F5 SSL Orchestrator and Cisco WSA Solution for SSL Visibility and Management
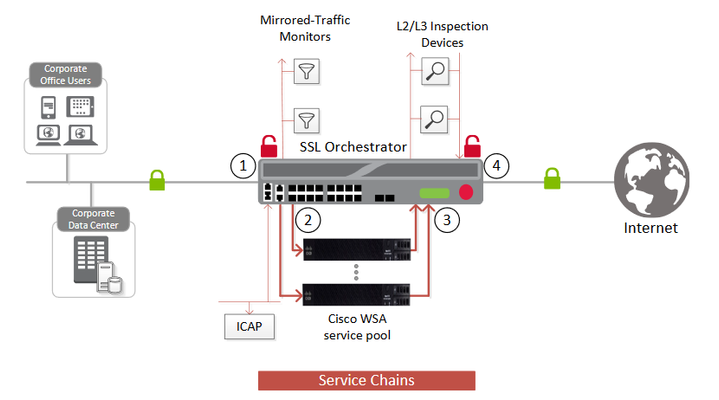
Data transiting between clients (e.g., PCs, tablets, phones, etc.) and servers are predominantly encrypted with Secure Socket Layer (SSL) or the newer Transport Layer Security (TLS) (For reference, see the 2019 TLS Telemetry Report Summary from F5 Labs) Pervasive encryption results in threats being hidden and invisible to security inspection unless traffic is decrypted. The decryption and encryption of data by different devices that are performing security functions, such as Cisco Web Security Appliance (WSA), potentially increases overhead and latency. Added to the visibility difficulties and the fragmented nature of the security stack, enterprises are finding it challenging to design a comprehensive and lasting security strategy. F5® SSL Orchestrator™ and Cisco WSA integrate to deliver centralized visibility, orchestration, security, and control of web traffic, optimizing protection from web-based threats against any device. Bill of Materials F5 SSL Orchestrator Optional functional add-ons include URL filtering subscription, IP Intelligence subscription, network hardware security module (HSM), and F5 Access Manager (APM). Cisco Web Security Appliance Pre-requisites F5 SSL Orchestrator is licensed and set up with internal and external VLANs and self-IP addresses. An SSL certificate—preferably a subordinate certificate authority (CA)—and private key are imported into SSL Orchestrator. The CA certificate chain with the root certificate is imported into the client browser. SSL orchestration generally presents a new paradigm in the typical network architecture. Integrated with SSL Orchestrator, the traffic to the Cisco WSA is decrypted – including usernames, passwords, social security, and credit card numbers, etc. It is therefore highly recommended that security services be isolated within a private, protected enclave defined by the SSL Orchestrator. Solution Deployment In this example deployment setup, the SSL Orchestrator is configured to send decrypted traffic to an inline Cisco WSA. SSL Orchestrator handles both decryption and re-encryption of HTTPS traffic, with an inspection zone installed between the ingress and egress. Decrypted traffic is steered to a service pool of Cisco WSA devices. You can also deploy the F5 system as a device sync/failover device group (including an HA pair) with a floating IP address for high availability. How traffic flows in this deployment: Client traffic arrives at the ingress side of the SSL Orchestrator, where it is classified, and interesting HTTPS traffic is decrypted as part of the SSL handling process. SSL Orchestrator steers the decrypted traffic through the load balanced Cisco WSA service pool as part of a service chain that potentially includes multiple types of security services. The HTTP traffic is inspected by the Cisco WSA services for any hidden threats before sending that traffic back to the SSL Orchestrator. The SSL Orchestrator orchestrates the decrypted traffic through other services in the chain before it aggregates and re-encrypts the traffic, which is then routed to the next destination. Configure the Web Proxy Service Please refer to the appropriate Cisco WSA documentation for more detailed information on configuring WSA. The following are the minimal settings required for integration with SSL Orchestrator. Configuration of the web proxy will be performed from the WSA UI. The Cisco WSA can be configured as either a transparent or explicit web proxy. Deploy SSL Orchestrator using Guided Configuration The SSL Orchestrator guided configuration presents a completely new and streamlined user experience. This workflow-based architecture provides guided configuration steps tailored to a selected topology. Step 1: Topology Properties SSL Orchestrator creates discreet configurations based on the selected topology. Select L3 Outbound (transparent proxy) or L3 Explicit Proxy to support decrypted forward proxy traffic flows through the Cisco WSA. Step 2: SSL Configuration Select the previously imported subordinate CA certificate (see Prerequisites, above) for signing and issuing certificates to the end-host for client-requested HTTPS websites that are intercepted by SSL Orchestrator. Step 3: Create the Cisco WSA Service The services list section defines the security services that interact with SSL Orchestrator. The guided configuration includes a services catalog that contains common product integrations. In the service catalog, double click the 'Cisco WSA HTTP Proxy' service and configure the service settings: Cisco WSA IP address, port, and connected VLANs. Create these routes to route from the Cisco WSA appliance back to SSL Orchestrator. A gateway route to SSL Orchestrator 'from-service' self-IP ( 198.19.96.245 in the above example). A static return route to define the path back to the SSL Orchestrator 'to-service' self-IP (198.19.96.7 in the above example) on the inbound side of the Cisco WSA. Using the SSL Orchestrator service catalog, create additional security services as required before proceeding to the next step. Step 4: Service Chains Create a service chain, which is an ordered list of security devices. The service chain determines which services receive decrypted traffic. Step 5: Security Policy SSL Orchestrator’s guided configuration presents an intuitive rule-based, drag-and-drop user interface for the definition of security policies. In the background, SSL Orchestrator maintains these security policies as visual per-request policies. If traffic processing is required that exceeds the capabilities of the rule-based user interface; the underlying per-request policy can be managed directly. Use this section to create custom rules as required. Step 6: Intercept Rule Interception rules are based on the selected topology and define the listeners (analogous to BIG-IP Local Traffic Manager virtual servers) that accept and process different types of traffic, such as TCP, UDP, or other. The resulting listeners will bind the SSL settings, VLANs, IPs, and security policies created in the topology workflow. Step 7: Egress Settings The egress settings section defines topology-specific egress characteristics like NAT and outbound route. Step 8: Summary Review the setting and click deploy SSL Orchestrator. Testing the Solution Use one of the following ways to observe the decrypted traffic Server certificate test To test an explicit forward proxy topology, configure a client’s browser proxy settings to point this listening IP and port. Ensure that the client trusts the local issuing CA certificate. Open a browser from the client and attempt to access an external HTTPS resource. Once the page is loaded, observe the server certificate of that site and take note of the certificate issuer, which should be the local issuing CA. If you have access to the client’s command-line shell and the cURL or wget utilities, you can simulate browser access using one of the following commands: curl -vk --proxy [proxy IP:port] https://www.example.com wget --no-check-certificate -e use_proxy=yes -e https_proxy=[proxy IP:port] -dO – https://www.example.com Both of these commands will display both the HTML server response and the issuer of the server’s certificate. Decrypted traffic analysis on the SSL Orchestrator Perform a tcpdump on the SSL Orchestrator to observe the decrypted clear text traffic. This confirms the SSL interception by the F5 system. tcpdump –lnni [interface or VLAN name] -Xs0 The security service VLANs and their corresponding application services are all visible from the SSL Orchestrator GUI: Network -> VLANs. Decrypted traffic analysis on the Cisco WSA From the web UI, navigate to Help and Support > Packet Capture. Edit the packet capture settings, such as the network interface on which the packet capture runs. Use one of the predefined filters, or create a custom filter and Click Start Capture to begin. Click Stop Capture to end the capture. Download the packet capture and analyze the tcpdump to observe the decrypted clear text traffic. Additional Resources Learn more about SSL Orchestrator on f5.com Recommended best practices guide: SSL Orchestrator and Cisco WSA Solution581Views0likes0Comments