Gateway using APM (using this template - ). Part of the config is to create a new NTLM Machine account. I had no issues creating the account - and the iApp deployment went swimmingly well. I also verified that the machine account showed up in AD as a computer account. However, I am seeing these errors in the APM logs: May 15 17:40:32 f5lab debug nlad[6379]: 01620000:7: <0x56900b70> nlclnt[2a8e2c794]: is now initializing. May 15 17:40:32 f5lab debug nlad[6379]: 01620000:7: <0x56900b70> NLAD_TRACE: cli_full_connection(output_cli = (nil), my_name = "F5LAB", dest_host = "domaincontroller.domain.local", port = 445, service = "IPC$", service_type = "IPC", user = "F5LAB$", domain = "DOMAIN") May 15 17:40:32 f5lab debug nlad[6379]: 01620000:7: <0x56900b70> NLAD_TRACE: cli_full_connection(output_cli = (nil)) = 0xC000006D May 15 17:40:32 f5lab err nlad[6379]: 01620000:3: <0x56900b70> nlclnt[2a8e2c794] init: Error [0xc000006d,NT_STATUS_LOGON_FAILURE] connecting to DC 10.11.12.13 I also cannot renew the NTLM account password from the GUI as I get this error: Could not connect to domain domain controller of realm 'domain.local' machine account update for 'f5lab' failed: Preauthentication failed, principal name: f5lab@domain.local. Invalid user credentials. (-1765328360) I'm running on 12.1.3.4 and have tried the following: Recreated the NTLM account, multiple times. I know I have permissions as the account does show up in AD, and I do have domain admin level permissions Restarted the eca service (bigstart restart eca) Restarted the nlad service (bigstart restart nlad) Restarted the F5 appliance itself. Verified that the DNS settings are configured properly. The F5 is able to resolve the domain controller IP from the alias. No firewall exists between this F5 and the domain controller. Has anyone seen this and if so - can anyone point me in the right direction? I thought I'd try here before opening a support ticket with F5.470Views0likes4CommentsOutlook Anywhere and NTLM authentication
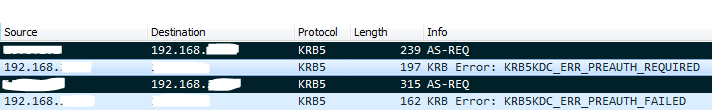
Hello, I am trying to achieve Outlook Anywhere with basic-NTLM and Kerberos SSO. I followed the DG and am stucked at NTLM authentication. When I create the NTLM Machine Account the logs say that it joined the domain, then I create the NTLM Auth Configuration with my domain and DCs. After that I see this messages in the logs: nlad[11851]: 01620000:3: <0x2b3374f71700> nlclnt[12a02a8c0] init: Error [0xc000006d,NT_STATUS_LOGON_FAILURE] connecting to DC 192.168. I added some Exchange groups to the machine account and enabled delegation for http with Exchange servers. I then try to renew machine account password but I have this error: adutil[16625]: 01490274:5: (null):Common:00000000: New master key received. adutil[16625]: 01490200:3: ERROR: Could not connect to domain domain controller of realm 'EXAMPLE.AD' adutil[16625]: 01490200:3: WARNING: machine account update for 'f5apm' failed: Preauthentication failed, principal name: f5apm@EXAMPLE.AD. Invalid user credentials. (-1765328360) Then I took a look at Kerberos trafic and could see that the bigip can't get a Kerberos ticket: At this step I am not even talking about Kerberos SSO which I think has nothing to do with NTLM. I have found K33692321 but it doesn't help. I also took a look at K08915521. It says that it may be a domain name or NetBIOS name issue but I know that my domain is EXAMPLE.AD and NetBIOS EXAMPLE. Does someone already managed to make this work ? It is a standard configuration so am I missing something Windows side ? Best regards443Views0likes0CommentsECA plugin documentation in the wiki
I'm running 11.4.1 and trying to figure out NTLM auth. I'm following a guide I found on devcentral but it's not working for me. I see there's a plugin ECA that enables NTLM authentication, however the documentation is...well, not present. The Wiki says that 11.3.0 introduced "ECA::metadata" however when I try using that in my iRule I get a syntax error: 01070151:3: Rule [/XXX/ntlm-auth-iRule] error: /XXX/ntlm-auth-iRule:44: error: [undefined procedure: ECA::metadata][ECA::metadata select_ntlm:$static::ntlm_config] So apparently ECA::select works - by which I mean that I get no errors when I save the iRule. However, the iRule is not working. I am having a hard time troubleshooting because ECA is such a black box.390Views0likes5CommentsFreeradius auth for LTM V11.5.1
Guys am running out of inspiration here and hoping you may be able to help. I have set up a FreeRadius server which is successfully authenticating Linux systems and Cisco devices. I have added the config for F5 to the radius server and verified it's triggering correctly for my test user. e.g. (radiusd log extract) Mon Feb 22 14:39:35 2016 : Debug: rlm_perl: Added pair Auth-Type = PAP Mon Feb 22 14:39:35 2016 : Info: ++[perl] = ok Mon Feb 22 14:39:35 2016 : Info: +} group post-auth = ok Sending Access-Accept of id 161 to 192.168.1.90 port 27260 Cisco-AVPair = "shell:priv-lvl=15" F5-LTM-User-Shell = "tmsh" F5-LTM-User-Info-1 = "F5-admin" F5-LTM-User-Role = Administrator F5-LTM-User-Partition = "Common" Mon Feb 22 14:39:35 2016 : Info: Finished request 25. I've then followed the recipe at https://support.f5.com/kb/en-us/solutions/public/14000/300/sol14324.html and believe I have things set right. tmsh sows this when list the auth section: auth radius system-auth { servers { system_auth_name1 } } auth radius-server system_auth_name1 { secret $M$q5$0UFrYg9zh5kLp7xkZOb2vZpgAPggyDPoWmjeIgF5F1I= server 192.168.1.56 } auth remote-role { role-info { F5-admin { attribute F5-LTM-User-Info-1=F5-admin console %F5-LTM-User-Shell line-order 1001 role %F5-LTM-User-Role user-partition %F5-LTM-User-Partition } } } Trying to log in as my test user sadly yields no good outcome, in spite of the the log from the radius server showing it sending an Access-Accept packet with the relevant F5 attributes included. So I guess my question is if there is log file I've been unable to find on the LTM itself which might let me know what I'm doing wrong. This or any other thoughts would be greatly appreciated. Enno.315Views0likes1CommentUsing OpenID Connect to authenticate users
Hello all, I want to use OpenID Connect to authenticate my users before gaining access to one of my application. I want to use my bigip as OpenID Provider (ie: the entity that authenticate the users) . My issue is the following: The OpendID provider (my bigip) never provides me with a ID Token. All I have is an “Access Token” and a “Refresh Token” but no “ID Token”. Below is a description of my lab: resource owner: ip address 10.10.255.1 bigip OpenID Provider: virtual server ip 10.10.255.221 (see below for the access policy) *The agents are left with their default values. Client: I user openid debugger (https://oidcdebugger.com/) in order to request the authorization code. Then I request the Tokens using an html code. I do the following for testing : I request the authorization code from the authorization server (ie my virtual server) . For this I use openID Connect debugger to construct the request for me. Here is the request that I send : ? client_id=e1111098ccff5f81859f9fc83eaa000c29267803efc0bb5b & redirect_uri=https://oidcdebugger.com/debug & scope=openid myscope & response_type=code & response_mode=form_post & state=toto & nonce=7r8saarltr After sending this request I enter my credentials (in the logon agent), I click on authorize then the virtual server correctly redirects me to: https://oidcdebugger.com/debug code=cae85f6fd33c6b27f56f536b6fd9af2ca0fc78e69ac3d13799533c143b38b4ac&state=toto” I now have a correct authorization code that I can exchange for an “access token” AND a “ID Token” . I then send a POST to get the access and ID Tokens using the following HTML code : *note the presence of the “openid” in the scope parameter. However, this is what I get from the authorization server (see in the comment) : -> I have No “ID TOKEN” ☹ Could you please help me configure my access policy so that it supports OpenID Connect and sends me an “ID Token” ??2.7KViews0likes8CommentsLTM :: SSL Client Authentication :: Lock Out
Has anybody implemented any controls on their LTMs that prohibits a source from repeatedly authenticating to a virtual server that requires SSL client authentication? Granted... the ability to brute-force a 2048 bit key signed with sha256 from an internal/protected PKI is going to be rather... umm... difficult. However I don't want to give any prospects of a snow ball's slight chance in Mojave to induce any sort of undesirable condition (DoS, failure of authentication logic, unknown bugs... whatever it is). I want to slow that process down so it can either be detected earlier or prevented as a whole - of course. Plus, I'm an overly paranoid soul who simply rather not provide the ability for random sources to pound on the door at-will. That being said... anybody share that concern? Has anybody done anything to put controls in place to limit failed SSL client authentication? In my scenario, nobody should be touching the VS unless they have an approved mobile device that is part of our MDM with a certificate acquired by our PKI (SCEP). In light of that, I have zero regard for the gracefulness of client rejection. There might be something built-in to accommodate this scenario... but I'm not aware of it. I was initially thinking iRule, so I just dove right into it. I'm no programmer... but I'm thinking something along these lines (warning: this code has not been tested!). Would love any constructive feedback on any of the above or below! Thanks 🐵 when RULE_INIT { set static::ip_lockout_attempts 3 set static::ip_lockout_xtimeout 900 } when CLIENT_ACCEPTED { set client_ip [IP::client_addr] set hsl [HSL::open -proto UDP -pool syslog.pool] set bad_cert_count [table lookup -notouch $client_ip] if { $bad_cert_count == {} } { table add $client_ip 0 $static::ip_lockout_xtimeout } elseif { $bad_cert_count < $static::ip_lockout_attempts } { table lookup $client_ip } else { reject set time_remaining [expr { [table timeout -remaining $client_ip] / 60 }] HSL::send $hsl ":: SSL_REJECT :: Source IP $client_ip has been locked out. Time remaining: $time_remaining minutes." } } when CLIENTSSL_CLIENTCERT { if { [SSL::cert count] > 0 } { set cert_result [X509::verify_cert_error_string [SSL::verify_result]] if { $cert_result eq "ok" } { table delete $client_ip } else { table incr $client_ip HSL::send $hsl ":: SSL_REJECT :: Client certificate from $client_ip rejected." } } else { table incr $client_ip HSL::send $hsl ":: SSL_REJECT :: Client certificate from $client_ip not supplied to virtual server." } } Theory and base code borrowed from Jason Rahm and Stephanie via DevCentral.239Views0likes2CommentsForm Based Authentication with Tomcat not working on F5
I have a virtual Server on the BigIP with a SSL client profile. The backend Tomcat server is accessible via http and offers the Tomcat form based authentication. I always get "Wrong Username or Password" It seems the Tomcat responds with status 302 and redirects to a http url, but even when enabling rewriting to https i can´t get it work. It seems the session information oder cookie gets lost but i am stuck in analysis. As the Tomcat form based authentication is a standard i wonder if someone is using this and got it working. Kind regards DanielSolved1.4KViews0likes2Commentsroot password recovery on VE with remote authentication
I'm trying to reset the root password on a VE LTM. When I try to go to the GUI, I get a 500 gateway error. When I try to log in via SSH, my password doesn't work. I can reboot into single user mode following K4178 and mount the filesystems and "chroot /sysroot" per K35811337. However, when I run "passwd root", I get an error saying "the user root is currently authenticated from a remote source" Root shouldn't be remotely authenticated. Any suggestions of how to proceed from here? There's nothing important in the configuration currently, so I'm not concerned with keeping the existing config intact.843Views0likes1Comment