OAuth SSO
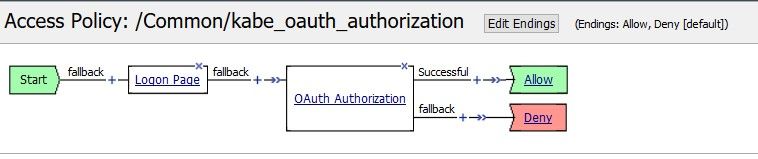
Hi All, we'd like to secure the access to a backend portal with OAuth (F5 Authorization Server and F5 Client/Ressource Server). We aleady configured 2 Virtual Servers and 2 Access Profiles access profile 1 for the backend application (OAuth Client and Scope Agents) access profile 2 for the OAuth AS (Logon Page, LDAP Auth and OAuth AS Agent) The login and the OAuth (OIDC) works with the backend via id_token. Idea was to ask the user ONCE for his LDAP Credentials and then authorize the user in subsequent authorization requests from client applications WITHOUT asking for entering his credentials again. What we see in the session logs is, that the authorization server session always ends with "session deleted (oauth_finished)" once the authorization request has successfully ended, hence the users LDAP information is destroyed together with the "session deleted" Is it possible to get some kind of SSO so that the users credentials is stored in the client for subsequent authorization requests and that the logon page can make use those credentials without prompting the user to login manually again? Thanks Steffen432Views2likes3CommentsBIGIP OAUTH : Transmit "Application id" to backend server after a successful atuthentication
Hello @ all 🙂 I took over the management of a bigip (15.1.1) on which APM is configured, in particular to do OAUTH for partner applications. I'd like to know if it is possible to transmit used application id (from "Access ›› Federation : OAuth Authorization Server : Client Application " ) to backend server. Here is what I had understood about how it works (currently functionnal): External form, when "Authentication button" is clicked, redirect to a form hosted and managed with APM on our F5. An Access policy is used and when user is authenticated, the brower redirect to the external application using one of the defined url for the current Application ("Access ›› Federation : OAuth Authorization Server : Client Application " : Security settings/Redirect URL(s) ). Then, the next requests are authenticated. I'd like to know if it is possible (and how) add an information that could be transmitted to backend server to identify the used application. Little precision : we can't change the current behavior of the external app : it means that the solution should be on the BigIP. Thank you for your helpSolved1.1KViews0likes10CommentsUsing Custom OAuth Client iRules
How do I use iRules with OAuth Server Profile? What are the valid events that will fire to trigger execution. Products docs just say "attach and iRule if you want customization". https://support.f5.com/kb/en-us/products/big-ip_apm/manuals/product/apm-authentication-sso-13-1-0/37.html Under heading "Configuring OAuth servers for APM as a client"556Views2likes2CommentsOAuth SSO like SAML Inline SSO possible?
Hi Folks, I have the following challenge and I am unsure, how it can be solved. F5 APM as OAuth Authorization Server Web Application as OAuth Client + Ressource Server Szenario 1: Internal Access This works like a charme. The user go's to the Web Application, clicks on the OIDC Login Link, is redirected to the Authorization Server, etc. The classic grant flow. Szenario 2: External Access through APM Portal The customer demand is, to publish this web application through a F5 APM Webtop with single sign on. The Web Application does not support getting the JWT from the authorization header, therefore all Bearer SSO methodes are not working. The application must go through the OAuth Grant Flow transparently for the user. This looks like the SAML Inline SSO method, but that is not possible with OAuth or do I miss anything? I have two ideas, how this can be solved. It would be great, If someone knows an even simpler method. Publish the OAuth Server in the internet. Publish the Web Application through a new Virtual Server with an Access Profile attached. Add Portal Link to the Web Application. Span the access session accross both Access Profiles. Opening the Web Application from the Web Top -> works seamless with the same Access Session Clicking on the OIDC Login Link at the Web Application Redirect to the OAuth Server New Access Session begins and the user must login again -> BAD The new access session for the Authorization server is required, because: The Access Policy must be validated to trigger the OAuth Authorization VPE Agent. The Access Policy is closed automatically after OAuth Authorization. First idea: At initial login on the Webtop: Generate a secure domain cookie Set it in the browser Write a mapping table (ltm table) cookie->username At the OAuth Server: Get the cookie Lookup the username in the mapping table If found, set the OAuth username, else prompt for authentication OAuth Authorization works without user login again Second idea: At initial auth-redirect Request from the Web Application: Intercept the auth-redirect request Use a sideband connection to request the authorization code from the authorization server (skip authentication, authorization server is only available on the f5 itself) Use another sideband connection to send the authorization code via the redirect-request back to the Web Application Use the redirect-request response as the response for 1. and deliver it to the browser This are the only two ideas I have, too solve this challenge. However, is it really as complex as I think or is there a really simple method I have overseen?1.2KViews0likes4CommentsAPM Oauth clintless mode
Hi, We currently have the following setup: client( not a web browser) sends a post request to an internal oauth server with the following parameters: username: some_user password: some_pass scope: some_scope grant_type: some_grant if the client passes the authentication he receives a bearer access token which is inserted to the header on the response. Then he can access and use the rest api. We want to integrate F5 into the current scenario so it will act as a client/resource provider( I hope those are the right terms) and then will check the validity of the access token. I'm pretty new to all of the terms and the process of getting an access token, I have read couple of posts on devcentral, guides on f5 clouddocs and on ask f5 and started to play around with it. Those are the resources I've used so far: https://devcentral.f5.com/questions/apm-authentication-for-a-sessionless-and-clientless-api-62162 https://clouddocs.f5.com/training/community/iam/html/class2/module1/module1.html https://support.f5.com/kb/en-us/products/big-ip_apm/manuals/product/big-ip-access-policy-manager-single-sign-on-concepts-configuration-14-1-0/04.html https://support.f5.com/kb/en-us/products/big-ip_apm/manuals/product/big-ip-access-policy-manager-authentication-and-single-sign-on-14-0-0/38.html I have a very general idea how its supposed to work: Client sends a POST request to a VS with apm. An irule will check the request and insert clientless mode. somehow I need to parse the POST parameters and assign them to the appropriate APM variables. There must be a provider configuration and a request configuration ( with the appropriate variables which were parsed ). F5 requests an access token from the oauth server and if successful then on the response it inserts a bearer header with the received access token. The client sends requests to the api which is configured behind a different VS with a per request AP which will verify his bearer token and the scope with the Oauth server. I would like to know if that's something possible to achieve and where and how to start. Thanks, Alex584Views0likes1CommentF5 Oauth server introspect JWT access token from external server
dear all, I already have setup a F5 as oauth client, F5 as oauth server (AS) and F5 as API gateway where F5 performs the introspect internally in its oauth database. So that is all working fine. Now we would like to perform introspect from an external server / API gateway towards the F5 and we are using JWT access tokens generated by F5 oauth server. I would assume the endpoint is /f5-oauth2/v1/introspect and we should define resource-server-id, resource-server-secret and access-token. According to the F5 documentation it is used only for Opaque tokens but that is not recommended as best practice is to use JWT. /f5-oauth2/v1/introspect as token introspection endpoint for validating Opaque tokens Now the question, how am I able to perform introspect from an external API server towards the F5 oauth server to validate that the provided JWT access token is still valid?1.1KViews0likes1CommentHow to trigger an OAuth discover using TMSH or REST API?
Hi all, I was just wondering how to trigger the discover process of an OAuth provider via TMSH or the REST API. I see a pull-config option in tmsh, but it doesn't appear to do anything?!? modify apm aaa oauth-provider provider_test pull-config Can anyone help? Regards, SimonSolved667Views0likes2CommentsUsing OpenID Connect to authenticate users
Hello all, I want to use OpenID Connect to authenticate my users before gaining access to one of my application. I want to use my bigip as OpenID Provider (ie: the entity that authenticate the users) . My issue is the following: The OpendID provider (my bigip) never provides me with a ID Token. All I have is an “Access Token” and a “Refresh Token” but no “ID Token”. Below is a description of my lab: resource owner: ip address 10.10.255.1 bigip OpenID Provider: virtual server ip 10.10.255.221 (see below for the access policy) *The agents are left with their default values. Client: I user openid debugger (https://oidcdebugger.com/) in order to request the authorization code. Then I request the Tokens using an html code. I do the following for testing : I request the authorization code from the authorization server (ie my virtual server) . For this I use openID Connect debugger to construct the request for me. Here is the request that I send : ? client_id=e1111098ccff5f81859f9fc83eaa000c29267803efc0bb5b & redirect_uri=https://oidcdebugger.com/debug & scope=openid myscope & response_type=code & response_mode=form_post & state=toto & nonce=7r8saarltr After sending this request I enter my credentials (in the logon agent), I click on authorize then the virtual server correctly redirects me to: https://oidcdebugger.com/debug code=cae85f6fd33c6b27f56f536b6fd9af2ca0fc78e69ac3d13799533c143b38b4ac&state=toto” I now have a correct authorization code that I can exchange for an “access token” AND a “ID Token” . I then send a POST to get the access and ID Tokens using the following HTML code : *note the presence of the “openid” in the scope parameter. However, this is what I get from the authorization server (see in the comment) : -> I have No “ID TOKEN” ☹ Could you please help me configure my access policy so that it supports OpenID Connect and sends me an “ID Token” ??2.7KViews0likes8CommentsF5 OAUTH JWT error "failed trust verification with trusted CA bundle"
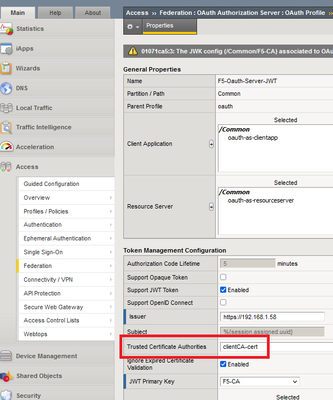
Hello to All, I tried using F5 as an OAUTH server that generates JWT tokens on 16.1.3.2 but I get the error "01071ca5:3: The JWK config (/Common/F5-CA) associated to OAuth profile (/Common/F5-Oauth-Server-JWT) failed trust verification with trusted CA bundle (/Common/clientCA-cert). " . I generated my own CA cert following "K14499: Using OpenSSL to create CA and client certificates (11.x - 16.x" https://support.f5.com/csp/article/K14499 Maybe I am doing something wrong or it is a bug but I am not certain as I do not have not worked with F5 as an Oauth JWT server. I am checking just really fast with the community as this is not something critical but if someone has seen this I will be happy to get a feedback 🙂 With or without Certificate Chain it is the same error or X5C. I am wondering as the certificate is 2048 bits RSA ifit should be 256 but I think this shouldn't matter. As a workaround I am using Octed JWT Key with a long shared password generated by a password generator that works. Also I tested with opaque keys as shown in https://support.f5.com/csp/article/K14391041 and it works but with those keys I do not think there is a way the F5 Auth server to return some usefull info like AD groups/emails to to the Oauth Client that is another F5 device as with JWT this is done with Claims. I did not find if F5 as an Oauth Authorization server supports UserInfo Request URI where after the authorization code that the web browsers provide is exchanged for Opaque Access token to configure what info the F5 Oauth Server to provide to the F5 Oauth Client but maybe some knows this. To bad that for OpenID Connect the JWT needs first to be enabled for the Oauth profile and thisagain means using Octed JWT Keys for either Access or ID tokens 😞647Views0likes2CommentsAPM JWT Multiple Providers NOT WORKING
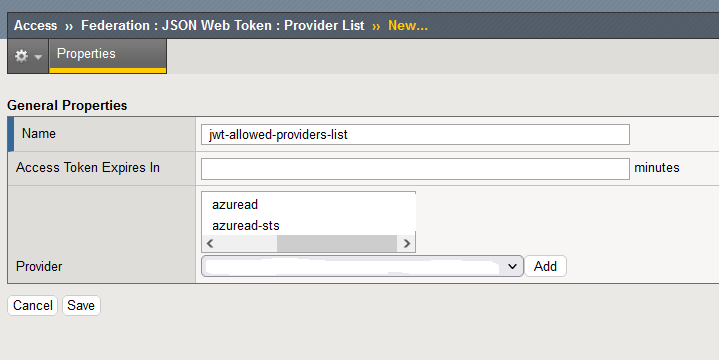
Dear F5 community, Using F5 APM 16.1.3 (as an oauth resource server) I am trying to implement a per-request policy that will verify the signature of JWT tokens sent by the client. These JWT tokens can be issued from two differents issuer (Azure AD or STS). I am able to verify JWT tokens for each provider seperatly using a dedicated "JWT provider" with only one Provider attached. When using 2 providers as follow I got following error message: WWW-Authenticate:Bearer error="invalid_token",error_description="Issuer Mismatch : Claim issuer= https://sts.windows.net/ Provider issuer=https://login.microsoftonline.com/v2.0" Based on F5 doc below, the built-in object supports having multiple JWT providers https://clouddocs.f5.com/cli/tmsh-reference/v15/modules/apm/apm_oauth_jwt-provider-list.html Configuration is pretty simple: - 1 Access Policy with "Allow" all ending - 1 Per-Request Policy with "OAuth Scope" set to "Internal" with the "jwt-allowed-providers-list" I guess It is most likely a bug. Anyone was able to make it work with multiple JWT providers ? I can workaround this by parsing the JWT payload, then determining the issuer and based on the issuer make two branches in the VPE: - first branch with the "oauth scope A" that will validate the token using JWT-Provider-A - second branch with the "oauth scope B" that will validate the token using JWT-Provider-B Thanks2KViews1like5Comments