APM Oauth clintless mode
Hi, We currently have the following setup: client( not a web browser) sends a post request to an internal oauth server with the following parameters: username: some_user password: some_pass scope: some_scope grant_type: some_grant if the client passes the authentication he receives a bearer access token which is inserted to the header on the response. Then he can access and use the rest api. We want to integrate F5 into the current scenario so it will act as a client/resource provider( I hope those are the right terms) and then will check the validity of the access token. I'm pretty new to all of the terms and the process of getting an access token, I have read couple of posts on devcentral, guides on f5 clouddocs and on ask f5 and started to play around with it. Those are the resources I've used so far: https://devcentral.f5.com/questions/apm-authentication-for-a-sessionless-and-clientless-api-62162 https://clouddocs.f5.com/training/community/iam/html/class2/module1/module1.html https://support.f5.com/kb/en-us/products/big-ip_apm/manuals/product/big-ip-access-policy-manager-single-sign-on-concepts-configuration-14-1-0/04.html https://support.f5.com/kb/en-us/products/big-ip_apm/manuals/product/big-ip-access-policy-manager-authentication-and-single-sign-on-14-0-0/38.html I have a very general idea how its supposed to work: Client sends a POST request to a VS with apm. An irule will check the request and insert clientless mode. somehow I need to parse the POST parameters and assign them to the appropriate APM variables. There must be a provider configuration and a request configuration ( with the appropriate variables which were parsed ). F5 requests an access token from the oauth server and if successful then on the response it inserts a bearer header with the received access token. The client sends requests to the api which is configured behind a different VS with a per request AP which will verify his bearer token and the scope with the Oauth server. I would like to know if that's something possible to achieve and where and how to start. Thanks, Alex584Views0likes1CommentFederation SP SAML with connector automation, Azure as Idp
Hello, I'm tring to setup connector automation for a customer where the BigIP is the SAML SP provider, and Azure as Idp. all is fine, everything is created and authentication is working. However after every "Frequency", the checksum is different and External IdP Connector is being recreated. And therefore the Access Policy needs to be applied. When the Azure, App Federation Metadata file, is download by a browser, the file is never the same. The "EntityDescriptor ID" changes with every download. And therefore also the checksum. So is the IdP Connector automation an option when Azure is IdP? Am I doing something wrong? I've tested with 15.1 and 16.1, but no different behaviour Thanks in advance789Views0likes3Commentstcl logic in SAML Attribute value field possible?
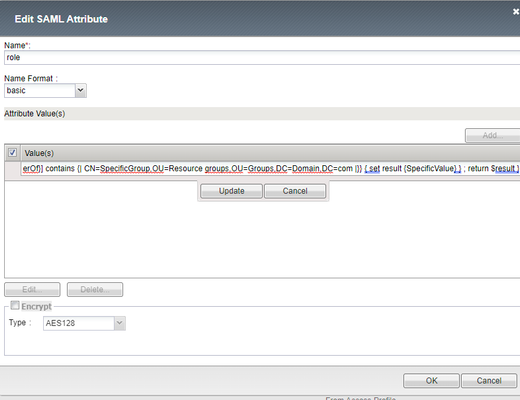
Hi. We're running BigIP as a SAML IDP. Can I somehow issue tcl logic in a SAML attributes? I'm talking about the Access ›› Federation : SAML Identity Provider : Local IdP Services, editing an object, under SAML Attributes. Based on what's in the memberOf attribute, I need to issue as a value either empty string or "SpecificValue". I am familiar with the %{session.variable} construct, but I don't want to clutter the session with more variables if I can avoid it, as that impacts all sessions using our IDP (30 or so federated services on the same VIP and AP). I tried these two approches: %{ set result {} ; if { [mcget {session.ad.last.attr.memberOf}] contains {| CN=SpecificGroup,OU=Resource groups,OU=Groups,DC=Domain,DC=com |}} { set result {SpecificValue} } ; return $result } expr { set result {} ; if { [mcget {session.ad.last.attr.memberOf}] contains {| CN=SpecificGroup,OU=Resource groups,OU=Groups,DC=Domain,DC=com |}} { set result {SpecificValue} } ; return $result } Expected result: An issued claim with the value "" or "SpecificValue" Actual result: An issued claim with the above code as the value As I mentioned, we've set it up using one VIP that is hosting 30 or so services. We're running 16.1.3.1. They are using the same SSO configuration and there's an iRule triggerd at ACCESS_POLICY_AGENT_EVENT, which does some magic to extract issuer and suchlike, and that helps to make decisions later in the Access Policy. It also populates a few session variables under the session.custom namespace for use in the Access Policy. Additional session variables are being populated in the Access Policy, such as resolved manager and their email address. I have looked briefly at the ASSERT::saml functions, but even if it would bepossible to manipulate that way, I wish to keep this set up as stream lined as possible and with as few new "special cases" in an iRule. So while I appreciate pointers along that route as well, I would first of all like to know if there is a way to do it natively in the SAML attribute value field. And if there are any options I have not yet explored here?862Views0likes5CommentsADFS Proxy- first time setup
Very new to ADFS and SAML especially with dealing with the F5. I have business case to add ADFS to one of my current setups. My organization has ADFS setup and i have a few questions for the community. Do i first connect and test the application with our current ADFS setup to make sure it can work? Once the ADFS has been tested and working, do i then try to do ADFS proxy withthe setup? or do i skip step 1 and just start with the ADFS proxy first and try to get that to work with the application? I have seen a few online labs for ADFs proxy etc... but just wondering what the community thinks? looking to have it setup like this: User -> F5 (VIP with login portal) -> sends info to ADFS -> ADFS sends token to F5 -> traffic goes to VPN tunnel to actual portal -> accepts the ADFS token -> User is logged into the service. trying to keep the initial traffic going down the tunnel first and getting redirected back to the F5 for authentication.408Views0likes0CommentsAutoFill username for Office 365 Federation
Hi. This is a simple question but I can't find a solution and ee are just getting started with our F5 implementation. I have deployed the office 365 federation using the f5.microsoft_office_365_idp.v1.1.0 iApp. I've got things working but when it redirects to my login page on the F5 the username field is blank, is this normal? is there any way to get the username from O365 and pre-populate that field? Thanks for any help Jon618Views0likes4Comments