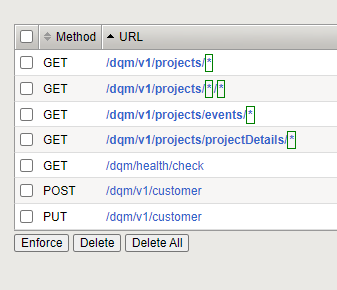
AWAF Path Parameters with OPENAPI json file
Hi, Iam securing a API with a JSON OPENAPI file it mostly works fine however I have two positional parameters used in one url that seems to mask the following paths "/dqm/v1/projects/{customerId}/{pageNumber} &/dqm/v1/projects/projectDetails/{workRequestId}" The result is illegal parameter length violations on a url that is actually valid. the two paths have different operationId headers associated with them Does the WAF use the operationId to match the Path? It appears not as if I delete the operation Id from the api file then the policy matches the correct URL. Any assistance in ubderstanding what is happening and why is appreaciated. Allowed URL's extract from JSON openAPI file /dqm/v1/projects/{customerId}/{pageNumber}: get: tags: - customer-projects-controller operationId: getCustomerProjectsForIdperPage parameters: - name: customerId in: path required: true schema: type: string - name: pageNumber in: path required: true schema: type: string responses: '200': description: OK content: '*/*': schema: $ref: '#/components/schemas/CustomerProjectsResponse' /dqm/v1/projects/projectDetails/{workRequestId}: get: tags: - customer-projects-controller operationId: getProjectDetailswithID parameters: - name: workRequestId in: path required: true schema: type: string responses: '200': description: OK content: '*/*': schema: $ref: '#/components/schemas/ProjectDetailsResponse'Solved1.8KViews1like5CommentsIs there Limitation of irule "virtual".. can we do it like this?
Hi We have BIG-IQ and BIG-IP AWAF. I see that BIG-IQ application dashboard is show only 1 application per virtual server. But in BIG-IP AWAF.. we config it as 1 virtual server 100 application (multi domain vip+use irule to check host header and send it to specific pool and choose specific waf policy) So we can't see each application metric in BIG-IQ.... This is our issue. I understand we need to config each vip for each application so BIG-IQ can retrive data from each vip per application but we can't use that many public ip. So I found that we have irule "virtual" which can send traffic to another virtual server. Can we do it like this? Instead of when HTTP_REQUEST { if {[HTTP::host] equals "abc.example.com"} { ASM::enable /Common/abc.example.com >>>> choose pool and waf policy by host header pool /External/Pool_abc.example.com } ------------------------------------ Change to when HTTP_REQUEST { if {[HTTP::host] equals "abc.example.com"} { virtual VS_abc.example.com >>> send it to private ip virtual server by host header which craete a new. } and in virtual server VS_abc.example.com we use private ip and assign pool and waf policy normally so we can add VS_abc.example.com in BIG-IQ application dashboard and see metric per application. But is there any limitation on how to use irule "virtual" like this? Is this practical?717Views1like3CommentsAre the Bot protection "Browser Verification" and the DDOS "Client Side Integrity Defense" the same?
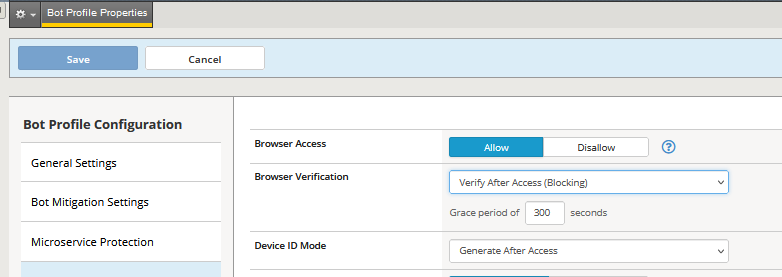
I recently needed to configure some Advanced WAF/ASM Bot defense profile and DDOS profile and I saw the two features "Client Side Integrity Defense" and the DDOS "Browser Verification". I knew them but I started asking myself are they the same feature but with the DDOS profile only after the DDOS threesholds being reached then this feature is activated and for the F5 Bot profile this feature if enabled always checks the web browsers if they support javascript. Basically if I enable Bot protection "Browser Verification" do I need at all to enable the DDOS "Client Side Integrity Defense" feature? Also with the DDOS "Client Side Integrity Defense" feature is the javascript inserted Before Access or After Access?734Views1like1Comment