Mitigation of OWASP API Security Risk: Unsafe Consumption of API using F5 XC Platform
Introduction: The Introductory article covered a brief overview of OWASP Top 10 API Security risk/vulnerability. This article is a continuation of the series and shows mitigating API Vulnerability Unsafe Consumption of API using F5 Distributed Cloud (F5 XC) WAAP. Problem Description: The Digital transformation and modernization of Apps is accelerating to meet the market demands, which results in proliferation of architecture in data center, private/public cloud and across multi cloud which results in organizations to scramble and to gain the competitive edge. As Apps modernization involves API-based systems, those endpoints are now distributed across multiple environments, including third-party services. These third-party APIs are exposing new security risks due to interaction with them. These endpoints are trusted and not verified due to. Developers tend to adopt weaker security standards for authentication/authorization, input validation and sanitization, thereby making these APIs attractive to attackers. Solution from F5 XC: F5 XC delivers a broad approach to API security with a combination of management, monitoring/visibility, and enforcement functionalities. This allows organizations to discover third-party API endpoints, their request/response schemas, sensitive data, authentication state easily and effectively. F5 XC helps in monitoring and securing these API endpoints by performing continuous learning and inspection to provide protection against malicious users. This article aims to demonstrate validation and sanitization of data received from the third-party integrated API before processing further. Preventing unsafe consumption of API vulnerabilities using F5 XC SaaS console configs: Below are the steps that are being followed to access valid API data from the third-party Integrated API, Upload the modified swagger file Configure API Protection for Endpoints Step 1: Uploading the modified swagger file We are updating the swagger file to define API groups and set rules to control access to APIs, enabling granular API access control ability. This ensurestraffic from a third-party API complies with the specified schema. If the traffic does not conform to the API schema of third-party services, you can enable action to block the traffic, ensuring the security and integrity of your API. Note: In this case, Endpoints and expected data associated to it in the Swagger file is validated properly by the developers before uploading in F5 XC console. Login to F5 XC console and click on Multi-cloud App Connect. Select the HTTP Load Balancer by selecting “…” > Manage configuration for your load balancer to which API Protection to be enabled. Select Edit Configuration on the manage configuration screen. Go to API Protection section, From the API definition menu, select Enable to use an API definition. From the API Definition menu, select the API definition. Click “Add Item” to create a new definition. Enter name in metadata section. In Swagger Specs section, click on the drop-down menu and select “Upload Swagger file”. Enter the name in Metadata section of Swagger File. Click on Upload File button in Swagger Upload section to upload the swagger file. A sample swagger file shown below validates the email address returned by the third-party server. Once the file is uploaded, click on Continue. Select the swagger file created above from the Swagger Specs drop-down and click on Continue and page will be redirected to LB configuration page. Step 2: Configuring API Protection for Endpoints From Validation drop-down, select “All Endpoints” to enable validation for all the endpoints specified in the swagger file. In the “All endpoints” validation section, From the OpenAPI Validation Response Processing Mode menu, select validate. From the Response Validation Enforcement Type menu, select the type of enforcement as Block. From the Response Validation Properties menu, select HTTP Headers, Content-type, HTTP Body, and Response Code. Enable Show Advanced Fields button on the top right corner of the section and select Property Validation Settings to Custom and select “Disallow” for Allow/Disallow additional query parameters in Request. Click on Apply. Click on Save and Exit. In this scenario, below is the data sent by the third-party API to store the details in the database server If the third-party service returns data, which includes malicious SQL injection/payload that causes harm to the database servers during the process of transport security, authentication/authorization. In this attack scenario, a third-party API returns data consisting of 'Admin' OR 1=1--' which tries to compromise the system. This is instantly identified, cautioned, and mitigated by F5 XC. Json data logs for respective security analytics. Conclusion: With F5 XC things become easier to manage, monitor andenforce security to API services. F5 XC provides the feasibility of continuous discovery of APIs and inspectingdata received from the third-party services when configured appropriately in the Load Balancer. This helps in secure and manage APIs with the modern App and API deployment with necessary management and protection against threats. Related Links: https://owasp.org/API-Security/editions/2023/en/0xaa-unsafe-consumption-of-apis/ https://docs.cloud.f5.com/docs/how-to/app-security/apiep-discovery-control https://docs.cloud.f5.com/docs/how-to/app-networking/http-load-balancer Introduction to OWASP API Security Top 10 20231.5KViews2likes0CommentsMitigating OWASP API Security Risk: Excessive Data Exposure using F5 XC Platform
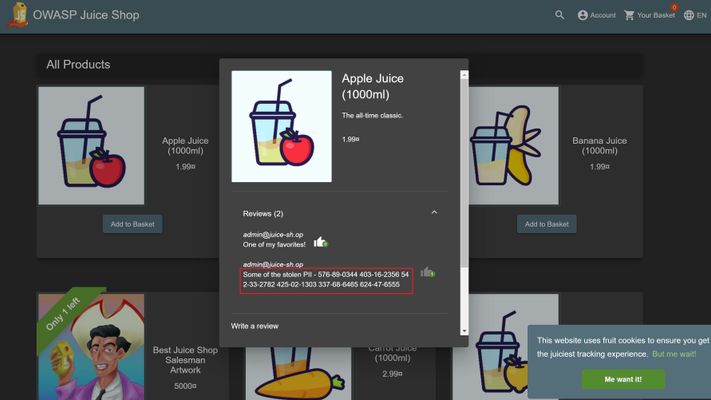
This is part of the OWASP API Security TOP 10 mitigation series, and you can refer here for an overview of these categories and F5 Distributed Cloud Platform (F5 XC) Web Application and API protection (WAAP). Introduction to Excessive Data Exposure: Application Programming Interfaces (APIs) are the foundation stone of modern evolving web applications which are driving the digital world. They are part of all phases in product development life cycle, starting from design, testing to end customer using them in their day-to-day tasks. Since they don’t have restrictions in place, sometimes APIs expose sensitive data such as Personally Identifiable Information (PII), Credit Card Numbers (CCN) and Social Security Numbers (SSN), etc. Because of these issues, they are the most exploited blocks in cybercrime to gain access to customer information which can be sold or further used in other exploits like credential stuffing, etc. Most of the time, the design stage doesn't include this security perspective and relies on 3rd party tools to perform sanitization of the data before displaying the results to customers. Identifying the sensitive information in these huge chunks of API response data is sophisticated and most of the available security tools in the market don't support this capability. So instead of relying on third party tools it’s recommended to follow shift left strategies and add security as part of the development phase. During this phase, developers must review and ensure that the API returns only required details instead of providing unnecessary properties to avoid sensitive data exposure. Excessive data exposure attack scenario: To showcase this category, we are exposing sensitive details like CCN and SSN in one of the product reviews of Juice shop application (refer links for more info) as below - Overview of Data Guard: Data Guard is F5 XC load balancer feature which shields the responses from exposing sensitive information like CCN/SSN by masking these fields with a string of asterisks (*). Depending on the customer's requirement, they can have multiple rules configured to apply or skip processing for certain paths and routes. Preventing excessive data exposure using F5 Distributed Cloud: Step1: Create origin pool – Refer here for more information Step2: Create Web Application Firewall policy (WAF) - Refer here for details Step3: Create https load balancer (LB) with above created pool and WAF policy - Refer here for more information Step4: Upload your application swagger file and add it to above load balancer – Refer here for more details Step5: Configure Data Guard on the load balancer with action and path as below Step6: Validate the sensitive data is masked Open postman/browser, check the product reviews section/API and validate these details are hidden and not exposed as in original application In Distributed Cloud Console expand the security event and check the WAF section to understand the reason why these details are masked as below: Conclusion: CCN and SSN are sensitive information mapping to the identity of a specific individual and protecting this critical data is a necessity in this digital world. In this article we have demonstrated how F5 XC Distributed Cloud Platform can prevent these sensitive data exposures using data guard. For further information check the links below: OWASP API Security - Excessive Data Exposure OWASP API Security – Overview article F5 XC Data Guard Overview OWASP Juice Shop2.2KViews3likes2CommentsMitigation of OWASP API Security Risk: BOPLA using F5 XC Platform
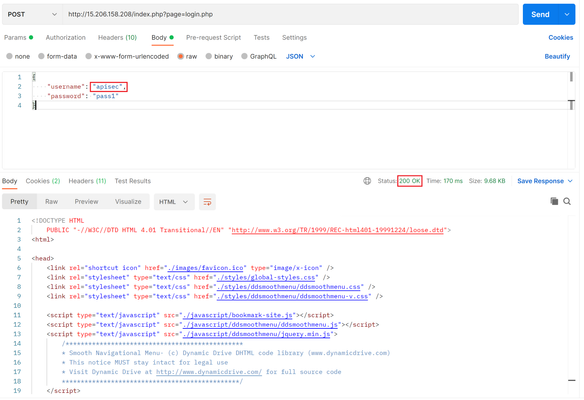
Introduction: OWASP API Security Top 10 - 2019 has two categories “Mass Assignment” and “Excessive Data Exposure” which focus on vulnerabilities that stem from manipulation of, or unauthorized access to an object's properties.For ex: let’s say there is a user information in json format {“UserName”: ”apisec”, “IsAdmin”: “False”, “role”: ”testing”, “Email”: “apisec@f5.com”}. In this object payload, each detail is considered as a property, and so vulnerabilities around modifying/showing these sensitive properties like email/role/IsAdmin will fall under these categories. These risks shed light on the hidden vulnerabilities that might appear when modifying the object properties and highlighted the essence of having a security solution to validate user access to functions/objects while also ensuring access control for specific properties within objects. As per them, role-based access, sanitizing the user input, and schema-based validation play a crucial role in safeguarding your data from unauthorized access and modifications. Since these two risks are similar, the OWASP community felt they could be brought under one radar and were merged as “Broken Object Property Level Authorization” (BOPLA) in the newer version of OWASP API Security Top 10 – 2023. Mass Assignment: Mass Assignment vulnerability occurs when client requests are not restricted to modifying immutable internal object properties. Attackers can take advantage of this vulnerability by manually parsing requests to escalate user privileges, bypass security mechanisms or other approaches to exploit the API Endpoints in an illegal/invalid way. For more details on F5 Distributed Cloud mitigation solution, check this link: Mitigation of OWASP API6: 2019 Mass Assignment vulnerability using F5 XC Excessive Data Exposure: Application Programming Interfaces (APIs) don’t have restrictions in place and sometimes expose sensitive data such as Personally Identifiable Information (PII), Credit Card Numbers (CCN) and Social Security Numbers (SSN), etc. Because of these issues, they are the most exploited blocks to gain access to customer information, and identifying the sensitive information in these huge chunks of API response data is crucial in data safety. For more details on this risk and F5 Distributed Cloud mitigation solution, check this link: Mitigating OWASP API Security Risk: Excessive Data Exposure using F5 XC Conclusion: Wrapping up, this article covers the overview of the newly added category of BOPLA in OWASP Top 10 – 2023 edition. Finally, we have also provided minutiae on each section in this risk andreference articles to dig deeper into F5 Distributed Cloud mitigation solutions. Reference links or to get started: F5 Distributed Cloud Services F5 Distributed Cloud WAAP Introduction to OWASP API Security Top 10 2023346Views3likes0CommentsMitigation of OWASP API Security Risk: Broken Authentication using F5 XC Platform
Introduction to Broken Authentication: Authentication in APIs adds friction, so during the initial development phase and for the sake of simplicity developers try to not implement authentication and authorization processes. As the application keeps growing, they will add these recommendations to existing code and during this transition they may have left some of the old internal APIs without authentication. Hackers will try to find these kinds of poorly authenticated flaws to bypass the login validation and gain access to their application data. According to Okta, most of the data breaches in 2020 fall under this category and so this is one of the most preferred approaches to attackers. Authentication is said to be broken if hackers are able to compromise passwords, keys, session tokens and user account information. As per OWASP, APIs may fall under this category if API doesn’t have authentication validation API permits credential stuffing API permits attackers to perform a brute force attack without presenting captcha/account lockout mechanism Permits weak passwords Sends sensitive authentication details, such as auth tokens and passwords in the URL Strong password policy not implemented Below are some of the preventive measures which are to be followed to protect application from these kinds of exploits: Authentication support for all API’s Authorization design developed in a good and structured way using access controls Session tokens need to be expired in shorter time Rate limiting and account locking after specific invalid logins Rotation of keys and certs Internal APIs should be audited and not exposed to outside Multi factor authentication support for critical APIs Enforcing strong password policy with special chars, capitals, numbers and minimum of 8 characters length In short, if the application doesn’t have authentication mechanism, supports weak passwords or even if we are unable to identify the authentication details of our requests, our application can be prone to broken authentication. And to prevent this risk we need different kinds of solutions to identify authentication details, enforce authentication policies, prevent credential stuffing & bot attacks, continuous monitoring of API’s, etc. So, let’s delve into F5 Distributed Cloud Platform (XC) and check how it can detect and protect applications against these vulnerabilities. Authentication Vulnerabilities Detection: Login to Distributed Cloud console and navigate to your load balancer configuration Enable API Discovery feature on this load balancer Once we have enabled this feature, Web Application and API Protection (WAAP) inbuilt AI/ML engine will start tracking all incoming traffic and after some time we will be able to see API endpoint details as below Change to table view and observe different types ofauthentication details along with some of the vulnerabilities discovered by WAAP as below a. API type and authentication state b. Auth type like JWT and insights on user role c. Security assessment for API endpoint vulnerabilities, threat level and risk score d. Sensitive data leakage like IP, credentials, etc Mitigation Steps: AppSec/SecOps can navigate to the Security & API endpoint dashboards and analyze these requests data & authentication insights. If they are not familiar with any kind of requests, they can explore the solutions below and as per their requirements they can configure them to prevent these vulnerabilities. Configure rate limiting to keep a limit on number of requests - check here for more details on rate limiting Configure API Protection rules on load balancer to restrict access to applications – check here for more details on API rules Configure Bot Defense to prevent credential stuffing and bot attacks – check here for more details on bot protection Configure OpenAPI schema validation to detect/block invalid and abnormal requests – for more details check this article Malicious user detection – check this existing article for more details ConfigureMutual Transport Layer Security (mTLS) authentication using client certificates - check here for more information Conclusion: Wrapping up, this article covered an overview of broken authentication risk and then we also shed light on how WAAP can extract valuable authentication vulnerabilities. Lastly, we also discussed some of the XC mitigation steps to prevent this API Security risk. For more information or to get started check links below: OWASP API Security Top 10 2019 OWASP API Security Top 10 2023 F5 Distributed Cloud WAAP2.8KViews4likes0CommentsMitigating OWASP API Security Top 10 risks using F5 NGINX App Protect
This 2019 API Security article covers the summary of OWASP API Security Top 10 – 2019 categories and newly published 2023 API security article covered introductory part of newest edition of OWASP API Security Top 10 risks – 2023. We will deep-dive into some of those common risks and how we can protect our applications against these vulnerabilities using F5 NGINX App Protect. Excessive Data Exposure Problem Statement: As shown below in one of the demo application API’s, Personal Identifiable Information (PII) data, like Credit Card Numbers (CCN) and U.S. Social Security Numbers (SSN), are visible in responses that are highly sensitive. So, we must hide these details to prevent personal data exploits. Solution: To prevent this vulnerability, we will use the DataGuard feature in NGINX App Protect, which validates all response data for sensitive details and will either mask the data or block those requests, as per the configured settings. First, we will configure DataGuard to mask the PII data as shown below and will apply this configuration. Next, if we resend the same request, we can see that the CCN/SSN numbers are masked, thereby preventing data breaches. If needed, we can update configurations to block this vulnerability after which all incoming requests for this endpoint will be blocked. If you open the security log and filter with this support ID, we can see that the request is either blocked or PII data is masked, as per the DataGuard configuration applied in the above section. Injection Problem Statement: Customer login pages without secure coding practices may have flaws. Intruders could use those flaws to exploit credential validation using different types of injections, like SQLi, command injections, etc. In our demo application, we have found an exploit which allows us to bypass credential validation using SQL injection (by using username as “' OR true --” and any password), thereby getting administrative access, as below: Solution: NGINX App Protect has a database of signatures that match this type of SQLi attacks. By configuring the WAF policy in blocking mode, NGINX App Protect can identify and block this attack, as shown below. If you check in the security log with this support ID, we can see that request is blocked because of SQL injection risk, as below. Insufficient Logging & Monitoring Problem Statement: Appropriate logging and monitoring solutions play a pivotal role in identifying attacks and also in finding the root cause for any security issues. Without these solutions, applications are fully exposed to attackers and SecOps is completely blind to identifying details of users and resources being accessed. Solution: NGINX provides different options to track logging details of applications for end-to-end visibility of every request both from a security and performance perspective. Users can change configurations as per their requirements and can also configure different logging mechanisms with different levels. Check the links below for more details on logging: https://www.nginx.com/blog/logging-upstream-nginx-traffic-cdn77/ https://www.nginx.com/blog/modsecurity-logging-and-debugging/ https://www.nginx.com/blog/using-nginx-logging-for-application-performance-monitoring/ https://docs.nginx.com/nginx/admin-guide/monitoring/logging/ https://docs.nginx.com/nginx-app-protect-waf/logging-overview/logs-overview/ Unrestricted Access to Sensitive Business Flows Problem Statement: By using the power of automation tools, attackers can now break through tough levels of protection. The inefficiency of APIs to detect automated bot tools not only causes business loss, but it can also adversely impact the services for genuine users of an application. Solution: NGINX App Protect has the best-in-class bot detection technology and can detect and label automation tools in different categories, like trusted, untrusted, and unknown. Depending on the appropriate configurations applied in the policy, requests generated from these tools are either blocked or alerted. Below is an example that shows how requests generated from the Postman automation tool are getting blocked. By filtering the security log with this support-id, we can see that the request is blocked because of an untrusted bot. Lack of Resources & Rate Limiting Problem Statement: APIs do not have any restrictions on the size or number of resources that can be requested by the end user. Above mentioned scenarios sometimes lead to poor API server performance, Denial of Service (DoS), and brute force attacks. Solution: NGINX App Protect provides different ways to rate limit the requests as per user requirements. A simple rate limiting use case configuration is able to block requests after reaching the limit, which is demonstrated below. Conclusion: In short, this article covered some common API vulnerabilities and shows how NGINX App Protect can be used as a mitigation solution to prevent these OWASP API security risks. Related resources for more information or to get started: F5 NGINX App Protect OWASP API Security Top 10 2019 OWASP API Security Top 10 20232.2KViews7likes0CommentsMitigating OWASP API Security Risk: Mass Assignment using F5 XC Platform
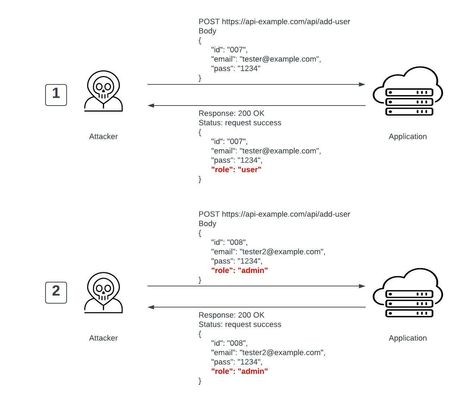
Overview: This article is a continuation of the series of articles on OWASP API Security vulnerabilities and demonstrates a scenario for mitigating API Mass Assignment using F5 Distributed Cloud Platform (XC). Introduction to OWASPAPI Mass Assignment: APIs are the foundation building blocks for today’s modern applications and because of such high acceptance there are software frameworks available to help the developers with the implementation, but these frameworks sometimes allow developers to automatically bind client’s request parameters into the code variables, opening gates for the attackers to exploit the Mass Assignment vulnerability. API Mass Assignment vulnerability occurs when manually crafted requests from clients to modify immutable internal object properties are not restricted by API Endpoints. Attackers can take advantage of this vulnerability by framing an HTTP request to escalate user privilege, bypass security mechanisms or use any other approach to make the API Endpoints work in a way it was not designed to work. Note: Mass Assignment and Excessive Data Exposure which were a separate risk category in OWASP API Sec 2019 are now merged into a new risk category named Broken Object Property Level Authorization The above image is the pictorial representation of possible exploitation of Mass Assignment vulnerability. You can see the attacker is successfully able to escalate his privilege from normal user to admin by manipulating the JSON content of the API request. In the first step, the attacker sends a valid API request to add the user and gets a response back with a parameter carrying information about the role. In the second step, the attacker adds the role parameter to the JSON object in the API request eventually resulting in successful exploitation of the vulnerability. Prevention Steps: Automatic binding ofclient’s input data into application's internal code variables should be avoided. Allow/Deny list should be clearly defined for the properties that should or shouldn't be accessible by the clients. Application schema should be well defined and enforced on all incoming client requests. Demonstration: For this demonstration we’ve already hosted crAPI (completely ridiculous API) application by referring to the QuickStart guide in the repository. Also, in the XC console we added the hosted application as an origin server and attached it with the newly created HTTP Load Balancer (LB). Note: crAPI is a vulnerable application designed for training purposes and can be a helpful tool to understand the OWASP top 10 most critical API security risks. For more details you can refer to OWASP crAPI repository Attack Scenario: In the use case below we have an API endpoint which is used to order products. This endpoint has a vulnerable field named “quantity” that can be exploited for mass assignment by providing a negative value resulting in a successful purchase order with an increase in available balance. As shown below at the start of the demo, the available balance for a user account is 200 $. Step1: First step is to gather the endpoint and request payload data by placing a valid purchase order from GUI. In the above screenshot, you can see we have successfully placed the order from the GUI which resulted in a decrease of available balance by 10$. This is a valid customer use case scenario. Step2: Next, we will try to place an order for a product with negative quantity using the gathered endpoint and check if mass assignment vulnerability is present or not. As you can see in the above screenshot the order with the negative quantity is placed successfully and the available balance is increased by 10$ which is not expected. Hence, we can conclude that mass assignment vulnerability exists in this demo application. Prevention through F5 XC: As mentioned in the prevention steps for the purpose of schema validation we will upload OpenAPI specification file to XC and set up the validation rules on incoming client requests If a mismatch occurs, an API Security event will betriggered and based on the enforcement mode set in the validation rules, the request will either getreported or blocked. Step1: As shown in the below image, update the crAPI’s OpenAPI specification file (a.k.a. swagger file) by adding a “minimum” keyword with value as “1” for the “quantity” parameter to restrict the request carrying a negative quantity to bypass Step2: Import crAPI’s swagger file to the LB and create API Definitions Login to F5 XC console Navigate to your LB and start editing the applied configuration Scroll down to API Protection and select “Enable” in API Definition field Click “Add Item”, Enter a name Click “Upload Swagger file”, Enter a name and upload the swagger file for your application, Apply the changes Now from your LB main config page, select “Custom List” for “Validation” field and click Configure. Start configuring Validation List, click “Add Item”, Enter a name, select “Validate” for “OpenAPI Validation Request Processing Mode” field, select “Block” for field “Request Validation Enforcement Type” and select all available properties in “Request Validation Properties” field, below of the config page select “Base Path - /” for “Type” field, Apply the changes. Refer to the document for more details. Step3: Try to repeat the attack scenario of ordering a product with negative quantity. As you can see in the above screenshot the attack was blocked successfully by the XC. Step4: Monitor the “Security Analytics” logs from F5 XC console Conclusion: API Mass assignment vulnerability can illegally be exploited by attackers to cause some serious damage but as demonstrated, F5 XC API security solutions can help to detect and mitigate such vulnerabilities with the help of Open-API schema validation feature. For more details, follow below links: OWASP API Security Project OWASP API6:2019 Mass Assignment F5 Distributed Cloud Services F5 Distributed Cloud WAAP Overview of OWASP API Security Top 10 2019 Introduction to OWASP API Security Top 10 20234.2KViews7likes2CommentsMitigating OWASP API Security risks using BIG-IP
The introduction article covered the summary of OWASP API Security TOP 10 categories. As part of this article, we will focus on how we can protect our applications against some of these vulnerabilities using F5 BIG-IP Advanced Web Application Firewall (AdvancedWAF). Excessive Data Exposure: Problem Statement: As shown below in one of the demo application API’s, Personally Identifiable Information (PII) data like Credit Card Numbers (CCN) and Social Security Numbers (SSN) are available which are highly sensitive and so we must hide these details to prevent personal data exploits. Solution: By configuring DataGuard related WAF settings in BIG-IP as below, we are able to mask these numbers thereby preventing data breaches. If needed, we can update settings to block this vulnerability after which all incoming requests for this endpoint will be blocked. Injection: Problem Statement: Customer login pages without secure coding practices may have flaws and intruders will use them to exploit credential validation using different types of injections like SQLi, Command Injections, etc. In our demo application, attackers were able to bypass validation using SQLi (Username as “' OR true --” and any password) thereby getting administrative access as below: Solution: By configuring AdvancedWAF settings in BIG-IP and by enabling appropriate violation blocking settings, we are able to identify and block these types of known injection attacks as below. Improper Assets Management: Problem Statement: In our demo application, attackers have identified deprecated endpoints with a path starting with “/v1” which are currently not being maintained but are still available. Using these undocumented endpoints, attackers can get access to unwanted data causing loss of sensitive app information. Solution: To avoid this specific use case, we have come up with OpenAPIor Swagger files for the demo application, uploaded them to BIG-IP and have configured AdvancedWAF to allow only these known URL’s. If attackers try to access deprecated URL’s which are not available in OpenAPIfiles, the requests will be blocked. Insufficient Logging & Monitoring: Problem Statement: Appropriate logging and monitoring solutions play a pivotal role in identifying attacks and also in finding the root cause for any security issues. Without these solutions, applications are fully exposed to attackers and are completely blind in identifying details of users and resources being accessed. Solution: BIG-IPprovides many dashboards like Statistics, Dos Visibility, Analytics, OWASP, etc for end-to-end visibility of every request being accessed and users have the ability to filter requests as per their requirements. By default, system provides different types of logging profiles and users can also create custom logging profiles. They can attach them to Load Balancers to track these data flows. BIG-IP also supports a reporting service to generate the timely reports as needed by users. Conclusion: As demonstrated above, F5 BIG-IP AdvancedWAF can be used as a mitigation solution to prevent different OWASP security attacks againstour modern applications running API’s. Stay tuned for more OWASP videos. For getting started, check below links: BIG-IP AdvancedWAF OWASP API Security Top 10 BIG-IP VE Overview of BIG-IP2KViews4likes3CommentsIntroduction to OWASP Top 10 API Security Risks - 2019 and F5 Distributed Cloud WAAP
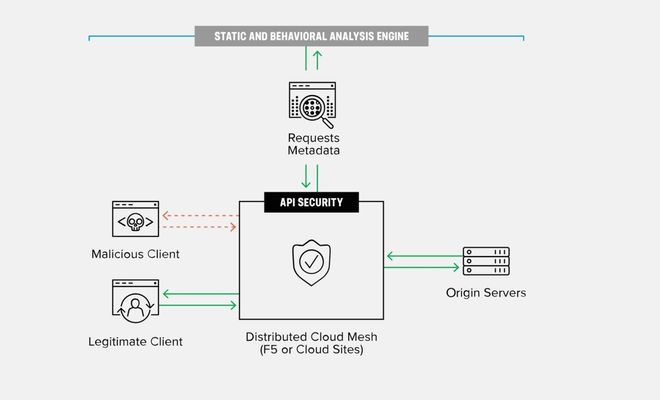
Introduction to API: An application programming interface (API) is a combination of protocols, functions, etc. which we can utilize to get details about resources, services and features.APIs are fast, lightweight and reliablebut they expose sensitive data and so they have become the targets of hackers. Overview of OWASP API Security: The simplicity of APIs has given hackers a chance to infiltrate them in plethora of ways tosteal personal and sensitive details. Increase in demand of API security caused a need for a project to keep track of latest API vulnerabilities andsecurity procedures calledOWASP API Security Top 10. As per the above project below are the top ten issues and their overview in API security as of 2019. API1:2019 Broken Object Level Authorization APIs expose endpoints that manage objects using unique identifiers, providing hackers a chanceto bypass access controls. To prevent this attacks authorized checks like credentials and APItokenshould always be kept in place in the code ifthere is a request using a user input. API2:2019 Broken User Authentication Authentication mechanisms are sometimes implemented with less security, allowing attackers to compromise authentication tokensto take over other user's identities. API3:2019 Excessive Data Exposure In most of the recent attacks it was observed developers are exposing unnecessary and sensitive object properties providing illegal users a way to exploit them.For more information about this vulnerability, demonstration scenario and prevention steps using F5 XC refer to thearticle. API4:2019 Lack of Resources & Rate Limiting APIs do not have any restrictions on the size or number of resources that can be requested by the end user. Above mentioned scenarios sometimes lead to poor API server performance, Denial of Service (DoS) and brute force attacks.For more information about this vulnerability, demonstration scenario and prevention steps using F5 XC refer to thearticle. API5:2019 Broken Function Level Authorization Most applications are composed of different groups, users and roles. If configurations like access control are not applied, it will lead to authorization flaws allowing one user to access theresources of other users. API6:2019 Mass Assignment Code sanity should always be performed in response data, binding client data into code variables without filtering gives hackers a chance to guess object's properties by exploring the API endpoints, documentations, etc. API7:2019 Security Misconfiguration This attack is mostly caused because of misconfigured HTTP headers, unnecessary HTTP methods, permissive Cross-Origin resource sharing (CORS), and verbose error messages in logs containing sensitive information like usernames, PIN, IP addresses, etc.For more information about this vulnerability, demonstration scenario and prevention steps using F5 XC refer to thearticle. API8:2019 Injection OS commands, SQL, Command Injection, etc., occur if there are no restrictions on user requested schema as part of filter query. The malicious request can sometimes bypass these validations to execute unintended commands providing attackers access to sensitive information.For more information about this vulnerability, demonstration scenario and prevention steps using F5 XC refer to thearticle. API9:2019 Improper Assets Management A modern web application typically hosts thousands of requests. It is critical to update the documentation/swagger as per the latest changes and include information about newly implemented APIs. If they are not regularly updated hackers can explore and find any deprecated API which may sometimes expose debug endpoints.For more information about this vulnerability, demonstration scenario and prevention steps using F5 XC refer to thearticle. API10:2019 Insufficient Logging & Monitoring Any issues in logging and monitoring services will give attackers more ways to attack systems without being recognized. It’s always advised to configure the best monitoring solutions to keep track of all logs and to configure email alerts. Sometimes it’s the best practice to keep logging details in a different location to avoid malicious user activity erasing their log trails.For more information refer to the article. Overview of F5 Distributed Cloud WAAP: Web Application and API protection (WAAP) is a SAAS offering provided by F5 Distributed Cloud Services to protect applications and published APIs using Web Application Firewall (WAF), bot protection, API security, and DDoS mitigation. Once WAAP policy is applied on the load balancer, these service engines protect web applications and API endpoints with the latest automatic detection of WAF, Bot and DOS attack signatures. One of the key sections of Distributed Cloud WAAP is API security which focuses primarily on securing the API’s using different configurations like OpenAPI ingestion, automatic API discovery, service policies, rate limiting, Allow/Denied URLs, etc. Below diagram shows how Distributed Cloud WAAP protects APIs: Whenever there is a request originating from end users Distributed Cloud WAAP analyses the request metadata details like URL, filter parameters, Headers, etc. to find whether it’s a legitimate request. Once the request is screened, validated and approved then only the request is forwarded to the back-end servers. Back-end servers then return the requested details to the end user. If for any reason Distributed Cloud WAAP finds the request has discrepancies or is not valid the request will be blocked, and a security event will be generated in dashboard. Users or administrators can analyze the captured request details and can modify the existing Distributed Cloud WAAP configurations if needed to reach the business goals. Articles on OWASP API Security: Excessive Data Exposure Lack of Resources & Rate Limiting Security Misconfiguration Injection Improper Assets Management Insufficient Logging & Monitoring Note: Articles on remaining OWASP API Security Top 10 2019 vulnerabilities are in pipeline and will get published shortly, stay tuned for the update New edition of OWASP API Security Top 10 risks - 2023 is released and you can check this link for more details Related Links: F5 Distributed Cloud WAAP F5 Distributed Cloud Services6.3KViews3likes0CommentsMitigating OWASP API Security Risk: Security Misconfiguration using F5 XC Platform
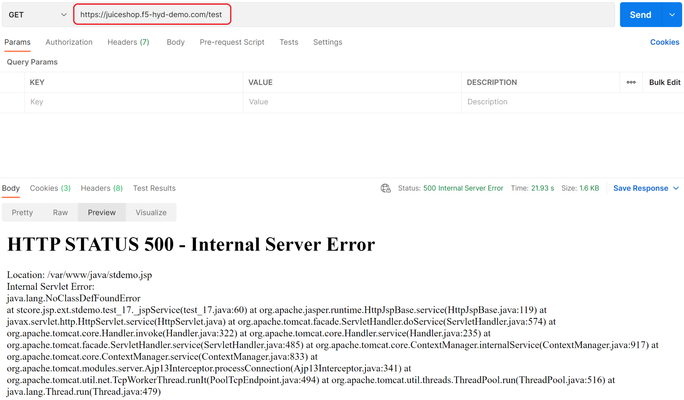
Overview: This article is a continuation of the series of articles on OWASP API Security vulnerabilities and demonstrates a scenario for mitigating API Security Misconfiguration using F5 Distributed Cloud Platform. Introduction to OWASP API Security Misconfiguration: APIs are the backbone of the modern application development model and because of their heavy usage they often become victim of attacks. Sometimes these vulnerabilities arise if security best practices are missed and are not followed properly in application development life cycle. Below are a few scenarios which fall under API Security Misconfiguration category: Latest security patches are not applied. Unnecessary HTTP verbs are enabled exposing APIs to get accessed by them. Improper implementation of CORS policy. Missing repeatable security hardening process. Exposing detailed stack trace error messages or sensitive information. Problem Statement: There are many ways an attacker can take advantage of security misconfigurations by utilizing readily available automation tools. In the demonstration below we will cover a scenario where the application is vulnerable for exposing stack trace information and will see how F5 Distributed Cloud WAAP can help in identifying and mitigating such threats. What is Stack Trace? Stack Trace is a system defined error message which occurs when program under execution gets abnormally terminated. This information is normally used for debugging purposes. Application throwing stack trace information gives the attacker a picture of active subroutines at that point during its execution and may help him to find flaws in the system which eventually may lead to some harmful implications. For the demonstration, we have already deployed a Load Balancer (LB) in the Distributed Cloud Console and attached the origin server to the LB. For configuration steps please follow the documentation As you can see from the above screenshot, a specific API Endpoint in our application is throwing Internal server error message along with stack trace information. F5 Distributed Cloud WAF engine can help in detecting such threats. For that you need to create a WAF policy with default configuration, enable WAF and attach theWAF policy to the LB. Configuration steps are covered in the documentation In the above screenshot you can see that Distributed Cloud WAF engine has successfully identified security misconfiguration in the API Endpoint. Prevention: From the suite of security solutions offered by F5 Distributed Cloud WAAP, here we have chosen to create an ‘API Protection Rule’ to restrict the access of API Endpoint throwing stack trace information. Step1: Select Load Balancer service tile from Distributed Cloud console homepage. Step2: On the right side of your LB click on three dots (ellipsis) and select ‘Manage Configuration’ as an action, click on ‘Edit Configuration’. Step3: Scroll down, in ‘API Protection’, click ‘Configure’ API Protection Rules. Step4: In ‘API Endpoints’, click ‘Add item’, Enter a name and configure a rule to deny access to the API Endpoint ‘/test’, Click ‘Apply’ then ‘Save and Exit’. Step5: Re-visit the same API Endpoint, throwing stack trace information. In the above screenshot you can see access to the vulnerable API Endpoint is restricted successfully. Conclusion: As demonstrated, the F5 Distributed Cloud WAF engine can successfully detect security misconfiguration event and optionally applying API Protection Rule on top of it can add a layer of security, safeguarding application against potential threats. For further information click the links below: OWASP API Security Project OWASP API7:2019 Security Misconfiguration F5 Distributed Cloud Services F5 Distributed Cloud WAAP F5 Distributed Cloud WAF Overview of OWASP API Security Top 10 20193KViews0likes0CommentsMitigating OWASP API Security Risk: Injection flaws using F5 XC Platform
Overview of OWASP and F5 Distributed Cloud Web Application and API Protection: The Introductoryarticle covered basics of OWASP and API Security. We have also seen summary of the top 10 vulnerabilties and an overview of F5 Distributed Cloud (F5 XC) Web Application and API Protection (WAAP). This article is in continuation of the series and shows a scenario of how we can mitigate Injection attack using F5 XC. Introduction to Injection: An injection attack is facilitated by a vulnerability which allows a hacker to provide some malicious code to the application in an unexpected way. When an application passes information from user input, as a best practice there should be some validations in place before sending request to the back-end servers. Sometimes an attacker can induce special characters (like $ to get env variable) and malicious code to bypass the scope and get sensitive details. Some of these attacks include: Executing Linux system calls on back-end servers to get sensitive information Allowing an attacker to steal other user tokens, session cookies, etc. Running malicious scripts like Cross Site Scripting Introduction to F5 Distributed Cloud Web Application Firewall: Most of these exploits can be blocked using F5 Distributed Cloud Web Application Firewall (F5 XC WAF) which supports a vast variety of these types of signatures categorized as LOW, MEDIUM and HIGH. F5 XC WAF can be configured with simple default configuration and can be tuned to custom attack signatures at lowest level. If needed, customers can also explore security events, research attack signatures to identify if the request is valid or illegal and whether it should be blocked or allowed. After analyzing these security events, administrators/SecOps can go ahead and further tune existing WAF configuration as per their business needs. Problem statement: Below demo shows a simple application login API using Postman tool and how we can prevent injection attacks on this API using F5 XC WAF. First let’s analyze the login API of a demo application. As part of the request, the payload takes 2 parameters and users provide a valid username and password to authenticate the login successfully. Valid Postman Request: Illegal Postman Request using SQL Injection: If the application code is not sanitized and validated, then attackers can explore the SQL query used in the request and can add malicious SQL commands (For ex: inject OR 1=1 in the query which is always true and returns data) thereby bypassing the credential validation and can login to application as below. Prevention: We can protect our web applications by creating load balancer and applying F5 XC WAF as below: Login to F5 Distributed Cloud Console with your credentials Navigate to Load balancers menu, then expand “Security” section and then click on “App Firewall” Create App Firewall with mode as Blocking (refer links for more details) Navigate to Manage section and from drop-down select “HTTP Load Balancers” Create load balancer and apply above created App Firewall (refer links for more details) Open Postman and try to regenerate SQL injection attack with same code provided above Validate your request is blocked as below: In Distributed Cloud Console navigate to security events section, expand the latest requests and filter logs with your request-ID. As shown below we can see request is blocked because of SQL Injection vulnerability: Conclusion: As demonstrated above, F5 Distributed Cloud WAAPcan be used to detect, alert and mitigate Injection vulnerabilities. Related Links: F5 Distributed Cloud Platform F5 Distributed Cloud Security WAAP Creating Load balancer Steps Security WAAP features of load balancer3.9KViews3likes0Comments