F5 + VSCode; 2024 roadmap
Greetings team! As I started the vscode project in 2019, I had no idea where it would go. I just knew there was value in using it as a workbence to streamline f5 automations. Since then it has grown into a handful of project covering several different aspects of F5. I am very thankful for all the great comments and feedback over the last couple of years. As the 2023 year comes to an end, I wanted to take a moment to step back and solicit some feedback from the community. Please take a couple of minutes to review the following link and provide feedback. https://github.com/f5devcentral/vscode-f5/discussions/234 In short, this is a way for me to guage where I can make the biggest impact with these projects. Thank you.508Views5likes1CommentF5 APM VPN Support For Microsoft O365 Split-Tunneling
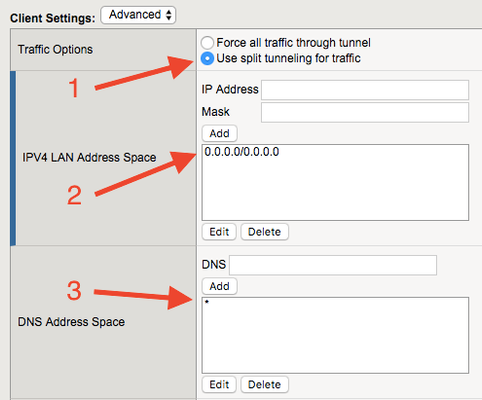
We ran into a significant issue with remote VPN client performance when our Microsoft Office products moved to the O365 cloud offering. Our current limitation of "no split-tunneling" per corporate policy, prevented our users from establishing connectivity to their geographically preferable O365 cloud. Instead, their traffic could/would route back to the corporate F5 APM VPN BigIP and then out to the internet. Much longer path and real-time services such as Teams/Skype calls suffered greatly. Other vendors were also having issues with this such as ForcePoint (Websense) and McAfee. Those vendors released O365 specific patches to permit a better performance through various rules and methods. Our F5 APM VPN was the bottle-neck and we had to address this quickly. Approval was granted to permit ONLY O365 products to be split-tunneled. Luckily, Microsoft has fielded this question/requirement many times and they had a ready answer: https://docs.microsoft.com/en-us/office365/enterprise/urls-and-ip-address-ranges Unfortunately, there's +500 IPv4 networks alone. Many are overlapping and some could be combined into a supernet. Not pretty, but workable. Using node.js, we developed a script that will pull-down the Microsoft IPv4 space, perform a CIDR clean on the networks, log into the F5 BigIP and push the Network Access exclude IP list, then apply the Access Policy in one shot. You can see the repo here: https://github.com/adamingle/f5O365SplitTunnelUpdateScript If you'd like to use the repo, please note the "settings.json" file. You will need to update according to the README.md Additionally, you will need to configure the allowable/tunneled traffic for the Network Access on VPN. If you only specify the exclusion space, there will be no inclusion space and no traffic will traverse the tunnel. Enable split-tunneling by checking the "Use split tunneling for traffic" radio button Add ALL networks to the "IPV4 LAN Address Space" with the IP Address 0.0.0.0 and Mask 0.0.0.0 Specify wildcard/asterisk for the "DNS Address Space" After you have the split-tunneling enabled on your Network Access Lists in F5 APM and you have correctly modified the "settings.json" file of your local f5O365SplitTunnelUpdateScript repo, you should be able to execute your O365 split-tunneling address exclusion changes. Use Jenkins or other automation tool to run the script automatically. Definitely worth a watch: https://channel9.msdn.com/Events/Ignite/2015/BRK3141 *This has been tested/used successfully with the Edge 7.1.7.1 client on v13.1.11.6KViews2likes7CommentsError when running bigip_command Playbook against LTM : Syntax Error: unexpected argument /bin/sh\n
I am running a Playbook to test bigip_command using ansible [core 2.15.3] against LTM running 15.1.6.1. When I run the playbook I get the following message: UNREACHABLE! => { “changed”: false, “msg”: “Failed to create temporary directory. In some cases, you may have been able to authenticate and did not have permissions on the target directory. Consider changing the remote tmp path in ansible.cfg to a path rooted in "/tmp", for more error information use -vvv. Failed command was: ( umask 77 && mkdir -p "echo $HOME/tmp"&& mkdir "echo $HOME/tmp/ansible-tmp-1709037153.0021555-3167181-73985055078518" && echo ansible-tmp-1709037153.0021555-3167181-73985055078518="echo $HOME/tmp/ansible-tmp-1709037153.0021555-3167181-73985055078518" ), exited with result 1”, “unreachable”: true } When I run the Playbook with -vvv flags I see the following line just before the error message pasted above: Failed to connect to the host via ssh: Syntax Error: unexpected argument “/bin/sh” Similarly, if I test the ssh I also see this same unexpected argument message: ansible all -m shell -a id -vvv Syntax Error: unexpected argument “/bin/sh”\n’ I have tried editing various things in hosts file and ansible.cfg but nothing I have tried seems to have made a difference. Is anyone familiar with this and what is needed to resolve this. Any help is greatly appreciated!107Views1like4CommentsLet's Encrypt with Cloudflare DNS and F5 REST API
Hi all This is a followup on the now very old Let's Encrypt on a Big-IP article. It has served me, and others, well but is kind of locked to a specific environment and doesn't scale well. I have been going around it for some time but couldn't find the courage (aka time) to get started. However, due to some changes to my DNS provider (they were aquired and shut down) I finally took the plunges and moved my domains to a provider with an API and that gave me the opportunity to make a more nimble solution. To make things simple I chose Cloudflare as the community proliferation is enormous and it is easy to find examples and tools. I though think that choosing another provide with an open API isn't such a big deal. After playing around with different tools I realized that I didn't need them as it ended up being much easier to just use curl. So, if the other providers have just a somewhat close resemblance it shouldn't be such a big task converting the scripts to fit. There might be finer and more advanced solutions out there, but my goal was that I needed a solution that had as few dependencies as possible and if I could make that only Bash and Curl it would be perfect. And that is what I ended up with 😎 Just put 5 files in the same directory, adjust the config to your environment, and BAM you're good to go!!😻 And if you need to run it somewhere else just copy the directory over and continue like nothing was changed. That is what I call portability 😁 Find all the details here: Let's Encrypt with Cloudflare DNS and F5 REST API Please just drop me a line if you have any questions or feedback or find any bugs.2.1KViews1like6CommentsAutomate ASM "Ready to Be Enforced" Attack Signatures
Hi All, Problem scenario is this: Multiple F5 ASM deplyoments which use BigIQ to push out updated attack signatures ( works well ) and a 14 day Enforcement Readiness Period. This all works well up to this point, where someone manually has to go and click the "Enforce Ready Entities" button. That sounds like a minor thing to do, but in an Enterprise it includes change control/PVT etc to do... ...but automating this out as a fortnightly thing should reduce risk and I can do other things. So I am comfortable with the API, but looking at v13/v14 API I dont see a functionality that can do this for me. Has anyone done this last step to fully utomate attack signature updates ?Solved2.2KViews1like5CommentsAnsible bigip_commands module and Bash
I'm hoping this is a simple question. I'm trying to use ansible to check for the presence of some files on a Big-IP. I've tried using the bigip_command module to call commands like grep and file, but I can't get it to run any bash commands, only tmsh. The description says "bigip_command – Run TMSH and BASH commands on F5 devices". How do I get it to run Bash commands? I must be missing something. Thanks in advance! https://clouddocs.f5.com/products/orchestration/ansible/devel/modules/bigip_command_module.html580Views1like0Comments