TACAS not working - No TACACS packets in TCPDUMP
Hi, I have problem with user authentication over TACACS on BIG-IP 12.0 HF2 (Virtual edition). I configured TACACS, add host routes for TACACS server over MGMT interface, all according to config guide, but it is not workin. There is no packets in TCP dump. I tried TCPDUMP over all interfaces, also with command tcpdump -nni 0.0 port 49 but there is no any packet in trace. In log there are messages May 25 16:30:30 f5-04-1 warning httpd[14928]: pam_unix(httpd:auth): check pass; user unknown May 25 16:30:30 f5-04-1 notice httpd[14928]: pam_unix(httpd:auth): authentication failure; logname= uid=48 euid=48 tty= ruser= rhost=10.24.131.4 May 25 16:30:33 f5-04-1 err httpd[14928]: [error] [client 10.24.131.4] AUTHCACHE PAM: user 'xxx' - not authenticated: Authentication failure, referer: https://localhost:15443/tmui/login.jsp?msgcode=1& May 25 16:30:33 f5-04-1 info httpd(pam_audit)[14928]: User=xxx tty=(unknown) host=10.24.131.4 failed to login after 1 attempts (start="Wed May 25 16:30:30 2016" end="Wed May 25 16:30:33 2016"). May 25 16:30:33 f5-04-1 info httpd(pam_audit)[14928]: 01070417:6: AUDIT - user xxx - RAW: httpd(pam_audit): User=xxx tty=(unknown) host=10.24.131.4 failed to login after 1 attempts (start="Wed May 25 16:30:30 2016" end="Wed May 25 16:30:33 2016"). TACAS configuration: auth source { type tacacs } auth tacacs system-auth { encryption disabled protocol ip secret $M$DF$/p4kusJntSq1Ydp41sLeZCOA/SrorObenISS/2pX08k= servers { 192.168.134.206 10.51.10.68 } service ppp } Management routes configuration: sys management-route default { description configured-statically gateway 10.24.131.1 mtu 1500 network default } sys management-route TACACS-1 { gateway 10.24.131.1 network 192.168.134.206/32 } sys management-route TACACS-2 { gateway 10.24.131.1 network 10.51.10.68/32 } Any suggestions?1.1KViews0likes5CommentsTACACS+ Timeout
Hi all, I have been successfully authentication to my F5 estate using TACACS handing off to AD for many years. I have now added another layer by integrated with my MFA platform but cannot figure out how to alter/set timeouts for the MFA authentication. My configuration for TACACS is: auth tacacs system-auth { protocol ip secret xxxxx servers { x.x.x.x y.y.y.y } service ppp } I have set the timeout with: list auth tacacs system-auth timeout auth tacacs system-auth { timeout 15 } When I connect, I am prompted to MFA for both CLI & GUI. However, if I wait for 30 seconds, 1 minute, etc. the MFA session is still waiting & authenticates me when I accept the MFA challenge. Can anyone out there suggest what I'm missing in making the timeout time me out?980Views0likes3CommentsMultiple AAA authetication groups to TACACS
Currently I authenticate to a TACACS for my read/write account. Anyone who needs to manage the LTM will be added to that group. However I need to give auditor access to a group of users. When I great a local account it doesn't allow me to add a password. I can't add them to the group that I'm in because they will have too much access. How to I get the LTM to authenticate a group of users with an auditor role.Solved899Views0likes18CommentsBigIQ integration with Cisco ACS (TACACS+)
I'm working with Big-IQ Central Manager and would like to authenticate against our TACACS (Cisco ACS) and use the RBAC capabilities; however the documentation is slim at best. I'm getting an error, "User has no roles or groups associations. Trying to compare what we set our LTMs to authenticate using remote roles that are defined in ACS (below) to what I have on our BigIQ. On our LTMs: 1. No users defined local 2. Authentication - Remote - TACACS+ 3. Remote Role Groups a. Group Name = TAC-Auth b. Line Order 20 (Relative to our env.) c. Attribute String = F5-LTM-User-Info-1=TAC-Auth d. Remote Acccess = Enabled e. Assigned Role = Other = %F5-LTM-User-Role f. Partition Access = Other = %F5-LTM-Partition g. Terminal Access = Other = %F5-LTM-User-Console On ACS (Only giving one example) Shell Profiles 1. F5-Device-TACAuth-Admin 2. Custom Attributes a. F5-LTM-User-Info-1 = TAC-Auth b. F5-LTM-User-Console = enable c. F5-LTM-User-Role = Administrator d. F5-LTM-Partition = All BigIQ 1. Auth Providers = a. Name = NA_ACS b. Type = TACACS+ 2. User Groups a. F5_Admin c. Authorization Attributes F5-BigIQ-User-Info = F5_Admin %F5-BigIQ-User-Role = Administrator ACS - Note: My understanding is that since BigIQ doesn't use partitions or the Terminal/Console role it might not be needed. 2. Custom Attributes a. F5-LTM-User-Info-1 = F5_Admin b. F5-LTM-User-Role = Administrator Thank you in advance for any insight! /jeff804Views0likes2CommentsPassword update - TACACS+ authentication
Hi, I have a F-5 BIG-IP i4600 (version 12) configured with remote authentication to a TACACS + server (Cisco ACS) The authentication works correctly. The problem happens when the password expires, access to the F5 device is denied, without request password update. From the web interface F5, users can not change their password. Is it possible what I try to do? It's necessary that users can update their password from the web interface of the F5 device Thank you!672Views0likes2CommentsF5 log: TACACS errors - wrong session ID in response
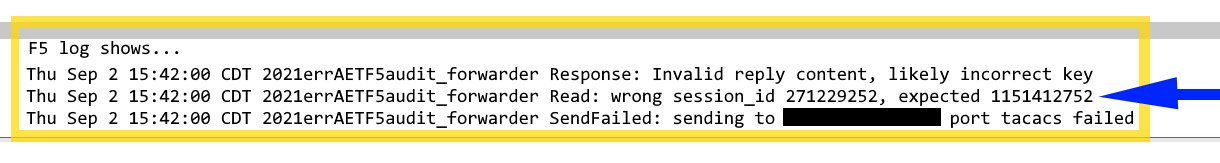
I've opened a TACACS error log msg issue with F5 support. What's appearing in the big ip log (on a standalone 2200, as well as other big ips I have) is a string of messages about an incorrect/unexpected session ID in TACACS responses to queries. A Wireshark capture shows the same session ID in both the query and the response which I would think is correct, however some other ID is expected in the response (as shown below). Is anyone familiar enough with big ip <=> TACACS query/responses to say what is normal here? Note: the 271229252 ID below is the one seen in both the query and response in Wireshark:658Views0likes0CommentsTacacs Remote address field not sent
Hello, Our load balancers use Cisco ACS for authenticate network operators (TACACS protocol), some of the ACS policies are based on source IP. We realized Big IP is not sending Remote address Field, and that is why our ACS rules are not being applied. Any ideas for solving this problem ? Version: 11.4.1 - 647.0485Views1like4CommentsEnabling TACACS+ locks out public key auth local admins
After enabling TACACS+ for local administrator authentication on a BIG-IP all non-default local admin users using public key authentication can no longer login. I suspect this is because remote user authentication only permits TMSH where as public key authentication tries to start BASH which may no longer be permitted. Is their are workaround or a way to fix this?450Views1like2Commentstacacs attibute value pair settings for remote role attributes
Hi, I've read Sol8811 and sol8808 and articles https://devcentral.f5.com/articles/v10-remote-authorization-via-tacacs-43.U0yHO_mulsE http://support.f5.com/kb/en-us/products/big-ip_ltm/manuals/product/ltm_implementation/sol_mgmt_auth.html1030640 on ACS 4.2 - i got auth working via the following: create a 'new service' on the Interface Configuration>Tacacs+(Cisco IOS)>New Services. I created a new service called 'F5_extras' with protocol 'IP'. This enables the new setting to appear in my existing Group (which contains many different vendor equipment). In the Group setting I can assign PPP IP via 'custom attributes' window: service=PPP protocol=IP Obviously set your F5_extras in your LTM tacacs configuration. (NOTE: ip assignment of dialup was not required for me - its mentioned a in a forum). For REMOTE ROLES how to I configure the ACS for the attributes? eg, mentioned on the dev central forum a user applied these attributes to the ACS device: F5-LTM-Host=4500ltm1 F5-LTM-User-Role=administrator F5-LTM-User-Partition=Common F5-LTM-User-Console=tmsh From Cisco site the Attribute values eg's are: eg's •acl= •autocmd= •callback-line •callback-rotary •cmd-arg= •cmd= http://www.cisco.com/c/en/us/td/docs/net_mgmt/cisco_secure_access_control_server_for_windows/4-2-1/User_Guide/acs421ug/A_TACAtr.htmlwp977782285Views0likes1Comment