Dynamic CRL Check with Client SSL Profile - How to notify the user?
Hi, we have implemented dynamic CRL checking with client SSL profile in our test environment with BIG-IP 15.1. And it works. If a test user tries to establish a SSL session to a VIP with dynamic CRL checking enabled and the user's cert is revoked, the BIG-IP resets the connection. We are looking for a wayto direct the user's browser to an error page so that the user would be notified that the application can't be accessed because the cert is revoked. Obviously, SSL session is (or not) established before any traffic can be sent over HTTP. We can verify CRL check result with "SSL::verify_result" in an iRule (for example), but the session is reset before an HTTP redirect can be sent. We are aware that this can be done with LTM + APM, however for this use case the APM is not available. This was, for example, possible in the "old days" on Cisco ACE with: parameter-map type sslMap_Name authentication-failure redirect cert-revoked url URL_Address Any ideas & help on how to notify the user that the cert has been revoked greatly appreciated. Thanks!Solved52Views0likes2CommentsSSL client profile - certificate authentication - multiple CRL files
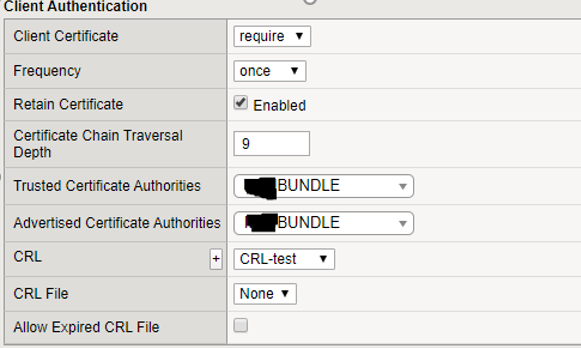
Hi guys, currently I'm running a tests with certificate-based user authentication, using LTM/APM. In general everything is working fine, except for the fact, that there is no option to check several CRL files in one SSL client profile. As there are multiple CAs, that have issued client certificates, I need to check several CRL files. The documentation is not very specific about this piece of information. There are only statements, that it is not allowed to have multiple CRLs in a single master file. I have tried to use CRLDP, but this does only work in conjunction with LDAP. I can only provide the CRLs via file upload to BIG-IP or via HTTP downloads from an internal server. The only idea I have so far, but which is still not tested, is to use several SSL client profiles, one for each Trusted CA, assign the correct CRL file, stored locally on the BIG-IP, and the assign the SSL client profiles dynamically, based on the requested hostname in the SNI extension. To be honest, I cannot believe that there is no easier way to achieve this. Any ideas on that? Thanks in advance. Greets, svs893Views0likes3CommentsDisable certificate revocation checking
I would like to be able to ignore revoked SSL server certificates for certain outbound HTTPS connections. The CA that issued those certificates is under my control. So my first thought was to create a local/static CRL (from my CA) that contained no revoked certificate serial numbers. Then I created a Server SSL profile which used that CRL in the Server Authentication section, and applied that profile to virtual server used for the outbound connection. The outbound connection worked fine until I revoked the server certificate. Now I get a "SSL Handshake failed" error during the connection attempt. So the F5 is clearly not using the local CRL. Am I misundertanding the purpose of a local CRL? Is there another/better way to accomplish this?Solved90Views0likes1CommentSupport dynamic CRL check for clientSSL profile (BIG-IP 15.1)
Hi, Did anyone tested (dynamic) CRL validator object for client SSL profile? (BIG-IP v15.1): It should work in v 15.1 (fixed bug 743758 - https://cdn.f5.com/product/bugtracker/ID743758.html ) I'm getting following errors for all client certificates: err tmm1[21207]: 01a40008:3: Unable to build certificate trust chain for profile /clientssl_profile tmm1[21207]: 01260009:4: clientIP:62042 -> VIP:443: Connection error: ssl_hs_do_crl_validation:6014: alert(46) unknown certificate error With CRL File it works ok, but file does not automatically fetch, check, and cache CRL files… Kr, EPX2.4KViews1like3CommentsF5 BIG-IP LTM VE - disk space issue
We do have a cron job running which updates a CRL file on regular basis in order to allow F5 to use up to date CRL file for verification of client certificate during mTLS. What we have noticed is, that the HDD space is constantly being filled up. We did some investigation and we found out, that there are always files being created in the ./config/filestore/.trash_bin_d/ folder Please see below an example ls -lh ./config/filestore/.trash_bin_d/.backup_1597885592_196_d/Common_d/certificate_revocation_list_d/:Common:trust2408-full_88715_317 ls -lh ./config/filestore/.trash_bin_d/.backup_1597885592_196_d/Common_d/certificate_revocation_list_d/:Common:trust2408-prod_79040_294 trust2408-prod / trust2408-full are the certificate revocation lists created by the script. This is causing, that the file system below is full and F5 can no longer operate properly Here is a difference within 24 hours Status from 19/08/2020 Filesystem Size Used Avail Use% Mounted on /dev/mapper/vg--db--vda-set.2._config 2.1G 467M 1.5G 24% /config Status from 20/08/2020 Filesystem Size Used Avail Use% Mounted on /dev/mapper/vg--db--vda-set.2._config2.1G805M1.2G41% /config I see that there are 10 files generate in less than 24 hours, each file has 43M. At the end of the day it will eat up all free space and cause F5 to not function properly any longer. I would expect, that these files which are in "./config/filestore/.trash_bin_d/.backup_nnnn " foler are automatically removed by F5 on regular basis. Or am I missing anything here? We do have 4 F5 load balancers which have this script enabled and only 2 of them have this issue. All the setup is the same. Has anyone experienced anything similar? Any advice is highly appreciated.551Views0likes2CommentsCRL & OCSP validtion of client certificates from X509 fields
I have requirement to create a Client certificate authenticated VIP with revocation checks. The problem is that the client certificate presented can be issued from one of about 100 different CAs. There is an XML feed which provides me all of the valid CA certificates and I already have a solution to get these into a certificate bundle on the F5, so that's not a problem. I also have an iRule to check the certificate fingerprint against a whitelist, again this works great. However, I am required to check for certificate revocation. Each certificate will have either (or both) a CRL distribution point or an OCSP responder listed in its X509 fields. Is there anyway I can get the 5 to automatically check for certificate revocation against these fields without having to manually import all of the CRL lists and/or setup all the OCSP responders manually? Or failing that, is the a (simplish) way for the F5 to scan the CA bundle and automatically download all the CRL files and concatenate them.317Views0likes0CommentsHow to understand "Update CRL" field in LTM's Certificate Authority profile?
Hi, I am wondering, how should I understand the CRL related fields in LTM's CA profile (Local Traffic > Profiles > SSL > Certificate Authority)? I cannot find any documentation for this profile. I would like to use this CA profile in APM's machine certificate check and make sure that machines with revoked certificates are denied access to APM resources. I understand that the "Certificate Revocation List (CRL)" field defines a static CRL file stored locally which I previously created under System > File Management > SSL Certificate List. But using CRL without a periodic and automatic update does not make sense. But I am struggling to understand what exactly would LTM do if I check the "Update CRL" checkbox under CA profile. How would LTM update this CRL? Where would it get the information for this update from? Would it read the CRL location URL from the certificate and try to access it? Anybody has an idea on how this is meant to work?481Views0likes1CommentIs there a way to auto-update CRL using iRules?
Hi, is there a way to update CRL automatically? We do this using bash scripts, is there a official or different way to do it like for example, iRules? I've seen posts like this but it's a old post. I'm using BIG-IP 11.6.0 Thanks.433Views0likes2CommentsRevoked Cert in CRL not logging
I have a authentication profile CRLDP server set that uses an LDAP instance to check the client cert presented against the LDAP CRL. This works fine and revoked certificates do not successfully handshake. However I don't seem to get any logs of a revoked certificate being presented. I thought I may need an iRule to accomplish this but after playing around with X509::verify_cert_error_string and SSL::verify_result I'm stuck. I keep getting an OpenSSL verify value of 0 X509_V_OK when I expect at least one to be 23 X509_V_ERR_CERT_REVOKED Has anyone got an iRule that successfully logs this info? PS.I'd prefer not to abandon the authentication profile in favour of an Access Policy profile. Thanks298Views0likes1Comment