ASM issue, need to return HTTP 500 to client in certain cases
I've written a script that captures the "Content-Type" header from requests. In the event that ASM blocks the request, I need to respond to the client with one of three types of responses (I'm using the ASM_REQUEST_BLOCKING event): If Content-Type = text/xml then send back a SOAP error with HTTP 200 If Content-Type = application/json then return HTTP 500 All others return the default ASM response with HTTP 200. Cases 1 & 3 are handled, but I can't figure out how to force an HTTP 500 status to be returned to the client. HTTP_RESPONSE doesn't fire when ASM blocks. Thanks for your advice.Solved3.8KViews0likes6CommentsDisable buffer overflow in json parameters
Hi In a file upload using api we allow the file name in base64 encoding. However this triggers the Generic buffer overflow attempt 1 . As of this post it seems signature at json parameter level cannot be disabled. https://devcentral.f5.com/questions/disable-attack-signature-on-particular-json-parametercomment77010 Has there been any change in this? I am using v12? In my json content profile I do not see the buffer overflow sig at all on filtering with the name.2KViews0likes8CommentsManual Traffic Learning -> Malformed JSON Data: How to handle this?
Hi, i created an ASM policy in blocking mode with a json profile. Sometimes I have a few illegal requests in Security > Event Logs > Application > Requests with "Malformed JSON Data" violation. As attack type it is identified as "JSON Parser Attack" and in the violation details the description is "Malformed document - Illegal encoding sequence". How can I see what's the exact problem on this violation? And how can I handle this problem? If I navigate to Application Security > Policy Building > Manuel Traffic Learning > Malformed JSON Data I don't understand this view. Which settings can be changed with option "Request body handling" and "Enable Staging" and what an effect does this have? I can't find a documentation or something like an explanation about this area and hope for more information from DevCentral. If you need further information please ask.1.5KViews1like2CommentsHTTPS Monitor: JSON File behind login page
Hello, we've already a https monitor that reads the contents of a json file, it looks like this: send string: GET /intern/api/v1/health/portal-status HTTP/1.1\r\nHost: host.company.com\r\n\r\n receive strimg: \"portalStatus\":\"AVAILABLE\" this works fine. but now I need a similar monitor, but the json file is passwort protectet, when I add username/password to the monitor, it doesn't work. when I do a curl: curl -sku monitor:<pw> -H "Content-Type: application/json" -X GET https://host.company.int/monitor/wga/widgets/health.json I get the logon-page for the username/pw I tried some other parameter for curl, but I don't get the content of the json-file. Any ideas? thanks in advance1.2KViews0likes14CommentsASM Flagging JSON Payload Base 64 encoded data as a violation
Hello I have some policies that are accepting encrypted data which has then been encoded with Base64 and sent in a JSON document. However sometimes however this data gets rejected as an attack signature has been triggered. I would really like to leave Attack signature checking on the JSON profile but would like to find a way of filtering out just these signatures that get triggered without blocking legitimate traffic. Currently the URL is in Staging which is allowing them through but I should really enforce this at some point and at that time these violations will get blocked. Has anyone got any suggestions on how I could achieve this. I have been looking at iRules that would unblock a request if a certain criteria is met. James1KViews0likes6CommentsAuthorization Header Defined as Unparsable by F5_ASM
One of our development teams is adding a new OAUTH token feature to an application. Sending the JSON call with the Authorization header creates an error within F5_ASM (ver 15.13): HTTP ValidationUnparsable request content Details Unparsable authorization header value I also see that the Authorization header's data is masked, though there's no settings for the Authorization header in the policy. What are my best options for troubleshooting this issue?871Views0likes3CommentsASM JSON login page
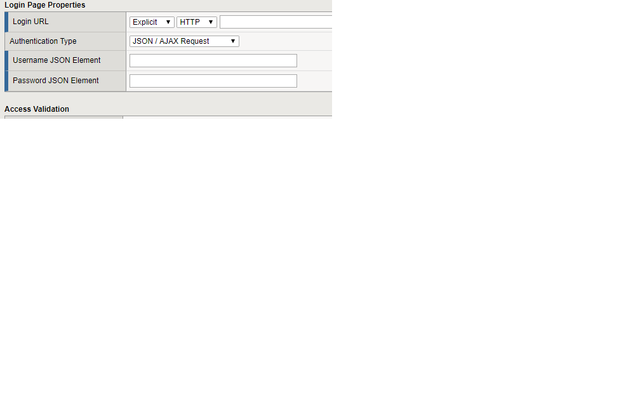
Hi, Trying to configure a JSON login page in ASM. The page first asks for the username and only then for the password. 1) When configuring JSON login in ASM, you must supply both the parameters( username and password), how can I configure only one? 2) In case I'ts possible to configure only one parameter, what is the best approach in this case? to configure 2 different login pages, each with one parameter( 1) password , 2)user)? Thanks, Alex805Views0likes4CommentsUsing an iRule to respond with a 500 Internal Server Error message
Hi, We have a customer error page setup to serve a nice neat error page when various violations are triggered however the JSON applications don't like this as they are not expecting html. What I would like to do is implement an iRule based on any identifiable data such as a header, to respond with a 500 error. For the moment I am just working on the main idea of serving the 500 rather than the custom error however what I have is not working. If someone can review what I have below and let me know why this is ignored and the custom error continues to load, that would be awesome. Thank you. when HTTP_RESPONSE { if {[HTTP::header value Connection] contains "close"}{ HTTP::respond 500 content "Internal Server Error" } }803Views0likes9CommentsBruteforce mitigation on JSON parameters
Hi All, I would like to know the possibilities to protect a webserver,against bruteforce attacks, who uses JSON parameters. In the ASM, the default option is, to protect a loginpage. The webapplication we want to protect, uses JSON parameter. The request looks like this : Content-Length: 84 Proxy-Connection: keep-alive Content-Type: application/json; charset=utf-8 User-Agent: [ics]:[iPad]:[2.1]:[20141103]:[1]:[Retina] Connection: keep-alive {"cardPostFix":"0097","postalCode":"1112CN","houseNumber":"5","expiryDate":"08\/18"} There is a possibility to do something with JSON (JSON profiles) but this concentrate on only the data and lenght that passes the ASM. Not bruteforce. Is there a basis iRule for this to exam this kind of mitigation. I looked for some and find one(POST Request Exponential Backoff), but I'm not sure this is the right way to implement a bruteforce mitigation. Thanks in advance. Erwin591Views0likes4CommentsIs there ressources to mock iControlREST?
Hello all, Is there a huge zip file somewhere with a complete dump of a "classic" F5 installation with virtual servers, policies, etc. I want to mock a iControlREST for unit testing and integration testing of one of our service that use iControl REST but not with production data that can be sensitive and doesn’t belong in a CI/CD chain. Thank you!540Views0likes4Comments