Load Balancing to Only One Pool Member
I have an issue where all traffic in a pool is going to the fifth of 5 pool members. We are using cookie persistence and I know there can be issues with that. We are also using both an http and OneConnect profile. From the sols and DC articles I've read it seems like the problem will arise if you do NOT have a oneconnect profile assigned. I have tried pulling http/oneconnect/tcp profiles on and off, using default profiles. The only thing I haven't tried is falling back to source address persistence. That is a last resort I do not want to use. Due to the application architecture source address persistence will definitely result in uneven load. All the "custom" profiles are built from an F5 guide for the application (Epic HyperSpace Web; Link to Guide). That being said this config seems pretty straight forward, but any help would be very much appreciated. We have captured traffic and seen the cookies present in the sessions. Below is the config. ltm virtual /PARTITION/v_80 { destination /PARTITION/10.10.1.1:80 ip-protocol tcp mask 255.255.255.255 persist { /PARTITION/Custom-cookie { default yes } } pool /PARTITION/pool_80 profiles { /PARTITION/Custom-OneConnect { } /PARTITION/Custom-http { } /PARTITION/Custom-lan-optimized { } } source 0.0.0.0/0 source-address-translation { type automap } translate-address enabled translate-port enabled } ltm pool /PARTITION/Pool_80 { description "HTTP Pool" load-balancing-mode least-connections-member members { /PARTITION/001:80 { address 10.1.1.1 } /PARTITION/002:80 { address 10.1.1.2 } /PARTITION/003:80 { address 10.1.1.3 } /PARTITION/004:80 { address 10.1.1.4 } /PARTITION/005:80 { address 10.1.1.5 } } monitor /Common/http_head_f5 service-down-action reselect } Only change to custom oneconnect profile is mask is 255.255.255.255. Only change to tcp-lan-optimized profile is the idle timeout is set to 1200s. Only change to http profile is that 'Redirect Rewrite' is set to Matching. Custom cookie persistence uses default settings.1.5KViews0likes41Commentscookie persistence issue with two BiG-ip
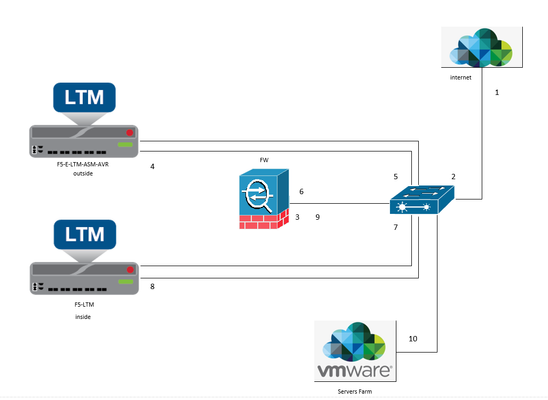
Dear : we have issue withcookie persistence not working if the server connect to inside LTM but if server connect to outside LTM cookie persistence working client traffic From 1 to 10 Outside VS Source Address Translation : Auto Map inside VS withcookie persistence Source Address Translation : Auto Map no Cookie onclient browser forpersistence Br1.2KViews0likes6CommentsHow to maintain Cookie persistence across web application with multiple ports (i.e. 80, 8443)
We have an F5 LB. There are two back-end servers that sit behind it. SSL termination is at the LB. Mapping to the back-end servers is 443 to 80, 80 to 80, and 8443 to 8443. That is, on the back-end servers, we have ports 80 and 8443 open. The LB was first setup with source IP persistence. We just moved to Cookie persistence to alleviate some issues with IP addresses switching mid-session and the like. The cookie persistence is session cookie, meaning no expiry and the cookie should expire when the user closes the browser. The cookie is also encrypted with a passphrase to comply with security practices (not sure why F5 would set the cookie value to some obfuscated value that maps to the back-end server IP and port, since that is apparently not very difficult to un-obfuscate). In testing the web application behind the LB, everything seemed to be OK. Then, we got a report from users with a particular piece in the web application, which loads pages over multiple ports (i.e. 80, 8443). What I see happening is, whether the request first starts with 80 or 8443, the LB cookie value is being generated again when the page is requested from the other port. It doesn't happen 100% but it happens frequently. Then the application reports that the application session is invalid. My guess is even if the cookie value changes, if it happens to hit the same back-end server, there will be no issue. However, if the request happens to hit the other back-end server, the web application will see the request as a new application session and, thus, report that the application session is invalid. What I think what might fix it is maintaining the cookie persistence across the multiple ports we have configured (i.e. 80, 8443). The problem is I'm not quite sure how to do that. That's why I'm here, to ask people who are smarter than me and more experienced and may know some solutions that would work. I would prefer to keep using HTTP Cookie Insert method, although I understand cookie hash does have options similar to source ip persistence such as match across virtual servers and the like. I don't know how much that would help me here, if at all. Can I use an iRule? If so, what might that look like? Maybe an iRule that checks if there is an existing LB cookie and if the request is coming from 80 but going to 8443 or vice-versa, then insert the cookie into said request such that no new cookie is generated and the same cookie is shared across port 80 and port 8443. Sounds good in theory but I'm not even sure of the first place to start to even attempt it. I hope what I'm asking is clear. If it isn't, please feel free to ask me to clarify. I want to maintain the LB cookie across multiple ports. Example: User goes to testsite.com/index.html. LB generates a cookie with value 1234. User is sent to back-end server 1. User then goes to testsite.com:8443/index2.html. LB will generate a new cookie with a different value--let's say it's 5678--and it may send the user to back-end server 1 or 2. If it goes to 1, the web app should be OK. If the request goes to 2, the web app will complain because the web app session is on 1. I want testsite.com and testsite.com:8443 to both have the same exact cookie, which, in this example, would be 1234. Does that make sense? Any help would be appreciated. Thank you in advance.799Views0likes2CommentsPersistence causing problems with redirection iRule?
I have a slightly strange case on website where I am seeing traffic being redirected strangely, and I believe it may be down to my persistence. I was wondering if anyone could advise on if what I am seeing is indeed because of persistence and, if so, how to best avoid it. I have cookie and source address persistence set up on the VS for and a pool of servers which serve this main part of the site and all subsites except one. I have an iRule set up on the VS to redirect any connections to www.website.com/test to a separate pool, which serves only this specific subsite. I am sometimes seeing connections for www.website.com being redirected to the pool designated solely for the 'test' subsite, despite these connections not matching the iRule. Specifically I am able to create this behaviour by navigating to www.website.com/test in a browser and then deleting '/test' and hitting enter. The connection is directed to the pool designed to serve just the '/test' subsite, which is unable to serve the main body of the site. Is this being caused by a persistence record being created for my connection to the '/test' pool, which is then being matched when I later navigate to the main site? If so, is there any way to avoid this?Solved746Views0likes12CommentsLTM and java certs
I have an internal web app I need to load balance. this app is SSL and I would like to use cookie persistence. I have setup my cert on my LTM and setup persistence before for other apps and it works well. issue I have run across with this new app is that even though the apache cert on the app matches our cert on the LTM, there is a portion of this app that uses java with the companies certificate. this results in the ssl decryption\encryption needed for cookie persistence to break on the java portion making the web app not function all together. are there any options in this scenario of java cert being different from the web server cert or am I stuck changing my persistence from cookie to ssl? PS I have an older bigip 1600 with 9.4 running.659Views0likes19Commentscookie encyption passphrase
I realize this is a pretty basic question so don't skewer me. I want to enable cookie encryption which seems like a very painless process, but I'm just curious as to what the cookie encryption passphrase is used for? is this going to be needed to be given out to users? whats the use and when is it utilized? further configuration needed on other devices for it? any and all help is always appreciated.599Views0likes5CommentsViewing Cookie-insert Persistence Records
Is there anywhere on the LTM that I can confirm that cookie-insert is being used for persistence? Currently I have a VS with cookie-insert as primary, and source-address as secondary, but when I look in tmshell all I see are source-address persistence records. When I enable AVR and capture transactions I can see the client sending the cookie in its requests. I suppose my confusion stems from the fact that I have another VS with cookie-hashing enabled, and "show ltm persistence...." will show that hashing is the method in use. This thread here indicates that the BIG-IP doesn't "store" the cookies, but it seems like it should indicate when a client is utilizing cookie-insert.599Views0likes7CommentsJava application persistence issue with load balancer
I have a java application running on 2 web servers, load balanced in round robin fashion and cookie insert persistence on VIP. From what I understand of the application, it keeps doing some kind of pulse check with server every few seconds because of which the java app disconnects as it is getting bounced bw one server and other, meaning persistence is not working for subsequent connections made by the java applet. I cannot use source/dest_addr persistence, so it has to be cookie persistence. I somehow managed to disable the pulse check within application, which made the app stable and no disconnects were noticed. However after a while some of the tabs/pages started to throw errors which I believe is due to server switch at the F5 load balancing. Any ideas what else can be done to ensure the java application connection made to one server is persistent for subsequent connections made from same source?594Views0likes6CommentsOnly Apply Default Persistence Profile (HTTP Cookie Insert) to specific URI paths
Currently, we are using a Default Persistence Profile (HTTP Cookie Insert) on our Virtual Server. However, we only need persistence for a few paths on the site; https://login.website.com/path1/* https://login.website.com/path2/* https://login.website.com/path3/* Is it possible, using an iRule perhaps (?), to only apply a pre-defined persistency profile for specific paths, and not the entire Virtual Server? Key point: I do NOT want to set/define the persistency options inline in the iRule. I would like to essentially reference a defined Persistency Profile ("Website-Cookie-Profile") from within the iRule. Cookie Method: HTTP Cookie Insert Cookie Name: ThisIsMyCookie Always Send Cookie: (not selected) Expiration: Session Cookie (selected) Cookie Encryption Use Policy: preferred Encryption Passphrase**: (masked) Thanks in advance. Any example iRules would be greatly appreciated.512Views0likes2Comments