F5 Predicts: Education gets personal
The topic of education is taking centre stage today like never before. I think we can all agree that education has come a long way from the days where students and teachers were confined to a classroom with a chalkboard. Technology now underpins virtually every sector and education is no exception. The Internet is now the principal enabling mechanism by which students assemble, spread ideas and sow economic opportunities. Education data has become a hot topic in a quest to transform the manner in which students learn. According to Steven Ross, a professor at the Centre for Research and Reform in Education at Johns Hopkins University, the use of data to customise education for students will be the key driver for learning in the future[1].This technological revolution has resulted in a surge of online learning courses accessible to anyone with a smart device. A two-year assessment of the massive open online courses (MOOCs) created by HarvardX and MITxrevealed that there were 1.7 million course entries in the 68 MOOC [2].This translates to about 1 million unique participants, who on average engage with 1.7 courses each. This equity of education is undoubtedly providing vast opportunities for students around the globe and improving their access to education. With more than half a million apps to choose from on different platforms such as the iOS and Android, both teachers and students can obtain digital resources on any subject. As education progresses in the digital era, here are some considerations for educational institutions to consider: Scale and security The emergence of a smogasborad of MOOC providers, such as Coursera and edX, have challenged the traditional, geographical and technological boundaries of education today. Digital learning will continue to grow driving the demand for seamless and user friendly learning environments. In addition, technological advancements in education offers new opportunities for government and enterprises. It will be most effective if provided these organisations have the ability to rapidly scale and adapt to an all new digital world – having information services easily available, accessible and secured. Many educational institutions have just as many users as those in large multinational corporations and are faced with the issue of scale when delivering applications. The aim now is no longer about how to get fast connection for students, but how quickly content can be provisioned and served and how seamless the user experience can be. No longer can traditional methods provide our customers with the horizontal scaling needed. They require an intelligent and flexible framework to deploy and manage applications and resources. Hence, having an application-centric infrastructure in place to accelerate the roll-out of curriculum to its user base, is critical in addition to securing user access and traffic in the overall environment. Ensuring connectivity We live in a Gen-Y world that demands a high level of convenience and speed from practically everyone and anything. This demand for convenience has brought about reform and revolutionised the way education is delivered to students. Furthermore, the Internet of things (IoT), has introduced a whole new raft of ways in which teachers can educate their students. Whether teaching and learning is via connected devices such as a Smart Board or iPad, seamless access to data and content have never been more pertinent than now. With the increasing reliance on Internet bandwidth, textbooks are no longer the primary means of educating, given that students are becoming more web oriented. The shift helps educational institutes to better personalise the curriculum based on data garnered from students and their work. Duty of care As the cloud continues to test and transform the realms of education around the world, educational institutions are opting for a centralised services model, where they can easily select the services they want delivered to students to enhance their learning experience. Hence, educational institutions have a duty of care around the type of content accessed and how it is obtained by students. They can enforce acceptable use policies by only delivering content that is useful to the curriculum, with strong user identification and access policies in place. By securing the app, malware and viruses can be mitigated from the institute’s environment. From an outbound perspective, educators can be assured that students are only getting the content they are meant to get access to. F5 has the answer BIG-IP LTM acts as the bedrock for educational organisations to provision, optimise and deliver its services. It provides the ability to publish applications out to the Internet in a quickly and timely manner within a controlled and secured environment. F5 crucially provides both the performance and the horizontal scaling required to meet the highest levels of throughput. At the same time, BIG-IP APM provides schools with the ability to leverage virtual desktop infrastructure (VDI) applications downstream, scale up and down and not have to install costly VDI gateways on site, whilst centralising the security decisions that come with it. As part of this, custom iApps can be developed to rapidly and consistently deliver, as well as reconfigure the applications that are published out to the Internet in a secure, seamless and manageable way. BIG-IP Application Security Manager (ASM) provides an application layer security to protect vital educational assets, as well as the applications and content being continuously published. ASM allows educational institutes to tailor security profiles that fit like a glove to wrap seamlessly around every application. It also gives a level of assurance that all applications are delivered in a secure manner. Education tomorrow It is hard not to feel the profound impact that technology has on education. Technology in the digital era has created a new level of personalised learning. The time is ripe for the digitisation of education, but the integrity of the process demands the presence of technology being at the forefront, so as to ensure the security, scalability and delivery of content and data. The equity of education that technology offers, helps with addressing factors such as access to education, language, affordability, distance, and equality. Furthermore, it eliminates geographical boundaries by enabling the mass delivery of quality education with the right policies in place. [1] http://www.wsj.com/articles/SB10001424052702304756104579451241225610478 [2] http://papers.ssrn.com/sol3/papers.cfm?abstract_id=2586847844Views0likes3CommentsScrubbing away DDoS attacks
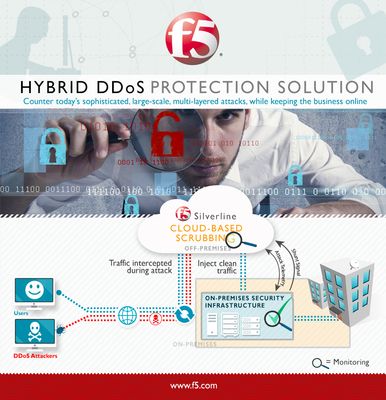
Bigger and badder than ever DDoS attacks are an IT professionals’ nightmare – they can knock out applications that generate revenue and facilitate communications, or even more fundamentally, take down entire networks. What’s worse, they are becoming increasingly sophisticated, large and frequent as cybercriminals get more aggressive and creative. All businesses must now expect DDoS attacks, rather than consider them remote possibilities, and prepare accordingly. One recent study found that in just one year, a whopping 38% of companies providing online services (such as ecommerce, online media and others) had been on the receiving end of an attack. Such attacks have moved up the network stack over time, climbing from network attacks in the 1990s to session attacks and application layer attacks today. Now, application attacks at layer 7 represent approximately half of all attacks. We’re also seeing attacks go even further, into business logic, which often exists as a layer above the OSI model. Protecting your business So how do we protect our content and applications and keep them running in the face of attacks? With attack traffic reaching new heights (the record set in 2014 was 500Gbps), few organizations have sufficient bandwidth to hold up to such magnitudes. Increasingly, businesses are having to turn to scrubbing services to handle such volumetric attacks. You can think of a scrubbing service as a first line of defense against DDoS attacks. Such services process your incoming traffic and detect, identify and mitigate threats in real time. The clean traffic is then returned to your site, keeping any attacks from reaching your network and enabling your businesses to stay online and available. Your users are left blissfully unaware. How scrubbing works For more detail, let’s take a look at how this process works at the new F5 scrubbing center here in Singapore, which is a key piece of our Silverline DDoS Protection hybrid solution. Part of F5’s fully redundant and globally distributedglobal security operation center (SOC), the facility is built with advanced systems and tools engineered to deal with the increasing threats, escalating scale and complexity of DDoS attacks. F5 determines the best scrubbing routes for each segment of traffic and automatically directs traffic through the cloud scrubbing centers for real-time mitigation. As traffic enters a scrubbing center, it is triaged based on a various traffic characteristics and possible attack methodologies. Traffic continues to be checked as it traverses the scrubbing center to confirm the malicious traffic has been fully removed. Clean traffic is then returned through your website with little to no impact to the end user. Silverline DDoS Protection provides attack mitigation bandwidth capacity of over 2.0 Tbps and scrubbing capacity of over 1.0 Tbps to protect your business from even the largest DDoS attacks. It can run continuously to monitor all traffic and stop attacks from ever reaching your network, or it can be initiated on demand when your site is under DDoS attack.1.4KViews0likes1CommentF5預測:智慧應用網路趨勢 教育邁向個人化
This is a localised version of the original article here. 科技改變了所有產業,教育也不例外,教育課題從未像今天這樣受到關注。我相信大家都同意教育已歷經了重大的改變,學生和教師不再像以前那樣被局限在一間掛著黑板的教室。 現在,網際網路成為主要的促成機制,學生藉由它聚集在一起,傳播理念和發掘經濟機會。教育資源已成為一個熱門的主題,對學生的學習方式帶來改變。Johns Hopkins大學教育研究與改革中心教授Steven Ross認為,運用資料建立客製化教育將成為未來促成學生學習的關鍵。這項科技革命產生了大量的線上學習課程,讓任何人都可以透過智慧型裝置存取。 哈佛和MIT針對大規模網路免費公開課程(massive open online course; MOOC)所做的二年評估發現,68個MOOC共有170萬筆課程註冊[2]。相當於約100萬參與者,平均每人參加1.7個課程。 毫無疑問的,此種公平教育為全球學生提供了龐大的機會,並且改善他們獲得教育的方式。iOS和Android等平台提供超過50萬個app,讓教師與學生都能輕易取得任何主題的數位資源。 教育隨著數位年代的發展而改變,以下幾點是教育機構應注意的: 應用為中心的規模與安全性 眾多MOOC供應者例如Coursera和edX的出現,已改變了今日教育的傳統地理和科技藩籬。數位學習將繼續成長,而人們也更加需要一個具備親和性的無縫學習環境。 再者,教育科技的發展也為政府和企業帶來新機會。如果這些組織有能力可以快速延展並順應嶄新的數位世界 - 讓資訊服務更容易提供、取得並確保安全,那將是最有效率的方法。 許多教育機構擁有一如大型跨國公司的龐大使用者數量,而在應用的交付上也面對了延展方面的問題。現在的目標不再是如何設法讓學生獲得快速連接,而是要如何快速的配置和提供內容服務,以及建立無縫接軌般的使用經驗。 傳統方法不再能夠為我們的客戶提供所需的水平延展。他們需要一個智慧化且彈性的架構,以支援部署和管理應用與資源。因此,現在的關鍵在於必須建構一個以應用為中心的基礎設施,讓課程能夠快速提供給用戶群,並且確保整體環境的使用者存取與流量安全。 無縫存取連接性的確保 我們生活在Y世代,對於任何人任何事都要求高度的便利性與速度。 對於便利的要求,也涵蓋了將教育提供給學生的方式。再者,物聯網(Internet of things; IoT)已開啟了全新的可能性,讓教師有更多方法可以教育他們的學生。 不論教育與學習是否透過連網裝置例如Smart Board或iPad為之,最重要的是必須確保資料與內容的無縫存取。我們對於網際網路頻寬越來越依賴,學生頻繁利用Web,因此教科書已不再是主要的教育方法。此種改變讓教育機構能夠根據他們收集到的學生與課業資料,建立更具個人化的課程。 安全責任與義務 雲端技術持續測試和改變全球教育。教育機構選擇一種集中化的服務模型,可以輕易的從中選擇希望提供給學生的服務以強化學習經驗。 因此,教育機構對於內容的選擇以及學生取得服務的方式,必須肩負安全責任與義務(duty of care)。他們可以透過政策,藉由強化的使用者身分識別與存取權限以確保將正確申請課程內容提供給各申請學生。 透過對app安全性的強化,教育機構將可以有效防護其環境的惡意程式與病毒威脅。教育者可以確保學生只取得他們確實希望取得的內容。 F5提供解決方案 BIG-IP LTM為教育組織提供一個穩固的礎石,支援配置、優化和交付服務。它讓教育機構能夠以一種快速且高時效的方式,在一個控制且安全的環境將應用發行到網際網路。F5方案提供所需的效能和水平延展能力,以確保最高層級的資料吞吐效能。 同時,BIG-IP APM讓學校能夠運用虛擬桌面基礎設施(virtual desktop infrastructure; VDI)應用,向上與向下延展而無需安裝昂貴的VDI閘道,並且提供集中化的安全性。再者,學校可以開發客製化iApps以便快速且一致的交付應用,以及以一種安全、無間隙且可管理的方式為那些已發行到網際網路的應用進行重新組態。 BIG-IP Application Security Manager (ASM)提供一個應用層安全性,保護重要的教育資產以及持續發行的應用和內容。ASM允許教育機構建立量身訂製的安全政策,無間隙的保護每一個應用,確保所有應用都能以安全的方式交付。 明日數位化的教育 我們很難不察覺科技對教育所造成的深遠衝擊。數位年代的科技建立了一種新層級的個人化學習。 教育數位化的時機已成熟,科技必須站在第一線確保內容與資料的安全、延展和交付。 科技促成的公平教育,協助解決教育的取得途徑、語言、經濟、距離和公平性等問題。再者,它破除了地理疆界,在妥善的政策保護下,促成高品質教育的大規模普及。253Views0likes0CommentsF5 IoT Ready平台
This blog is adapted from the original posthere. “物聯網“的應用與支持物連網服的各項應用程式正在改變著我們的生活方式。研究顯示運動與健康相關產業部門到2017年有41%的年增長率,將增長到近170萬台設備,在未來幾年隨著越來越多的設備、服裝或感應器成為司空見慣的的事情,職場工作模式的變化將是一個巨大的挑戰。 由於物聯網世代需要更多的應用程式來運行,訪問流量需要服務也必須更快配置,一個可靠強大的、可擴展的智能基礎設施將成為必要的關鍵。IT專業人員的任務是設計和建造的基礎設施已經準備好為未來的挑戰,包括物聯網。為了確保安全、智能路由器和分析等需求,網絡層需要精通基礎架構設備上使用的語言。了解網路中的這些協議將允許流量進行安全保障、,優先層級等與路由器相對應,進而做出更好的規模和設備的流量和數據的管理。 由於F5應用服務分享一個共同的控制面(F5平台),因此我們已簡化了IoT應用交付服務的部署與優化程序。藉由軟體定義應用服務(Software Defined Application Services; SDAS)所提供的彈性功能,我們可以快速的將IoT應用服務配置到資料中心和雲端運算環境,節省新應用與架構部署的時間和成本。 SDAS吸引人的地方在於它可以提供整體性的服務,根據IoT裝置的服務請求、情境與應用健康狀態,將IoT導引到最適當的資料中心或混合雲端環境。因此,客戶、員工與IoT裝置本身都能獲得最安全且最快速的服務經驗。 F5高效能服務架構支援傳統和新興的基底網路。它可以部署一個頂級的傳統IP與VLAN-based網路,利用NVGRE或VXLAN (以及其他較不為人知的疊層網路協定)以與SDN疊層網路(overlay network)搭配作業,以及整合例如Cisco/Insieme、Arista和BigSwitch等廠商的SDN網路。 硬體、軟體或雲端 服務架構模型(services fabric model)支援將眾多服務統合到一個可以部署在硬體、軟體或雲端的共同平台。這讓我們可以藉由建立標準化的管理與部署程序,以支援持續的服務交付並降低營運上資源負荷。透過服務資源的分享以及運用細緻分級的多租戶(multi-tenancy)技術,我們可以大幅降低個別服務的成本,讓所有IoT應用(不論規模大小)都能享有有助於提升安全性、可靠性與效能的服務。 F5平台: 提供網路安全性以防範內傳流量(inbound)攻擊 卸載SSL以改善應用伺服器效能 非僅了解應用並且知道它何時出現問題 非僅確保最佳終端使用者經驗並且提供快速且高效率的資料複製 F5雲端方案可以在傳統和雲端基礎設施之間為IoT應用交付服務提供自動化部署與協調,並且動態的將工作負荷重導至最適當的地點。這些應用交付服務確保可預測的IoT經驗、安全政策複製以及工作負荷敏捷性。 F5 BIG-IQ™ Cloud可以建立跨越傳統與雲端基礎設施的F5 BIG-IP®方案聯合管理,協助企業以快速、一致且可重複的方式來部署和管理IoT交付服務,而不論基底的基礎設施為何。再者,BIG-IQ Cloud能夠整合或者與既有的雲端協調引擎(例如VMware vCloud Director)互動,簡化整體應用部署程序。 延伸、延展與安全 F5雲端方案提供一個快速應用交付網路(Application Delivery Network)配置方案,讓企業能以大幅縮短的時間跨越資料中心(不論私有或公共)擴充IoT交付能力。因此,企業能夠有效的做到包括: 延伸資料中心至雲端以支援IoT部署。 於有需要的時候,將IoT應用延展至資料中心以外。 確保安全並加速IoT與雲端的連結。 當有維護的需要時,企業不再需要以人工方式組態應用以重導流量。相反的,IoT應用可以在實施維護之前,主動的重導至一個替代的資料中心。 在持續性的DDoS保護方面,藉由F5 Silverline雲端平台提供的F5 Silverline DDoS Protection服務能夠偵測並舒緩最大量的DDoS攻擊,避免危及你的IoT網路。 BIG-IP平台具備應用與地點獨立性,這意謂著不論應用類型為何或者應用駐留在什麼地方都無所謂。你只需要告訴BIG-IP平台到何處尋找IoT應用,BIG-IP平台就會達成交付程序。 F5新融合架構(F5 Synthesis)將這所有整合起來,讓雲端與應用供應商以及行動網路運營商擁有所需的架構,以確保IoT應用效能、可靠性與安全。 連結裝置將持續發展,促使我們跨入這個幾乎任何東西都會產生資料流的嶄新世界。雖然需要考慮的層面還很多,但是企業若能主動迎接挑戰並採納新的方法以促成IoT-ready網路,將能開啟一個邁向成功的明確路線。 一個IoT-ready環境讓IT能夠開始掌握此種轉變所蘊含的效益,而不需要對既有技術進行全面性的汰換。它也提供IT所需的緩衝空間,確保持續湧現的連結裝置不會癱瘓基礎設施。這個程序確保其效益可以被實現,而不需要為了維護IoT網路、資料和應用資源的可用性與安全而在營運治理上做出折衷。它也意謂著IT可以管理IoT服務而非機器。 不論一個IoT ready基礎設施如何建構,對於IT與商務上而言都是一種轉型之旅。這不是一件可以掉以輕心或忽略長期策略的轉變。若能採取適切的部署程序,F5的IoT ready基礎設施將能為企業及其員工帶來顯著的效益。351Views0likes0CommentsOn Cloud Nine: Lucky 7 questions you have about Singapore’s journey to becoming a Smart Nation
The Infocomm Development Authority (IDA) wants to make Singapore the world’s first Smart Nation, and this vision means connecting devices, things and people to provide better quality of life in an era of mobility, urban density, aging population and so on. IDA's executive deputy chairman, Steve Leonard, has said that when tackling difficult urban challenges in areas such as healthcare and energy, enterprises in Singapore need to capture and analyze massive amounts of data, and use that situational awareness to take meaningful actions (link). From a technology perspective, cloud has reached a tipping point in the enterprise. An exciting new era of cloud deployments is being ushered in, one characterised by high levels of flexibility, agility and innovation. Today, cloud is no longer just a buzzword, but an integral fabric of the modern enterprise. Conversation nowadays have shifted from cloud deployments to optimizing those resources and thus improving the overall user experience. Singapore’s Smart Nation vision has entered the “build” phase. What gives? The focus on infrastructure and services will serve as the nation’s framework. There are three areas of innovation: Smart Logistics, Smart Nation Tech Challenges and Smart Health-Assist. The vision to connect devices, things and people is a grand one, and starts with ensuring the integrity of the nation’s framework is built on a strong foundation. Applications and connectivity are at the heart of this vision and the technologies enabling flow of information are increasingly cloud-based. Enterprises are fast adopting a hybrid-cloud infrastructure, so sensitive data can be stored in a private cloud while the public cloud can be leveraged for computational resources to provide for the running of less critical applications. 2.To cloud or not to cloud? – That is the question! As early as 2013, 83% of Singaporean companies felt they have already experienced the financial advantages of cloud deployments. This is 16% more than the global average (link). The journey of cloud adoption is aligned with the Smart Nation Initiative and Singapore is a significant investor in cloud adoption. State initiatives aside, a question to ask is “to cloud or not to cloud”? The many benefits of cloud adoption include quicker disaster recovery times and increased collaboration amongst employees since they are able to sync up and work on documents and shared apps simultaneously. All these can only result in a positive business impact as productivity goes up. More importantly the cloud provides for business agility allowing companies to scale up and down their information infrastructure in a relatively short time frame, sometimes with the benefit of paying for capacity that is being consumed. “Pay to use” versus “Buy to Depreciate” provides for a better financial argument which generally goes well with CFOs. As technologies such as IoT become mainstream and as Singapore moves forward to becoming a Smart Nation, the correct question to ask is “How do we effectively deploy and maximise the potential of cloud?” Right…so, how can we fully maximise the potential of cloud and turn them into a positive business impact? Business has reached the tipping point of cloud computing with the utilisation of cloud both inside and outside the enterprise. To fully maximize the potential of cloud, there are 4 notable considerations for an enterprise cloud strategy. Applications: Companies today run a remarkable number of workloads within their IT environments, with some enterprises running more than 100 concurrently. Most of these applications demand differing sets of requirements and characteristics. However, as cloud-based services start to demonstrate the capability and maturity to run core workloads, confidence in off-premise solutions is increasing. The result, today’s enterprises are gaining more confidence in migrating critical workloads to a cloud environment. Business Decision-makers: The self-service nature of cloud solutions is starting to evolve decision-making process away from IT, and into one that involves multiple stakeholders and business leaders. More and more, departmental heads will play major role in identifying needs and shortlisting cloud solutions. Compliance/risk directors then need to take the lead in evaluating solutions and manage risks, while the entire C-suite make the final purchase-decision. Customers: Cloud, and indeed IT in general, has traditionally focused on internal enterprise and benefits such as cost savings, resource optimization and business agility. However, this ignores a key segment of IT user pool – the Customer! Forward-thinking businesses are now beginning to evaluate what cloud means to their customers and how they can leverage it to enhance the customer experience. Defence: Security and privacy of IT environments are perennial topics to any cloud discussions, whether it is about apps, business or customers. Security is often highlighted as the biggest impediment in adopting cloud services or choosing service providers. Security considerations should never be an afterthought to any cloud migration planning and should be considered and deliberated extensively prior to any move to the cloud. A “security-first” approach to a cloud strategy will ensure that the move to the cloud does not cause any major operational or internal policy issues as well as ensure a smooth customer experience. This should be complemented with a “follow the apps” defensive posture where the app security services should be fronting the application wherever it resides. Where’s the future of cloud headed? From optimization to orchestration. Today, the primary use of cloud services is to optimize and streamline conventional business processes. This will change. Enterprises will next leverage cloud services to automate business processes and drive business transformation. There will also be more collaborative decision-making in cloud service procurement. The role of the CIO is set to shift from information to innovation. With the inclusion of customers in the IT user pool, enhancing customer experience through high availability and performance of business apps is crucial. Cloud will continue to evolve. 5. Is Cloud safe? As more applications and technology becomes increasingly cloud-based, especially as we mature into a Smart Nation, how can we ensure information transfer over Cloud is safe? Every battle is won before it is fought, says Sun Tzu. This is also the philosophy undertaken by Singapore in the march towards being a Smart Nation. And security continues to be one of the largest barriers to cloud adoption. It is also a key consideration in a hyper-connected environment and the prolific use of applications adds an additional layer of challenge. Organisations generally do a decent job securing their infrastructure but face challenges when securing applications regardless if these applications are hosted in-house, in a cloud environment or both. The security strategy should encompass considerations at the network/infrastructure area, applications and web assets, endpoints and devices, users behaviours. Security is everyone’s business and a foresight consideration. How can Cloud benefit enterprises as Singapore moves to become a Smart Nation? Companies are investing in cloud and using it for competitive reasons. 77% of senior information technology executives have placed high importance on digital transformation and count it as a key factor for driving the business growth of their organisations (link). Improving operational excellence and customer experience are some of the reasons why cloud adoption is on the rise. Innovations in IoT are evolving and continue to shape how people use and interact with the technologies. New devices will emerge and the technologies will evolve with these devices which in turn will shape how information is being delivered to users. In a Smart Nation where hyper connectivity is at the heart of everything, accessing information and applications in a secure and seamless manner is key and cloud will play a crucial part in its success. OK, so Cloud deployment and Smart Nation: they are highly intertwined but the investment outlay and management complexity remains a key barrier. How can we efficiently manage this? It is a common perception associated with the build out of a cloud strategy but the key consideration is knowing how applications are being consumed and the corresponding services they need. In reality, not all applications will be delivered from the cloud due to the nature or the intent of the application, especially if there is a high level of data sensitivity or the need for high operational in house secure management. We will likely see the emergence of a hybrid cloud architectures requiring seamless management and orchestration services with a balanced security posture both in house and in the cloud. This will be especially applicable for the delivery of citizen services in an aspiring smart nation like Singapore where mobile and internet penetration rates are high and technology adoption is prevalent in every aspect of our daily lives. The expectation for service on demand will increase as IoT adoption becomes mainstream and becomes interconnected with the social platforms. Architecting the infrastructure from this perspective allows for better and efficient management and reduce costs in deploying cloud. Organisations and Governments alike are already starting to build out their own cloud strategy in an attempt to drive business growth and national transformation. In an increasingly connected world where mobility is driving productivity and consumption of information, cloud adoption in a hyper connected Smart Nation will spur productivity and improve customer satisfaction, with the right consideration and strategy. At the end of the day, a cloud strategy is just one of the many means to an end – an end to become a smart nation, a nation where the citizens and corporations alike are empowered to harness technology for driving growth.250Views0likes0CommentsAgility Australia set for success
With less than 24 hours to go before we officially kick-start Agility Australia in Melbourne, preparations are fast under way to ensure this year is its most successful year to date. Agility Australia is the local version of F5 Agility, which is an annual global event for F5 leaders, customers, and partners to share how its latest solutions are transforming what’s possible for today’s organisations. The aim of the event is to showcase how F5 is bringing the power of cloud, data centres, converged systems, and as-a-service together to enable fast, efficient, and secure application delivery in today’s challenging hybrid environments. Most importantly, the event provides an opportunity for F5 to provide its local stakeholders with key updates and announcements, in addition to expert insights that will help partners and customers to identify the best software and hardware solutions in the market to meet their business needs. In addition to the announcement of an update to F5’s BIG-IP®with the launch of its version 12.0, F5 will also be revealing the results of a new survey – ‘APAC State of App Delivery’. Best of luck to the F5 executives and sales teams for an enjoyable and winning event! More to come from the F5-ers over the next few days!335Views0likes1CommentIT安全性不能以一種方案「一體適用」
This is adapated from the original post by Matt Miller. 今天的安全局勢具有高度複雜化的傾向,原因大致上可以歸咎於日益複雜化的網路攻擊本質,特別是從管理者的觀點來看。例如,分散式拒絕服務攻擊(DDoS)現在已達到400Gbps速度,目標包括網路和應用層。很顯然的,攻擊者持續進化,開發其他方法來繞過包括防火牆等傳統安全防護。 對於面對應用層DDoS攻擊威脅的企業而言,必須克服的挑戰在於如何區分人類流量與魁儡(bot)流量。 再者,攻擊背後的動機越來越複雜,特別是從政治與經濟觀點而言。例如,美國國家安全局(NSA)洩密案 - 前僱員Edward Snowden洩漏了包括美國、英國、澳洲、加拿大和紐西蘭等國政府的機密資訊 - 此一事件確實提醒了我們必須重視駭客活動。另外,現在IT安全的最大威脅之一就是組織化的網路竊盜與詐欺,因為那些聰明的犯罪者越來越了解可以藉由線上犯罪獲取可觀的財務利益。 因此,確保擁有適切的防護以杜絕網路攻擊,已成為企業的一項關鍵課題。一個有效的安全策略必須涵蓋員工存取的所有裝置、應用程式和網路,並且跨越企業本身的基礎設施。傳統安全方法例如新一代防火牆和被動回應的安全措施,已無法有效的對抗新類型的攻擊。現在的安全性非常重視對於應用程式的保護,以及使用者身分識別的加密和保護措施,而比較不偏重於基底的網路基礎設施。這是因為網路基礎設施已演變得比較沒那麼靜態,並且也已被證明它只是用來運行複雜應用程式的一個載具。 企業需要的是一個彈性且完整的安全策略,必須有能力將DNS安全性與DDoS保護、網路防火牆、存取管理、應用安全性等結合智慧型的流量管理。 Frost & Sullivan的一項報告(Frost Industry Quotient)指出,市場呈現了朝Web應用防火牆(Web Application Firewall; WAF)與應用交付控制器(Application Delivery Controller; ADC)平台整合的發展趨勢,而這促使F5針對應用交付市場開發了一個稱為F5新融合架構(F5 Synthesis)的新觀點。此一觀點提供了一個高效能分散網路架構(high performance network fabric),為一個應用的基本單元(網路、DNS、SSL、HTTP)提供保護以防範複雜的DDoS攻擊威脅。 F5新融合架構透過業經測試的參考架構,在客戶朝軟體定義資料中心(software defined data centres; SDDS)轉移的過程中確保應用安全與可用性。再者,F5的DDoS防護方案提供目前市場上最完備的攻擊防護。DDoS攻擊的平均速度達到2.64 Gbps,而升級到F5的BIG-IP平台後,伺服器將能處理高達470 Gbps的攻擊威脅。這不僅提供了充裕的頻寬以舒緩DDoS攻擊,而且其額外的容量讓線上公司可以維護正常的商務營運 - 即使是在遭受攻擊的期間。 安全性不再是一種「一體適用」的方案。終端使用者期望擁有高效能服務,而企業必須確保他們所部署的安全方案不會變成一個瓶頸。我們可以預期見到多維(multi-dimension)或「雞尾酒」式的攻擊出現,亦即DDoS攻擊結合應用層攻擊與SQL安全弱點威脅。因此,傳統防火牆不再是一個有效的安全防衛,企業需要採行一種多堆疊的安全方法,並結合內部控管程序。面對來自不同裝置和多重面向的攻擊威脅,單一用途安全設備將被高功能的多用途設備取代。238Views0likes0Comments새로운 모바일, 하이브리드 세상의 접근 관리
This post is adapted from Jay Kelley's original entry. 기업 환경에 완전히 새로운 세상이 출현함에 따라 ‘새로운 표준’들과 새로운 기회가 생겨나는 반면, 기업들은 조직 전체에 전광석화처럼 다가올 새로운 도전과제들과 마주하게 되었다. 오늘 날 그리고 미래의 근무환경은 계속해서 모바일 중심으로 나아갈 것이다. 모바일 근로자의 수만큼 모바일 디바이스가 두 세배로 증가하게 될 것이라는 전망은 말할 것도 없는 명백한 사실이다. IDC가 2015년 연말에 이르면 전 세계 노동력의 37%가 모바일 근로자가 될 것이라고 분석하였고 이는 전 세계적으로 13억 명의 모바일 근로자가 올해 안에 생긴다는 뜻이다. 오렌지 비즈니스 서비스(Orange Business Services)에 따르면, 2018년에 이르면 전 세계 IP 트래픽의 55%가 모바일 비즈니스 인터넷 트랙으로 인해 발생할 것이라고 한다. 즉, 모빌리티는 현재 진행되고 있으며 우리 생활의 일부가 되었음을 알 수 있다. IDC는 아시아 태평양 지역의 BYOD(Bring your own device) 디바이스 시장이 계속해서 활발한 성장세를 이어나갈 것으로 예상했다. 2014년 아태지역 내 BYOD 관련 디바이스의 숫자는 스마트폰 1억 5천 5백만개, 태블릿PC 4백만개 이상을 기록하였다. 이는 전년 대비 각각 40.4%, 62.7%씩 성장한 숫자이며 현재 급증하고 있는 웨어러블 디바이스는 포함되지 않은 수치라는 것을 감안했을 때 매우 큰 수치이다. 모바일 인력이 빠르게 증가하고 기업 내에서 사용하는 스마트폰, 태블릿PC, 웨어러블 기기들이 폭발적으로 증가함에 따라, 기업 내에서 사용하는 클라우드 및 SaaS 기반 애플리케이션의 증가 속도 또한 맹렬하게 치솟고 있다. 클라우드 애플리케이션 제공업체인 스카이하이 네트웍스(Skyhigh Networks)의 최근 조사에 따르면, 오늘 날 기업들이 사용하고 있는 클라우드 서비스는 759개에 달한다고 한다. 가장 당혹스러운 것은 현재 사용 중에 있는 클라우드 애플리케이션 및 서비스의 규모가 크다는 점이 아니다. 클라우드 보안 연맹(Cloud Security Alliance)의 연구에 따르면, 문제는 대부분 기업의 IT 부서는 그들이 사용 중인 클라우드 기반 애플리케이션이 50개 이하라고 생각한다는 것이다. 즉, 기업마다 평균 700개 이상의 클라우드 애플리케이션 및 서비스를 사용하고 있지만 아무도(사용자 또한) 애플리케이션 및 서비스에 대한 관리를 하고 있지 않으며 어떠한 기업 정보도 공유되지 않고 있다는 사실이다. 문제는 이렇게 알지 못하는 문제점에 대해서는 예방조차도 되지 못한다는 사실인 것이다. 결국, 기업들에게 있어 “새로운 표준”이라는 혼란스러운 퍼즐의 마지막 조각은 바로 호스티드 프라이빗, 공공 및 클라우드 인프라와 함께 데이터센터와 클라우드 기반 애플리케이션 및 데이터가 절묘하게 조합된 하이브리드 네트워크이다. 가트너는 “실제 하이브리드 클라우드 컴퓨팅의 구축 사례는 찾아보기 어렵고, 대기업들의 4분의 3은 2015년 이내에 하이브리드 클라우드를 구축하길 기대한다”고 분석했다. 모바일 인력이 인프라 변화를 가져오는 것을 감안할 때 더욱 다양한 디바이스 생태계의 문제 해결에 대한 필요성도 제기되고 있다. 모빌리티를 해결한 인프라는 팽창하고 있는 디바이스 생태계를 지원하기 위한 클라우드 기반의 애플리케이션 및 서비스에 대한 더 큰 규모의 투자를 필요로 한다. 그러므로, 당분간 가까운 미래 네트워크의 트렌드는 하이브리드 형태가 될 것이라는 것을 알 수 있다. 모빌리티, 클라우드 및 하이브리드 네트워크의 “새로운 표준”을 통해 네트워크, 애플리케이션 그리고 데이터 접근성을 어떻게 해결할 수 있을까? 모바일 디바이스이자 기업 통제 아래 있는 새로운 디바이스들은 넘쳐나고, 애플리케이션 및 데이터는 네트워크와 다양한 클라우드 및 SaaS 구축 기반에 흩어져 있는 상태에서 기업들은 어떻게 신속 적합하고 인증 및 승인된 접근을 확인할 수 있을까? 이렇게 다양한 변수들 속에서도 변함없는 한 가지는 바로, 개인정보이다. 사용자 그리고 그들의 개인정보는 현재 그리고 앞으로도 기업에게 있어 틀림없는 “새로운 경계선(방어선)”이 될 것이다. 기존 네트워크 경계가 사라지거나 대부분의 경우 여러 부분으로 흩어지면서 새로운 경계로 등장한 것이 바로 개인정보이다. 애플리케이션, 데이터 그리고 네트워크까지 클라우드로 빠르게 나아감에 따라, 사용자가 관리하고 BYOD가 주도하는 모바일 생태계는 기하급수적으로 팽창하고 있다. 또한 기업의 관리는 더욱 어려워지고 광범위해졌으며 외부에 더욱 의존하게 되었다. 문제는 이들 외부업체가 대부분 보안에 대한 충분한 지식이 없거나 무관한 업체라는 점이다. 그럼에도 사용자 개인정보 문제는 전혀 개선되지 않고 있다. AAA 기술(authentication, authorization 및 accounting)의 뒷받침으로 개인정보는 이제 안전한 기업 접속 방어의 최전선에 위치하고 있다. 그러나, 개인정보는 접근권의 새로운 매개변수를 관리하는 방법의 일부분이다. 사용자 접근 요청의 내용, 접근 요청 시의 환경은 개인정보에 버금가며, 논의할 것도 없이 개인정보처럼 적합한 접근을 보장하는 것과 관련된 것이다. 누가, 언제, 어디서, 무엇을 어떻게, 왜라는 육하원칙을 해결하는 능력이 네트워크, 클라우드, 애플리케이션, 데이터 등이 어디에 있고 어떻게 구성되어있던 간에 안전한 접근을 보장하고 강화하고 차별화한다. 사용자의 개인정보를 네트워크, 클라우드, 애플리케이션, 데이터 등 어디에서나 효율적이고 안전하게 공유될 수 있게 보장하는 것은 이제 필수적인 사항이 되었다. 그러나 여전히 개인정보 사일로(silo), 클라우드 기반 그리고 SaaS 기반 애플리케이션 및 데이터 등의 온프레미스 개인정보 그리고 여러 사용자 이름과 비밀번호로 사용자들을 피로하게 하는 암호 피로도와 같은 해결과제들이 남아있다. 바로 이 지점에서 개인정보 브릿지가 활용될 수 있다. 페더레이션은 SAML과 같은 업계 표준을 통해 네트워크, 클라우드, 애플리케이션 등의 양자간의 신뢰할 수 있는 사용자 개인정보 망을 구축해준다. 개인정보 디렉토리의 번거로운 중복과 삽입은 더 이상 불필요한 사항이 되었다. 개인정보와 접근은 기업과 클라우드 및 SaaS 제공업체들 사이의 인증을 통해 기업에 의해 관리되고 있다. 일시적인 사용자 인증과 만료는 한 곳으로 집중되어 기업이 관리할 수 있다. 아이덴티티 페더레이션은 접근 가시성과 관리 기능을 함께 제공해준다. 기업들에게 접근 관리를 위한 개인정보보호 활용과 개인정보보호 브릿지 설정은 이제 반드시 거쳐야 하는 단계가 되었다. 애플리케이션이 기업 도메인의 외부로 이동하고 내부 인력과 디바이스가 모바일화되어 기업 내부에 머무르지 않으면 기업 도메인 또한 이동했기 때문이다. 모빌리티, 클라우드 및 하이브리드 인프라. 기업들이 피해나갈 수 없는 이 “새로운 표준”을 위한 보다 적극적인 기업의 준비와 전략이 필요한 때이다.210Views0likes0Comments新行動化混合世界的存取控制
This post is adapted from Jay Kelley's posthere. 企業正跨入一個嶄新的世界。許多新的典範和「淘金熱潮」般的新機會出現在眼前,但同時也伴隨著新的挑戰,它們如同閃電般的貫穿企業組織。 今天乃至於未來的工作人口仍將繼續朝行動化發展。根據IDC調查,全球37%工作人口將在2015年底邁入行動化。這相當於全球有13億行動工作者,當然行動裝置數量將是這個數字的二或更多倍。再者,Orange Business Services報告指出,到了2018年,全球55%的商業IP流量將屬於行動商業網際網路流量。行動化時代已來臨,並且將繼續存在。 IDC預期亞太地區的攜帶自有裝置(bring your own device; BYOD)市場將繼續呈現強大成長。根據2014年調查,亞太區估計有1.55億支智慧型電話和超過400萬台平板電腦在使用中,而年成長率分別為40.4%和62.7%,形成支撐BYOD趨勢的基礎。而且,這項預測還沒包括新興的穿戴式裝置。 行動人口如火箭衝天般的加速成長,智慧型電話、平板電腦和穿戴式裝置大量湧現,這些現象使得雲端和軟體即服務(SaaS)應用數量呈現令人驚訝的成長速度。根據SkyHigh Networks最近的調查,今天的企業平均使用759種雲端服務。然而,最讓人困惑的並不是這些雲端應用與服務的數量。根據Cloud Security Alliance的一項調查,大多數企業IT團隊相信他們使用中的雲端應用少於50種。也就是說,平均超過700種雲端應用與服務在企業內使用 - 但除了使用者本身之外,沒有任何人可控制那些應用、服務、以及在其上分享的企業資訊。問題是,你無法捍衛那些你並不知道的東西! 最後,企業新典範的最後一片拼圖就是混合網路(hybrid network),亦即藉由一些代管私有、公共與雲端基礎設施,將資料中心與雲端應用和資料混合在一起。Gartner報告指出「儘管實際的混合雲端運算部署相當稀少,但將近四分之三的大型企業預期將在2015年擁有混合部署」。行動工作人口將帶動基礎設施改變,需要處理更分散化的裝置生態系統。而支援行動化的基礎設施則需要在雲端應用與服務方面投入更大的投資,以支援擴充中的裝置生態系統。因此,可以預見的是,混合網路將在可見的未來成為主流。 面對新典範的行動化、雲端與混合網路,企業如何解決網路、應用與資料存取問題?如此眾多行動化但僅受到公司有限度管控的新裝置,加上散佈在網路、各種雲端與SaaS環境的應用與資料,企業該如何確保快速、適當、驗證與授權的存取? 在這麼多變數當中,有一項常數仍維持不變:身分識別。使用者(和他們的身分識別)將成為今天與未來的企業「新疆界」。 傳統網路邊界已被破除、斷片化、甚至瓦解成許多小片段,身分識別因此變成新的邊界。應用、資料、甚至網路都快速朝雲端轉移,使用者控制的BYOD行動生態系統呈指數成長,這些無不使得企業管控變得更為困難、分散、並且必須仰賴他人維護 - 而很多情形下,這裡所指的「他人」正是那些對於安全性欠缺警覺或者不關心的使用者。然而,使用者身分識別永遠不會改變。透過認證、授權與計費(authentication, authorization, and accounting; AAA)機制,身分識別已成為現在確保企業存取安全的第一道防線。 不過,身分識別只是管控存取的先頭部隊。使用者請求存取的當下情境,以及他們提出存取請求時所處的環境,同樣都是確保安全存取的要素。若能夠適當的管控「何人」、「何事」、「何時」、「何地」、「為何」與「如何」,就可以確保、強化和區分使用者對網路、雲端、應用與資料的安全存取,而不論那些資源駐留在何處或如何組成。 確保有效率且安全的在網路、雲端、應用程式和資料之間分享使用者身分識別(不論他們身在何處),是現在的一項必要工作。然而,這有許多挑戰,例如身分識別孤島、雲端與SaaS應用和資料的企業內部(on-premise)身分識別、以及使用者密碼疲勞(導致較弱的使用者名稱與密碼)等都很容易被破解。解決之道就是要構築一個身分識別橋梁。聯合識別(federation)透過業界標準例如SAML,在網路、雲端、應用程式之間建立一個信任的鏈結,不再需要繁雜的身分識別目錄複製與插入。身分識別與存取由企業管控,並且在企業、雲端與SaaS服務供應商之間進行認證。企業能夠集中化的管控使用者認證與終止。聯合識別提供了存取能見度與管控能力。 利用身分識別進行存取控制以及識別橋梁的建立,是企業現在必須做的工作,因為應用程式轉移到企業領域之外,工作人口和他們的裝置日趨行動化並且群體離開企業,而企業領域本身也已移動。這就是新典範。225Views0likes0Comments榮耀得獎 謙卑服務 - F5榮獲多項亞太獎賞
This blog post is adapted from the original post in Englishhere. 最近,F5在亞太屢獲獎賞。四項大獎的獲得,明確證明了F5持續的市場與技術領導性。F5一直致力於提供全方位的客戶經驗,並且很榮幸的獲得許多業界專家與分析師對於我們的肯定。這些獎賞屬於亞太區每一位F5員工的榮耀。F5全心支持我們的夥伴成長,並且為客戶提供方案與服務,這些努力讓F5從平凡的廠商茁壯成為一個在企業混合環境為數千應用提供優化與安全的可信賴夥伴。 F5今年從Frost & Sullivan獲得象徵應用交付控制器(Application Delivery Controllers; ADC)領導地位的大獎。這對於F5是一項非常特別的榮譽,因為這是我們第七年獲得Frost & Sullivan亞太資通技術獎(Asia Pacific ICT Awards)評選為年度最佳ADC廠商 - 這是一項令我們重視但不能因此鬆懈的成就。這個獎賞的頒贈是由分析師透過深入的訪談、分析以及廣泛的輔助研究而決定,評估的項目包括營收、市佔率、能力、以及對於業界的整體貢獻。 F5已從資料中心根源茁壯成長,成為提供強大混合方案技術的公司,從專門用途的硬體到服務方案。在Network World Asia的2015資訊管理獎(Information Management Awards 2015)評選活動中,F5很榮幸獲頒年度最佳應用交付控制器獎。應用已成為大多數商業交易的核心,這使得企業面對新的挑戰,必須延伸他們IT基礎設施的管理以涵蓋駐留在雲端的應用程式。我們掌握了比以往更優勢的定位,協助企業降低複雜性並擁抱混合基礎設施部署,而不會讓我們的客戶犧牲他們原本在資料中心享有的效益。 今年的一個重要里程碑是,我們藉由F5 Silverline平台的推出而跨入雲端服務交付市場。安全性是F5的DNA。今年,我們從Computerworld Malaysia和Network World Asia獲得的獎賞,反映了我們固若磐石的DDoS保護技術。這二個獎賞都是由終端使用者組織的區域資訊長(CIO)和IT主管參與票選。印證了F5在保護企業免於安全弱點和網路威脅上的能力與績效。 這些獎賞肯定了我們在產品開發各個階段所抱持的嚴謹態度,從原始構想到終端使用者經驗與支援。熱潮過後,我們將繼續與企業合作,以最好的方案協助他們達成目標。現在,我們將開啟香檳,為我們的勝利乾杯!215Views0likes0Comments