Apache Tomcat Remote Code Execution via JSP upload (CVE-2017-12615 / CVE-2017-12617)
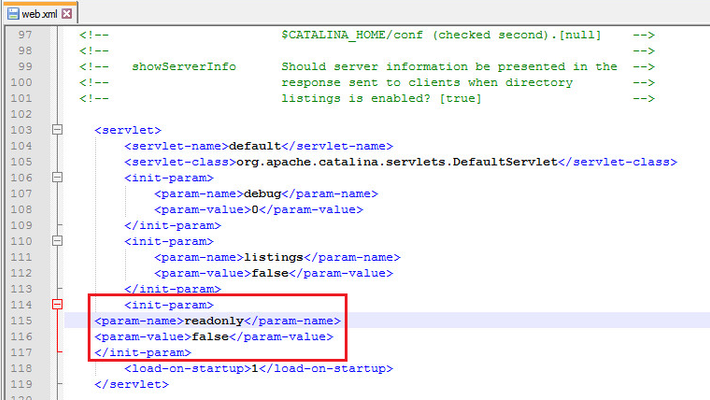
In the recent days, a new vulnerability in Apache Tomcat has been published (CVE-2017-12615). The vulnerability allows attackers to upload arbitrary files to the Tomcat application server by utilizing the HTTP PUT method. By uploading a .JSP file to the Tomcat Application Server, an attacker may be able to execute malicious JAVA code on the remote machine. Reproducing the vulnerability By default, Apache Tomcat restricts the usage of the HTTP PUT method, but by modifying Tomcat’s web.xml configuration file it is possible to disable this restriction. Figure 1: Configuring Apache Tomcat to allow the usage of the PUT method. Once this configuration change is in place, attackers may send HTTP PUT requests to the server, and consequently create files on it. Figure 2: Specially crafted PUT request exploiting the vulnerability sent to a preconfigured Apache Tomcat instance. Figure 3: The uploaded file as can be found in the application root directory. After the file has been successfully uploaded to the server by the attacker, he can access the uploaded file. As the uploaded file is a JSP file containing JAVA code, Apache Tomcat will execute this code while rendering the response. Figure 4: Accessing the uploaded file. Mitigating the vulnerability with BIG-IP ASM BIG-IP ASM customers are already protected against this vulnerability. By default, BIG-IP ASM restricts the usage of the HTTP PUT method and will block any HTTP PUT request sent to the virtual server. The exploitation attempt will also be blocked by a Server Side Code Injection signature (Signature ID 200004048) which can be found in signature sets that include “Server Side Code Injection” attack type. Figure 5: Exploitation attempt blocked with illegal HTTP method. Figure 6:Exploit blocked with Attack Signature (200004048) Update CVE-2017-12617 is the same vulnerability as CVE-2017-12615. Additional Apache Tomcat patch wasreleased as the previous patch did not resolve the remote code execution vulnerability described in CVE-2017-12615. Therefore it is possible to mitigate CVE-2017-12617 using BIG-IP ASM as previously described.7.7KViews0likes1Comment