Case insensitivity in ASM Brute Force username and/or password elements
I have a login page I'm attempting to enable brute force protection for (JSON/AJAX auth type), and it supports username and password JSON elements that are case insensitive from our application's perspective, meaning we expect clients to send them with inconsistent casing. The help text shows that the F5 BIG-IP expects these parameters to be case sensitive, which makes me think that even if we used an ASM policy with case sensitivity disabled during creation, it would still be treated as case sensitive. Frankly even if this did work as a workaround, I'm not sure I'd want to do this because I don't want everything in the policy to be case insensitive - just these few login elements. Also I'm not able to create a "duplicate" login URL where each one uses a different case for the username and/or password elements - the ASM policy prevents this. What is the recommendation for how to implement brute force protection for username and/or password parameters that can be sent with multiple cases?581Views5likes4CommentsASM Custom Blocking page - Variables
Hi all, I would like to ask you a question regarding ASM blocking page and variables that can be used in order to present a more extensive content.I know that <%TS.request.ID()%> variable can be used in order to present the support ID to the client.Is there any way to include more variables such as source IP address or XFF header on the html response page ? For example:The requested URL was rejected.Your support ID is: <%TS.request.ID()%>. Your IP is :<%TS.remote-ip-address.ID()%>. I'm using version 13.1.0. Any help would be appreciated. Thanks917Views3likes5CommentsKnowledge sharing: An example of the general order of precedence for the BIG-IP modules. Also, the F5 ASM DDOS Protection or Bot Protection order of precedence explained.
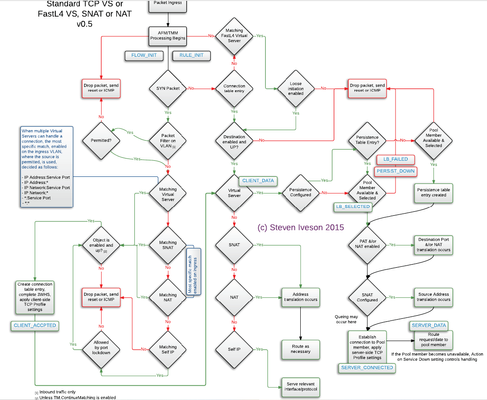
For the General order of the modules in F5: Packet Filter > AFM > iRule Flow Init event> LTM(or GTM/DNS) >APM > ASM . Also in the AFM there is DDOS at Layer 3 or 4 that is before the AFM rules (the same as the ASM). For the AFM DDOS there is general device DDOS and virtual server specific DDOS and the Genaral Device DDOS takes precedence but it has higher by default thresholds and this why during attack the Virtual server DDOS will in most cases be first activated. The Device DDOS is present even without the AFM module but when there is AFM module it can actually be controlled and configured(not only using the default values). The AFM rules themselves have a conext order(https://techdocs.f5.com/kb/en-us/products/big-ip-afm/manuals/product/network-firewall-policies-implementations-13-1-0/2.html). To see what part of the AFM is blocking you use the packet tracer tool: https://clouddocs.f5.com/training/community/firewall/html/class1/module2/module2.html If needed you can still place the ASM infront the APM by following: https://support.f5.com/csp/article/K54217479 https://support.f5.com/csp/article/K13315545 Other F5 precedences is the GTM/DNS order : https://support.f5.com/csp/article/K14510 The Local traffic object and VIP order for the LTM: https://support.f5.com/csp/article/K9038 https://support.f5.com/csp/article/K14800 The F5 irule event order: https://devcentral.f5.com/s/question/0D51T00006i7X94/irule-event-order-http The picture of the F5 order is from the old F5 401 study guide: As in the newer F5 TMOS versions the Bot defense is seperated from the DDOS Protection and as my tests confirmed first the ASM DDOS is activated then the Bot defense and after that the ASM policy and in the most F5 documentation maybe not writen good this is the case. In the older versons also first the DDOS filtered requests and then the Bot Defense further filtered the traffic before the ASM policy. As of now the Bot protection also generates support id, so if you are blocked and you see support id but in the security policy searches you can't find anything also search the support id under the Bot defence request logs as I found this the hard way. The Bot defence can also make in some cases dynamic signatures for the DDOS in order to stop the traffic at the DDOS checks but I still have not seen this done. https://clouddocs.f5.com/training/community/ddos/html/class7/bados/module4.html For testing web DDOS attacks jmeter is a great free tool and for bigger commercial tests there is cloud platform named RedWolf but Jmeter in most cases will do just fine.1.8KViews2likes1CommentSignature enforcement using iControl API
Hi there! I am looking in to the curl commands to update a specific signature in the policy. I can retrieve the self-link using the following command for example: curl -k -u ‘user:pass’ -X GET 'https://192.168.1.245/mgmt/tm/asm/policies//signatures?$signatureId%20eq%20200100092' However, the retrieved self-link is not identical for a policy e.g. /TEST01/test.com.app/test.com.app_policy . What curl commands/Rest APIs should I use to: Identify a signature from signature ID in a specific policy Then enforce that signature to blocking mode Apply the policy change Appreciate your earliest reply on this. Cheers. Best regards Hyder251Views1like0CommentsManual Traffic Learning -> Malformed JSON Data: How to handle this?
Hi, i created an ASM policy in blocking mode with a json profile. Sometimes I have a few illegal requests in Security > Event Logs > Application > Requests with "Malformed JSON Data" violation. As attack type it is identified as "JSON Parser Attack" and in the violation details the description is "Malformed document - Illegal encoding sequence". How can I see what's the exact problem on this violation? And how can I handle this problem? If I navigate to Application Security > Policy Building > Manuel Traffic Learning > Malformed JSON Data I don't understand this view. Which settings can be changed with option "Request body handling" and "Enable Staging" and what an effect does this have? I can't find a documentation or something like an explanation about this area and hope for more information from DevCentral. If you need further information please ask.1.6KViews1like2CommentsWhich attack signature sets does contain others?
My application is running on Apache Tomcat and there is one signature set with such name. Of course, I enabled it. The question is should I also enable sets referred to e.g. Apache, Java Servlets? Or maybe required signatures are containing in Apache Tomcat set already?349Views1like3CommentsUseful 13.1 addition to ASM/AFM
In 13.1 it seems we have more signature/ips like functionality but one thing I think the system really lacks is more actions that can be taken on hits for those signatures. IE: If someone trips a signature looking for /admin on your external site that doesn't contain a /admin directory--this user is obviously up to no good. Beyond just blocking that request it would be nice to have either through and irule or built-in functionality the ability to add that client's IP address to the shun list so that it could be blocked from everything for a specified period of time. I don't see a great way to do this at the moment without creating my own external program to read logs, keep track of ip addresses and add/remove on time intervals....think snortsam for snort...451Views1like2CommentsValidation Error: Malformed XML data
Hi, I am getting Validation Error: Malformed XML datafor XML request having Katakana/Hiragana characters in it. Below error lines from the request report from F5 <v11:frgnfirstName>マレーシア シンガフール</v11:frgnfirstName> <v11:frgnlastName>ç¯ ç”°</v11:frgnlastName>833Views1like5CommentsF5 platform EoSD and Software EoSD is different. Which one need to use?
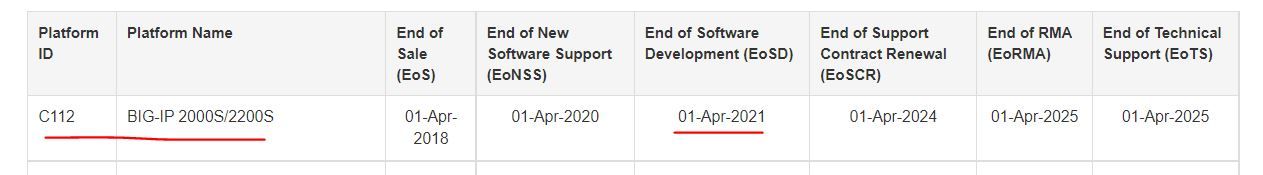
Hi We use F5 2000s with version 15.1.x From platform EoSD, It's already expired but from software EoSD. it's still available question is Which one should I use? If i use WAF and I believe attack signature will release if EoSD is still available...... question is right now will my attack signature still update? 2 what is different?1.4KViews1like3CommentsTCL error: _cgc_pick_clientside
Hi, in an ASM-LTM (Perimeter) Setup I see frquently the following logs: ***err: tmm3[19962]: 01220001:3: TCL error: _cgc_pick_clientside - unknown cgc sni: f5-bei1.xxxx.xx (line 49) invoked from within "CGC::sni $tls_servername"*** Any idea what this TCL error causes? The clientssl is quite Basic: one certificate chain, no Server Name set. Thanks, Rolf1KViews1like4Comments