Help with iRule logging to local0.
I am trying to log an iRule, but it keeps erroring out. Can you help with what I'm missing? when HTTP_REQUEST { if { [HTTP::path] starts_with "/media" } { pool persist cookie insert log local0. ”media.com_28080 TCP_logging fired, from [IP::client_addr]" } }5.7KViews0likes9CommentsiRule to Forward Traffic Based on URL Name
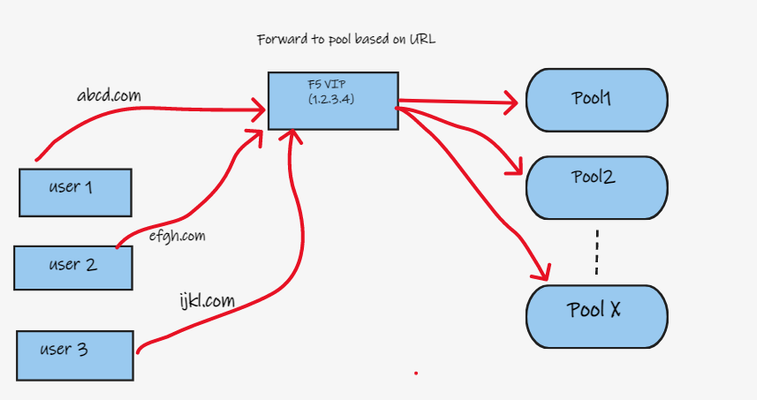
Hi, I am in a situation where we have shortage of IP address and am looking for an alternative way to forward traffic to pools based on URL. I am not really good with iRule hence looking for assistance and I have seen posts based on URI, but i am looking for assistance with URL. Eg: 1 VIP and based on the url name, the traffic needs to be forwarded to Pool. Help on this is appreciatedSolved3.2KViews0likes10CommentsiRule to decrypt and rewrite RADIUS User-Password AVP
In the RADIUS protocol, the user's cleartext password is transmitted inside Attribute-Value Pair (AVP) 2, padded with null characters as necessary, and then encrypted by the shared secret by XOR'ing it across the authenticator somehow or other. The technical details of how this works is a bit above my level of understanding as I'm not a cryptography expert. We have an infrastructure where our PAN VPN Gateway prompts a user for their username and password. In our environment, after the password, the user appends a fixed-length HOTP token from a Yubikey. The backend FreeRADIUS server has been configured to decrypt the password received, extract the fixed-length token, and perform backend checks to our LDAP and token servers. FYI, the password is encoded as PAP prior to RADIUS encryption in our setup, which is why this works; CHAP would prevent this from working. We've been having trouble with the stability of our FreeRADIUS server and we would like to leverage our much more stable Aruba ClearPass infrastructure which is load balanced globally with our GTMs and LTMs and highly stable. This also moves control of the RADIUS piece away from the systems team and onto the network team (me, specifically). Unfortunately, ClearPass doesn't have a direct mechanism to break the password from the token, and PAN doesn't have a way to transmit the token separately. This is where we would like to leverage an iRule. Basically, the way I envision this working is as such: Decrypt the password+OTP that is received from PAN using the authenticator value and shared secret Rewrite AVP 2 as just the password, encrypted by the shared secret (make sure to adjust the length of the AVP) Insert AVP 17 (which is not defined by the IEFT) with the token (ClearPass can be configured to look for this by modifying its RADIUS dictionary). Rewrite the length value at layer 7 if necessary - not sure if this would happen automatically by the F5; probably not. Ship the modified RADIUS packet to ClearPass I know how to accomplish all of this on the ClearPass side, but my dev skills are weak, I'm not very familiary with Tcl, and I don't have a solid understanding of how to encrypt/decrypt the password correctly. I've search high and low but the only solutions for decrypting the password seem to be written in languages that are even more difficult to understand like C. I obviously understand it is too much to expect someone to write the entire solution for me, but any advice on where to start would be very helpful. I think the trickiest part for me would be the encrypt/decrypt step.Solved2.6KViews0likes21CommentsBIG-IP : iRule test that variable exists and has certain value
F5 BIG-IP Virtual Edition v11.4.1 (Build 635.0) LTM on ESXi What is the simplest most elegant syntax to test that a variable exists and has a certain value ? For example if I want to determine that myvariable exists and has non-zero value , is this the simplest syntax ? when HTTP_REQUEST { set myvariable 0 conditional processing ... set myvariable 1 more processing ... if {[info exists $myvariable] && [$myvariable]} { do something }2.5KViews0likes2CommentsRequest client cert auth based on URL
I am trying to request client cert authentication based on select URL and it works with a whitelist only but when i use the negate in the datagroup with a datagroup including URI string values it does not work. Sounds perhaps weird but it seems that negating the datagroup with URI entries is not working properly. So when using a whitelist which should be bypassed it works and other websites are authenticated succesfully and a client certificate is being requested. In the client SSL profile we dont use the client cert authentication because we dont want the client cert authentication to be performed for all URLs, hence the SSL::renegotiate option. This seems to do the trick however while negating (not) against a list of websites that should use cert auth does not work and currently dont have the explenation for this behavior. We only have a list of websites that is using cert auth and not a full list of other websites that shouldnt use cert auth, therefor negating the websites would be the easiest solution. Is there any limitation with negating a datagroup with string values? Another side question is that we would like to perform the SSL::renegotiate and request a specific client cert from a certain CA issuer, how could we accomplish that? when HTTP_REQUEST { if {not[class match [string tolower [HTTP::uri]] contains DG_ACC_NO_CERT_AUTH] }{ #HTTP::header insert SSL_CLIENT_CERT [b64encode [SSL::cert 0]] log local0. "certificate not inserted and header SSL_CLIENT_CERT value is: [HTTP::header value SSL_CLIENT_CERT] for host [HTTP::host] and URI: [HTTP::uri]" } else { SSL::session invalidate SSL::authenticate always SSL::authenticate depth 9 SSL::cert mode request SSL::renegotiate enable SSL::renegotiate HTTP::header insert SSL_CLIENT_CERT [b64encode [SSL::cert 0]] log local0. "certificate inserted and header SSL_CLIENT_CERT value is: [HTTP::header value SSL_CLIENT_CERT] for host [HTTP::host] and URI: [HTTP::uri]" } }Solved2.5KViews0likes14CommentsHow can I preserve the original HTTP Host Header to the Backendservers?
Hi guys, I'm trying the following configuration to loadbalance a RH SSO Key cloack Cluster: clientIP -> https/443 -> (clientssl-Profile) F5-Virtual Server (serverssl-Profile) -> SNAT-IP -> tcp8443 -> Backendserver The Backendserver need to see the original client http Header, so I created a http Profile with the "Insert X-Forwarded-For"-Option enabled. Alternative I tried the following iRule: when HTTP_REQUEST { HTTP::header insert X-Forwarded-For [IP::client_addr] } Unfortunaly, both ways didn't work properly... How can I preserve the whole original HTTP Host Header trough the F5 to the Backendservers? Thank you!2.4KViews0likes3CommentsCookie Does Not Contain The "secure" Attribute on ltm vip
Our security team reported that multiple vulnerabilities has been detected on one of VIP: 1.2.3.4 (on BIG-IP LTM v12.1.2 version.) Please refer the list as below 1.Cookie Does Not Contain The "secure" Attribute 2.Path-Based Vulnerability 3. Session Cookie Does Not Contain the "Secure" Attribute 4.Slow HTTP POST vulnerability I also Referred this below article but "I don't find any kind of persistence profile enabled and also no custom http profile exist on this mentioned VIP ". K30524234: The HTTPOnly and Secure attributes are enabled by default in the Cookie persistence profile If cookies persistence not enabled on VIP, then is it something need to look at backend server (poolmember). please confirm me Kindly help me to fix this issue Great thanks, Girish2.2KViews0likes3CommentsiRule [string range...] not chunking data properly
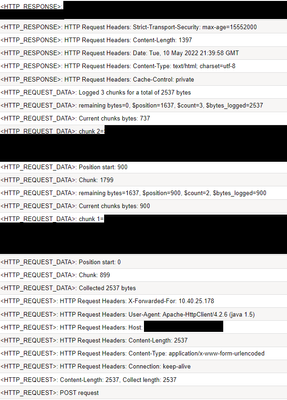
I have an irule (much of which I found here) that is to gather some much needed troubleshooting data I need in regards to the headers and payload I have coming in. The payload is obvisouly too large for a single log line so this was supposed to chunk it into manageable bytes. I had to make some modifications to the original irule which did not work, but now it is working, sort of. It logs the first 900 bytes as it should, then something happens and skips a bunch, and then logs the final bytes of data. I can't understand why it's not grabbing either the proper amount of data or failing to output this second chunk of missing data before making its final loop. iRule is here: when RULE_INIT { # Log debug to /var/log/ltm? 1=yes, 0=no set static::payload_dbg 1 # Limit payload collection to 5Mb set static::max_collect_len 5368709 # Max characters to log locally (must be less than 1024 bytes) # https://clouddocs.f5.com/api/irules/log.html set static::max_chars 900 set static::min_chars 0 } when HTTP_REQUEST { # Only collect POST request payloads if {[HTTP::method] equals "POST"}{ if {$static::payload_dbg}{log local0. "POST request"} # Get the content length so we can request the data to be processed in the HTTP_REQUEST_DATA event. if {[HTTP::header exists "Content-Length"]}{ set content_length [HTTP::header "Content-Length"] } else { set content_length 0 } # content_length of 0 indicates chunked data (of unknown size) if {$content_length > 0 && $content_length < $static::max_collect_len}{ set collect_length $content_length } else { set collect_length $static::max_collect_len } if {$static::payload_dbg}{log local0. "Content-Length: $content_length, Collect length: $collect_length"} foreach aHeader [HTTP::header names] { log local0. "HTTP Request Headers: $aHeader: [HTTP::header value $aHeader]" } #set payload [HTTP::collect $collect_length] HTTP::collect $collect_length } } when HTTP_REQUEST_DATA { # Log the bytes collected if {$static::payload_dbg}{log local0. "Collected [HTTP::payload length] bytes"} # Log the payload locally if {[HTTP::payload length] < $static::max_chars}{ log local0. "Payload=[HTTP::payload]" } else { # Initialize variables set remaining [HTTP::payload] set position 0 set count 1 set bytes_logged 0 # Loop through and log each chunk of the payload while {[string length $remaining] > $static::min_chars}{ #chunk = 899 set chunk [expr {$position + $static::max_chars -1}] log local0. "Chunk: $chunk" log local0. "Position start: $position" # Get the current chunk to log (subtract 1 from the end as string range is 0 indexed) set current [string range $remaining $position $chunk] log local0. "chunk $count=$current" log local0. "Current chunks bytes: [string length $current]" # Add the length of the current chunk to the position for the next chunk incr position [string length $current] # Get the next chunk to log set remaining [string range $remaining $position end] incr count incr bytes_logged $position log local0. "remaining bytes=[string length $remaining], \$position=$position, \$count=$count, \$bytes_logged=$bytes_logged" } if {[string length $remaining]}{ log local0. "chunk $count=$current" incr bytes_logged [string length $remaining] } log local0. "Logged $count chunks for a total of $bytes_logged bytes" } } when HTTP_RESPONSE { foreach aHeader [HTTP::header names] { log local0. "HTTP Request Headers: $aHeader: [HTTP::header value $aHeader]" } } The image below shows what I'm talking about - it even says "Oh I found 3 chunks", but I'm only being presented 2. I added some logging around the position, chunk value (aka end position), and bytes logged to help illustrate that it's clearly skipping over something. Any help would be appreciated! ThanksSolved2.1KViews0likes6CommentsIssues to forward requests with 'start with' due to similar contexts under same domain
Hi everybody, A network request that seemed to be simple is giving some trouble to our network team, I'd appreciate some help. Here's a summary of the rules to be put in place: 1) example.domain.com/cali --> forward to server1 2) example.domain.com --> forward to server2 When creating the rule with "URI starts with" from web interface it works, but there's a side effect: requests like example.domain.com/california are matching rule 1) and therefore failing, since that context is managed by some Apache at server2. They've tried using 'IS' instead 'STARTS WITH' for /cali but then, when trailing slash is not added, it fails. It also fails when calling something like /cali/ad Since we don't know what other possible contexts might be requested, we want just to add a rule for /cali and leave everything else (/california , /calisthenics, ...) under rule 2) What's the issue here? Is something like it possible just using the web interface or are iRules needed? Any examples? Thanks a lot in advanceSolved2KViews1like4CommentsHow to avoid "Access policy evaluation is already in progress"
Hello, I am using the iRule below to close Outlook Web App 2013 sessions. At the first sight it works correctly and shows the F5 logoff page (/vdesk/hangup.php3). However, OWA 2013 has a javascript that performs a hidden POST to the server on the onunload event to close the session on the server side. This happens right after the session is closed by the F5 logoff page. So it automatically creates a new APM session and when the user clicks on "Click here to login again" he/she sees the message below coming from APM: "Access policy evaluation is already in progress" How can I avoid this message? I tried to do ACCESS::session remove on in response to this last hidden POST but it didn't help. I also tried to introduce some delay before redirecting the user to the F5 logout page in order to let it perform the last POST but it did not work either. when HTTP_REQUEST { Set the uri variable set uri [string tolower [HTTP::uri]] Check if the user clicked the OWA signout link and redirect to the F5 logout page if { $uri contains "/logoff.owa" || $uri contains "/logoff.aspx" } { HTTP::redirect "/vdesk/hangup.php3" } }2KViews0likes14Comments