Get Started with BIG-IP and BIG-IQ Virtual Edition (VE) Trial
Welcome to the BIG-IP and BIG-IQ trials page! This will be your jumping off point for setting up a trial version of BIG-IP VE or BIG-IQ VE in your environment. As you can see below, everything you’ll need is included and organized by operating environment — namely by public/private cloud or virtualization platform. To get started with your trial, use the following software and documentation which can be found in the links below. Upon requesting a trial, you should have received an email containing your license keys. Please bear in mind that it can take up to 30 minutes to receive your licenses. Don't have a trial license?Get one here. Or if you're ready to buy, contact us. Looking for other Resourceslike tools, compatibility matrix... BIG-IP VE and BIG-IQ VE When you sign up for the BIG-IP and BIG-IQ VE trial, you receive a set of license keys. Each key will correspond to a component listed below: BIG-IQ Centralized Management (CM) — Manages the lifecycle of BIG-IP instances including analytics, licenses, configurations, and auto-scaling policies BIG-IQ Data Collection Device (DCD) — Aggregates logs and analytics of traffic and BIG-IP instances to be used by BIG-IQ BIG-IP Local Traffic Manager (LTM), Access (APM), Advanced WAF (ASM), Network Firewall (AFM), DNS — Keep your apps up and running with BIG-IP application delivery controllers. BIG-IP Local Traffic Manager (LTM) and BIG-IP DNS handle your application traffic and secure your infrastructure. You’ll get built-in security, traffic management, and performance application services, whether your applications live in a private data center or in the cloud. Select the hypervisor or environment where you want to run VE: AWS CFT for single NIC deployment CFT for three NIC deployment BIG-IP VE images in the AWS Marketplace BIG-IQ VE images in the AWS Marketplace BIG-IP AWS documentation BIG-IP video: Single NIC deploy in AWS BIG-IQ AWS documentation Setting up and Configuring a BIG-IQ Centralized Management Solution BIG-IQ Centralized Management Trial Quick Start Azure Azure Resource Manager (ARM) template for single NIC deployment Azure ARM template for threeNIC deployment BIG-IP VE images in the Azure Marketplace BIG-IQ VE images in the Azure Marketplace BIG-IQ Centralized Management Trial Quick Start BIG-IP VE Azure documentation Video: BIG-IP VE Single NIC deploy in Azure BIG-IQ VE Azure documentation Setting up and Configuring a BIG-IQ Centralized Management Solution VMware/KVM/Openstack Download BIG-IP VE image Download BIG-IQ VE image BIG-IP VE Setup BIG-IQ VE Setup Setting up and Configuring a BIG-IQ Centralized Management Solution Google Cloud Google Deployment Manager template for single NIC deployment Google Deployment Manager template for threeNIC deployment BIG-IP VE images in Google Cloud Google Cloud Platform documentation Video:Single NIC deploy inGoogle Other Resources AskF5 Github community(f5devcentral,f5networks) Tools toautomate your deployment BIG-IQ Onboarding Tool F5 Declarative Onboarding F5 Application Services 3 Extension Other Tools: F5 SDK (Python) F5 Application Services Templates (FAST) F5 Cloud Failover F5 Telemetry Streaming Find out which hypervisor versions are supported with each release of VE. BIG-IP Compatibility Matrix BIG-IQ Compatibility Matrix Do you haveany comments orquestions? Ask here62KViews8likes24CommentsWhat is BIG-IQ?
tl;dr - BIG-IQ centralizes management, licensing, monitoring, and analytics for your dispersed BIG-IP infrastructure. If you have more than a few F5 BIG-IP's within your organization, managing devices as separate entities will become an administrative bottleneck and slow application deployments. Deploying cloud applications, you're potentially managing thousands of systems and having to deal with traditionallymonolithic administrative functions is a simple no-go. Enter BIG-IQ. BIG-IQ enables administrators to centrally manage BIG-IP infrastructure across the IT landscape. BIG-IQ discovers, tracks, manages, and monitors physical and virtual BIG-IP devices - in the cloud, on premise, or co-located at your preferred datacenter. BIG-IQ is a stand alone product available from F5 partners, or available through the AWS Marketplace. BIG-IQ consolidates common management requirements including but not limited to: Device discovery and monitoring: You can discovery, track, and monitor BIG-IP devices - including key metrics including CPU/memory, disk usage, and availability status Centralized Software Upgrades: Centrally manage BIG-IP upgrades (TMOS v10.20 and up) by uploading the release images to BIG-IQ and orchestrating the process for managed BIG-IPs. License Management: Manage BIG-IP virtual edition licenses, granting and revoking as you spin up/down resources. You can create license pools for applications or tenants for provisioning. BIG-IP Configuration Backup/Restore: Use BIG-IQ as a central repository of BIG-IP config files through ad-hoc or scheduled processes. Archive config to long term storage via automated SFTP/SCP. BIG-IP Device Cluster Support: Monitor high availability statuses and BIG-IP Device clusters. Integration to F5 iHealth Support Features: Upload and read detailed health reports of your BIG-IP's under management. Change Management: Evaluate, stage, and deploy configuration changes to BIG-IP. Create snapshots and config restore points and audit historical changes so you know who to blame. 😉 Certificate Management: Deploy, renew, or change SSL certs. Alerts allow you to plan ahead before certificates expire. Role-Based Access Control (RBAC): BIG-IQ controls access to it's managed services with role-based access controls (RBAC). You can create granular controls to create view, edit, and deploy provisioned services. Prebuilt roles within BIG-IQ easily allow multiple IT disciplines access to the areas of expertise they need without over provisioning permissions. Fig. 1 BIG-IQ 5.2 - Device Health Management BIG-IQ centralizes statistics and analytics visibility, extending BIG-IP's AVR engine. BIG-IQ collects and aggregates statistics from BIG-IP devices, locally and in the cloud. View metrics such as transactions per second, client latency, response throughput. You can create RBAC roles so security teams have private access to view DDoS attack mitigations, firewall rules triggered, or WebSafe and MobileSafe management dashboards. The reporting extends across all modules BIG-IQ manages, drastically easing the pane-of-glass view we all appreciate from management applications. For further reading on BIG-IQ please check out the following links: BIG-IQ Centralized Management @ F5.com Getting Started with BIG-IQ @ F5 University DevCentral BIG-IQ BIG-IQ @ Amazon Marketplace7.8KViews1like1CommentAutomate import of SSL Certificate, Key & CRL from BIG-IP to BIG-IQ
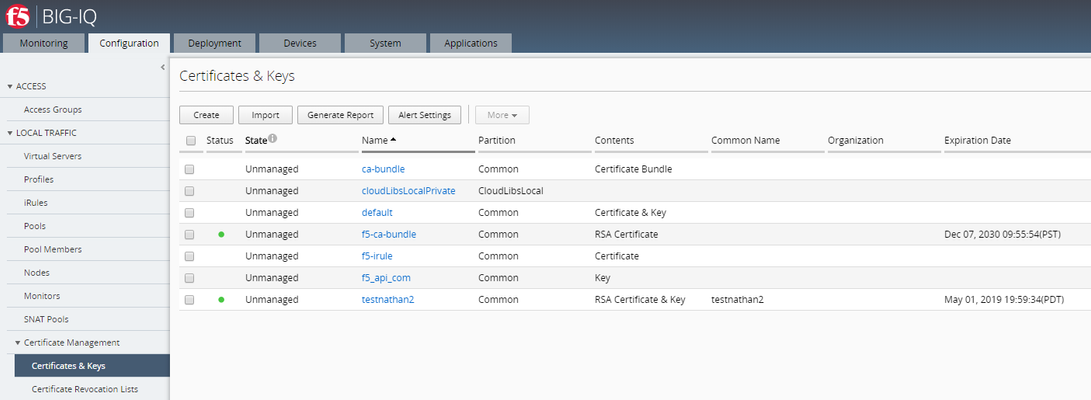
The functionality to automate the import of SSL cert & key from BIG-IP to BIG-IQ is available in the product starting BIG-IQ 7.0 and above. This script should not be used on BIG-IQ 7.0+ as it has not been tested on those versions. This script will import all supported SSL Certificate, Key & CRL that exist as unmanaged objects on this BIG-IQ which can be found on the target BIG-IP. Steps performed by the script: Gather certificateand key metadata (including cache-path) from BIG-IPs Download certificate and key file datafrom BIG-IPs Upload certificateand key file data to BIG-IQ Prerequisite:Discover and import LTM services before using this script.The target BIG-IP will be accessed over ssh using the BIG-IP root account. Installation:The script mustbe installed in BIG-IQ under /shared/scripts: # mkdir /shared/scripts# chmod +x /shared/scripts/import-bigip-cert-key-crl.py Command example: # ./import-bigip-cert-key-crl.py <big-ip IP address> Enter the root user's password if prompted. Allowed command line options:-h show this help message and exit-l LOG_FILE,log to the given file name--log-level {debug,info,warning,error,critical},set logging to the given level (default: info)-p PORT BIG-IPssh port (default: 22) Result:Configuration > Certificate Management > Certificates & Keys Before running the script: After running the script: Location of the scriptson GitHub:https://github.com/f5devcentral/f5-big-iq-pm-team In case you BIG-IQ is running on Hardware: Step 1: Install packages using pip, targeting a location of your choice # mkdir py-modules# pip install --target py-modules requests argparse Step 2: Run using python2.7, adding py-modules to the python path # PYTHONPATH=py-modules python2.7 import-bigip-cert-key-crl.py <big-ip IP address>4.9KViews1like43CommentsAdd a Data Collection Device to your BIG-IQ Cluster
Gathering and analyzing data helps organizations make intelligent decisions about their IT infrastructure. You may need a data collection device (DCD) to collect BIG-IP data so you can manage that device with BIG-IQ. BIG-IQ is a platform that manages your devices and the services they deliver. Let’s look at how to discover and add a data collection device in BIG-IQ v5.2. You can add a new data collection device to your BIG-IQ cluster so that you can start managing it using the BIG-IP device data. In addition to Event and Alert Log data, you can view and manage statistical data for your devices. From licensing to policies, traffic to security, you’ll see it all from a single pane of glass. But you need a DCD to do that. So, we start by logging in to a BIG-IQ. Then, under the System tab, go to BIG-IQ Data Collection and under that, click BIG-IQ Data Collection Devices. The current DCD screen shows no devices in this cluster. To add a DCD, click Add. This brings us to the DCD Properties screen. For Management Address field, we add the management IP address of the BIG-IP/DCD we want to manage. We’ll then add the Admin username and password for the device. For Data Collection IP Address, we put the transport address which is usually the internal Self-IP address of the DCD and click Add. The process can take a little while as the BIG-IQ authenticates with the BIG-IQ DCD and adds it to the BIG-IQ configuration. But once complete, you can see the devices has been added successfully. Now you’ll notice that the DCD has been added but there are no Services at this point. To add Services, click Add Services. In this instance, we’re managing a BIG-IP with multiple services including Access Policies so we’re going to activate the Access services. The listener address already has the management address of the DCD populated so we’ll simply click Activate. Once activated, you can see that it is Active. When we go back to the Data Collection Devices page, we can see that the Access Services have been added and the activation worked. Congrats! You’ve added a Data Collection Device! You can also watch a video demo of How to Add a data collection device to your BIG-IQ cluster. ps Related: Lightboard Lesson: What is BIG-IQ?3.3KViews0likes6CommentsF5 Venafi Solution for Enterprise Key and Certificate Management
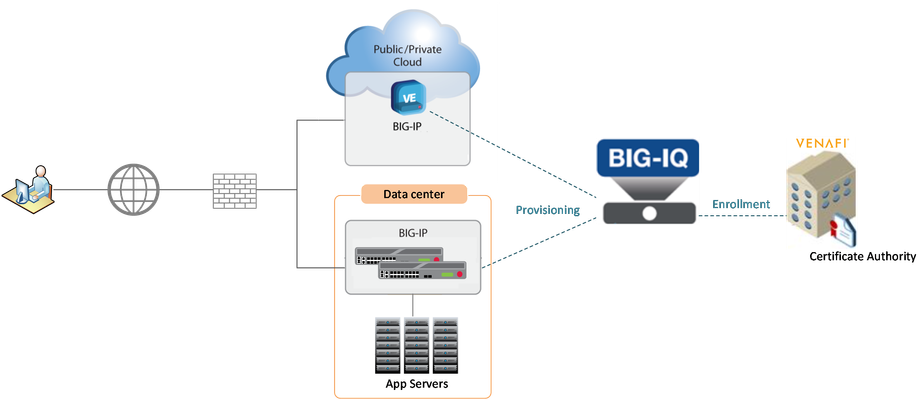
Solution Overview If you have deployed multiple BIG-IP systems to protect your business applications, you know how complex—and important—the certificate and key management process is. Certificates and keys play a critical role in securing data and application identity, and any mismanagement represents a significant risk to security and overall operations. F5 has partnered with Venafi, the industry leader in machine identity protection, to develop a BIG-IQ based integrated solution that automates the certificate and key management lifecycle—creating certificate requests, retrieving and managing certificates and keys, and overseeing their distribution to multiple BIG-IP systems. This comprehensive solution enables our customers to simplify and centralize the control of this crucial process while maintaining high levels of security. Solution Deployment F5 BIG-IQ is at the core of this integrated solution, automating management of the entire key and certificate lifecycle. BIG-IQ establishes a secure control channel with Venafi Trust Protection Platform (TPP) for certificate signing requests and enrollment. Once the certificates are signed and received from Venafi TPP, BIG-IQ enables you to assign them to the virtual servers and securely provision them to BIG-IP systems. Bill of materials F5 BIG-IQ, managing BIG-IP systems Venafi Trust Protection Platform (TPP) Deployment Steps Before beginning the detailed configuration, we recommend verifying the network reachability and hostname resolution of Venafi TPP server from BIG-IQ. Step-1: Add Venafi as third party CA provider in BIG-IQ From the BIG-IQ management GUI, click on the Configuration tab and navigate to LOCAL TRAFFIC >> Certificate Management >> Third Party CA Management. Click the Create button and select Venafi as the CA provider. Enter the WebSDK URL and credentials to authenticate with Venafi. Once configured, click the Test Connection button to verify BIG-IQ can reach Venafi TPP server. Click the Save & Close button. The Venafi provider you added appears in the list. Click the Edit Policy link of the new Venafi provider you added. In the Policy Folder Path, type the path of the Venafi TPP where the certificates and keys are located, and then click the Get button. BIG-IQ populates the Policy Folder List with the policies to where BIG-IQ should send Certificate Signing Requests. At this point (or later), you have the option to rename the policies for easier identification by editing its nickname. Click the Save & Close button. Step-2: Create a CSR to get a signed certificate from Venafi Navigate to LOCAL TRAFFIC >> Certificate Management >> Certificates & Keys and click on the Create button. Select ‘Venafi’ as the Issuer, and the policy folder. Specify the Certificate and Key properties. Click the Save & Close button. BIG-IQ generates the CSR and sends it to Venafi TPP for signed certificates and keys. You can now assign this imported certificate to your managed BIG-IP VE devices. Step-3: Assign the certificate and key to the application Navigate to LOCAL TRAFFIC >> Profiles. Click the Create button. Create a Client SSL Profile selecting the certificate and the key. Once configured, click the Save & Close button Navigate to LOCAL TRAFFIC >> Virtual Servers. Click the Create button. Create a virtual server and assign the client SSL profile. Once configured, click the Save & Close button Step-4: Deploy the configuration to a target BIG-IP System Click on the Deployment tab and navigate to EVALUATE & DEPLOY >> Local Traffic & Network. In Deployment section, Click the Create button. Select the Virtual Server object and Target Device- BIG-IP system. Click the Deploy button. Click on the configuration tab and navigate to LOCAL TRAFFIC >> Virtual Servers. You will see the virtual server has been successfully deployed to the target BIG-IP system. Summary As this demonstration shows, BIG-IQ not only offers a centralized management solution for BIG-IP systems, it also provides a one stop solution for key and certificate lifecycle automation through its integration with Venafi TPP. This simple, easy-to-deploy solution enables you to deliver secure applications more quickly and effectively, whether on-premises or on cloud. Additional Links Key and Certificate Management with F5 and Venafi (video) F5 BIG-IQ knowledge center Venafi marketplace2.8KViews4likes1CommentManaging BIG-IP Licensing With BIG-IQ
If the article title doesn't have you excited, I don't know what else to do. You know BIG-IQ centralizes management and analytics of BIG-IP and Per-App Virtual Editions across your enterprise. Were you aware that BIG-IQ can run as a License Manager to simplify more complicated subscription and license pool requirements... for free? Subscriptions, RegKey Pools, offline licensing, and all the other customer requirements made licensing a quagmire that BIG-IQ License Manager can help solve. Below you will find several resources to assist configuring BIG-IQ as a License Manager or just simply manage a few licenses. Configuring BIG-IQ as a License Manager This video provides a walk through demonstration of setting up BIG-IQ as a License Manager. If you already have BIG-IQ running as a Configuration Manager, you already have this working. I recommend watching this on Youtube directly. How to Manage Licenses Within BIG-IQ This video provides a detailed walkthrough example of how to manage subscription licenses within BIG-IQ. I recommend watching this on Youtube directly. Further Resources: BIG-IQ Centralized Management: BIG-IP VE Subscriptions - The document you want when configuring BIG-IQ as License Manager or how to manage licenses within BIG-IQ. AskF5 K77706009: Using BIG-IQ License Manager to remotely manage BIG-IP Virtual Edition licenses2.7KViews0likes14CommentsAgility 2020 - you're invited!
In-person event for Agility 2020 has been cancelled. Please see the Agility Event Page for more details. (Update 2/28/2020) In an abundance of caution for our customers, partners and employees, we have made the tough decision to cancel our in-person event for Agility 2020 due to the escalating travel and safety concerns related to the global COVID-19 (Coronavirus) outbreak. While we are disappointed to miss sharing ideas and solving problems with customers and partners from around the globe in person, we believe this is the best decision for everyone's welfare. We are rapidly developing an alternative to Agility as a virtual experience in the near term to deliver valuable Lab, Break-out Session, Certification and Keynote content to our customers and partners. Check back regularly for more details on the virtual event or email F5Agility@F5.com for additional information. <Professor Farnsworth imitation>Good news, everybody!</Professor Farnsworth imitation> As you know, there was no Agility 2019. This was in part so that we could reset the time of year for the conference from August to March. Agility 2020will be held from March 16-19, 2020 at theSwan & Dolphinin Orlando, Florida. Orlando, and Disney, and putt-putt golfing... That's right, *puts on ears* we're going to Disneyworld - and you are all cordially invited to participate in labs and breakouts, meet fellow F5 users, talk with F5 and partner subject-matter experts, learn to develop and deploy applications in days instead of months, secure your apps at scale in a multi-cloud environment, and hear about our vision for the future of F5 and NGINX. Registration is now open! The DevCentral team will be busy as usual that week. We areallflying over, and will be: hosting our usual booth and giving out swag in the expo hall, hosting a walk-in Nerdery zone next to our booth, where folks can drop in to speak with one of our subject-matter experts, presenting breakout sessions, hanging out at Geekfest, connecting community, enjoying the exclusive community area at the final night party, and of course, spoiling the dev/central MVPs during the joint 2019-20 MVP Summit at Agility with special sessions and activities. If you'd like to do more than pick up all the knowledge being dropped, if you have some cool technical stories or lessons-learned to share, please stay tuned for the open call for proposals which should go live in early December - so please start getting those great breakout, lightening round, and open talk ideas ready. Hope to see you there!2.4KViews3likes1CommentBIGREST - A Python SDK for F5 iControl REST API
This article is written by, and published on behalf of, DevCentral MVP Leonardo Souza. --- Hello all, this is going to be my shortest article so far. As you probably know already both BIG-IP and BIG-IQ have an iControl REST API. However, if you play with that very often, you will find yourself creating some scripts to perform some common tasks. If you put those scripts together, you kind of have an SDK that other people can use to simplify the use of the API. Almost all vendors these days have an SDK for their products, and the language of choice is mainly Python because of the language simplicity. As the article title says, I wrote BIGREST that is a Python SDK to work with iControl REST API. The SDK fully supports both BIG-IP and BIG-IQ. I wanted to advance my Python andiControl REST knowledge, so this was a useful way of doing that. You may be wondering "Isn't there already a Python SDK foriControl REST?", so let me explain that part. I have used the existing SDK many times in the past, and it was very helpful. The existing Python SDK, the F5-SDK (https://github.com/F5Networks/f5-common-python) is limited, as it mainly supports BIG-IP, and the only supported BIG-IQ functionality is license pools. I wanted to help with the F5-SDK and extend it for BIG-IQ so I looked into the code but I decided the changes I wanted to make made more sense to start from scratch. Some details about these differences are here HTTP paths HTTP paths can be seen as just a tmsh command. In the following examples, HTTP path is “/mgmt/tm/ltm/pool”. F5-SDK mgmt.tm.ltm.pools.pool.create(name='mypool', partition='Common') Python code for every HTTP path; requires more code. BIGREST device.create("/mgmt/tm/ltm/pool", {"name": “mypool”, “partition”: “Common”}) The user tells the HTTP path they want to use. less code to write and support all current HTTP paths and new HTTP paths are automatically supported. BIG-IQ and Python Support F5-SDK created to support BIG-IP REST API supports Python 2 and Python 3 Python 2 was discontinued in 2020 BIGREST created to support BIG-IP and BIG-IQ. supports only Python 3 The code can use new Python 3 functionalities to make it simpler to write and read. Method Names F5-SDK uses some names of the REST API like collection. Example: mgmt.tm.ltm.pools.get_collection() BIGREST tries to use only tmsh names. Example: device.load("/mgmt/tm/ltm/pool") In this case, you load the objects to memory, and if you want you save them after. Similar to load the configuration from the disk using tmsh, and saving it to the disk after. I wrote a very extensive documentation explaining how the SDK works, so you will find all the details there. For more information, including the link for the code and documentation, go to the code share: https://devcentral.f5.com/s/articles/BIGREST1.9KViews3likes1CommentBIG-IQ Client Certificate (PKI) Authentication
Beginning with version 7.0.0, BIG-IQ allows users to authenticate to the GUI using a signed SSL client certificate instead of a username and password. Client certificate authentication works in conjunction with an external authentication provider. The BIG-IQ verifies the user's identity by validating the client certificate against a list of trusted CAs(certificateauthorities), and optionally checking the certificate for revocation against the configured certificate revocation list (CRL). Then it extracts the username from the certificate and uses it to query an external server (directory) for group membership information for the user, which is used to determine the user's authorization to access various features of the BIG-IQ. Set upclientcertificateauthentication On the BIG-IQ, client certificate authentication works in conjunction with an Active Directory or an LDAP authentication provider.Prior to setting upcertificate authentication, make sure you have the following: External Active Directory or LDAP server X.509clientcertificatesfor the users to be authenticated. Additional clientcertificatescan be generated at any later time. All theX.509issuing CAcertificates (root and intermediate) for the clientcertificates Certificate Revocation Lists (CRLs) for all the revoked certificates, if applicable Additionally, you have to have a good understanding of the structure (attributes) of theclient certificates you are going to use, as well as of your directory schema. The login name of the user will be extracted from the certificate, and then it will be used to find the user in the directory. Prior to enablingclient certificate authentication, the user must set up either anActive Directoryor anLDAPauthentication provider(use the documentation corresponding to your BIG-IQ version).To avoid being locked out of BIG-IQ,before enabling client certificate authentication,make sure the settings are correct by clicking theTestbutton at the bottom of theauthentication providerpropertiesscreen.A successful test ensuresBIG-IQ can successfully connect to the remote directory and search usersin the directory. Also, make sure to set up the necessaryusergroups corresponding to directory groups and to put them in the appropriate roles. Whether the user is authenticated using a certificate or using user/password, access to various areas of the BIG-IQ will be granted according to the RBAC settings on the groups the user is a member of. Following that,check theEnable Client Certificate Authenticationcheck-box. This opensup a new area of the screen, with the following settings: CACertificate-upload afilecontaining theX.509CAcertificate(s) that sign and validate the user-provided SSL client certificatesused to authenticate.This can containone or several issuing CAcertificates, including both root and intermediatecertificates. Note:To successfullyvalidate aclient certificateissued by an intermediate CA, all the intermediate CA certificates leading up toas well asthe root CAmustbe present in the CAcertificatefile. Certificate Username Attribute-the attribute value to extract from the client certificate,containing the username (oruser identifier).The value extractedcan beeitherthe exact username or a longer string for which the username is just a substring. TheBIG-IQsupports the followingcertificate attributes: Common Namein theSubject Name(Subject CN) The followingattributesin theSubject Alternative Name(SAN): Directory Name DNS Name Email IP Address Registered ID URI OtherName(BIG-IQonly supportsuserPrincipalNameinOtherName) If the certificate contains multiple attributes with the same name, e.g., multiple Other Name attributes under the SAN, the username corresponding to the Other Name Certificate Username Attribute will be the concatenation of all thematchingattribute values, space-separated. Certificate Username Filter-anoptional regex filter used to extract the exact username from the value of theCertificate Username Attributein the certificate. Ifthis filter isnot specified, the entire attribute value is used as a username. Directory User Search Filter-asearchfilterused to find users in the directory, based on the username extracted from the certificate, and after applying the optionalCertificate Username Filter.The LDAP search query is obtained by replacing the{username}token in the filter with the actual username. For the Certificate Revocation List, you can optionallyuploada file containing one or more X.509 CRLs, one for each issuing CA.If more certificates are revoked at a later time, the CRL file needs to be re-generated and re-uploaded to keep the CRLs known to the BIG-IQ up-to-date. All the client certificates in the CRL file will fail validation, therefore the corresponding users will be deniedaccess. Note:CRLs have aNext updatefield. If current time is past theNext updatetime ofthe CRL set on the authentication provider, the CRL is considered obsolete,thereforeall the client certificates will failvalidation. Make sureto update the CRL prior to its expiration at the Next update time. ChecktheEnable Local Authentication Fallback check-box if you wantBIG-IQ tobe able toauthenticate usersagainstthe local authentication provider in addition to certificateauthentication. Eventhough in the end theBIG-IQadministratormay want to only allowcertificate authentication, we recommend thatsheenables local authentication fallback at first, until she has verified certificate authentication works correctly. This would prevent beingaccidentally locked outof BIG-IQdue to incorrectsettingsor mismatched client and CA certificates. Example1: Assume the client certificate has the following subject: Subject: C=US, ST=Washington, L=Seattle, O=ACME Corp, OU=Engineering,CN=John Doe/emailAddress=j.doe@acme.com Assume the directory entry corresponding to the user containsthe followingattributes: dn:CN=JohnDoe,OU=Users,OU=NorthAmerica,DC=olympus,DC=F5Net,DC=com CN=John Doe Using the Certificate Username Attribute Common Name extracts theusernameJohn Doe. Either don’t enter a Certificate Username Filteror set it to“.+” (match all characters in the input). Theresultingusernameafter applying the filter isJohn Doe. Using theDirectory User Search Filtercn={username}yields the search expression:cn=John Doe. Thisqueryretrieves the above directory entry corresponding to userJohn Doe. Example2: Assume the client certificate has the followingentries under theSubject Alternative Name (SAN): otherName.1 =1.3.6.1.4.1.311.20.2.3;UTF8:JOHN.DOE.J.III.1042156825 otherName.2 =1.3.6.1.4.1.311.20.2.3;UTF8:j.doe@acme.com otherName.3 = 1.3.6.1.5.5.7.8.7;IA5STRING:_mail.example.com Assume the directory entry corresponding to the user containsthe followingattributes: userPrincipalName: 1042156825@acme.com mail: J.Doe@us.acme.com Using the Certificate Username AttributeOtherName extracts theusernamestring (userPrincipalNameonly,OID= 1.3.6.1.4.1.311.20.2.3): JOHN.DOE.J.III.1042156821j.doe@acme.com Using theCertificate Username Filter“[0-9]*”weextract the string1042156825. That username (or rather user identifier) will be substituted in theDirectory User Search Filter. Using theDirectory User Search FilteruserPrincipalName={username}@acme.comyields the search expression:userPrincipalName=1042156825@acme.com. Thisqueryretrieves the above directory entry corresponding to user John Doe. Alternatively, using theCertificate Username Filter“[A-Za-z0-9.]+(?=@acme.com)” we extract the string(username)j.doe. That username will be substituted in theDirectory User Search Filter. Using theDirectory User Search Filtermail={username}@us.acme.comyields the search expression:mail=j.doe@us.acme.com. Thisqueryretrieves the above directory entry corresponding to user John Doe. Log intoBIG-IQGUI using aclientcertificate Prior to authenticating toBIG-IQ,import the SSL client certificate into the web browser. The imported file must contain both the X.509 certificate and the associated private key. It is aPKCS#12file, having the extension .p12 or .pfx. If the file is password-protected,youneed to enter the passwordwhenimportingthe certificate.You will also need to provide theprivate key’spassword, if applicable. For stronger security, we recommend that both theprivate keyand thePKCS#12bundle arepassword-protected. Note: The certificateimport user workflow varies slightly across browsers and across operating systems. Thecertificateimport functionality is usually located in the browser preferences/settings, underPrivacy & Security > Certificates > Your Certificates. In the browser address bar, enter aBIG-IQ URI.That first request in unauthenticated.Therewill beno login page, just a blank page.The browser will prompt the user to select one of the certificates from the browser's personal certificate store.Only the certificatesthat could potentially be successfully validated by the BIG-IQ, i.e., whose issuers are trusted by the BIG-IQ, will be displayed. In the browser, you can eventually view the certificate details, i.e., their subject, issuer,etc. Selectthedesired clientcertificatefrom thelist. If the fallback mechanism to allow local user/password authentication is enabled, the user may choose not to send a client certificate, case in which the browser willdisplay the login screen,prompting the userto enter a user/password combination, which will be used to authenticate against the local authprovider. If localauthenticationfallback isdisabledandthe user choosesnot to send a client certificate,or if there is no certificate that could potentially be successfully validated by the BIG-IQ, authentication will fail. The first step in certificate authenticationconsists ofthe BIG-IQ successfully validatingthe certificate presented by the browser.If thecertificatehas been issued by one of the trusted CAs,is not expired,and it has not been revoked,certificate validation succeeds. If certificate validation fails for various reasons, the browser request returns a 400code (SSL certificate error). Next, the BIG-IQ extracts the username from the certificate, according to theCertificate Username AttributeandCertificate Username Filtersettings. Then it looks up the user in the directory, by executing the search query corresponding to theDirectory User Search Filtersetting.If the user is found in the directory, the BIG-IQ retrieves the user properties, including the groupsthe useris a member of. Access to various areas of the BIG-IQ isgranted according tothe RBAC permissions on the groups the user is a member of. If the authentication is successful, the user is taken to the splash page, or alternatively to the last visited page if the user has previously logged in to the BIG-IQ. To log out after authenticatingwith the client certificate presented by the browser,or to log in using a different certificate,the user will have to close the browser sessionto clear the SSL session established between the browser and the BIG-IQ. To prevent future logins using the same browserand certificate, the user will have to remove the certificate from the browser. Recover from BIG-IQ lockout Afterenablingclient certificate authentication,there might be some unfortunate situations when the userislockedout of BIG-IQ. Reasons include incorrect settings on theauthentication provider, invalid, expired, or revoked certificates, and expired CRLs. To get out of that bad situation, if fallback to local authentication is enabled, when the browser prompts the user to choose a certificate toauthenticate, choose to not send a certificate (click the Cancel button). The browser willdisplay theBIG-IQlogin screen,prompting the userto enter a user/password combinationto log in.After logging in as an administrator using thelocal authenticationprovider, fix the problem that has caused the lockout, then resume usingcertificate authentication. Iffallback to local authentication isdisabled,sshinto theBIG-IQ. At the shell prompt, run the following command: client-cert-auth -x This will reset the BIG-IQ authentication to the default username/password authenticationusing thelocal authenticationprovider. Itwill alsodeletethe authentication providerthat has caused the lockout.1.8KViews3likes4CommentsHow to Use BIG-IQ and Ansible to Build Advanced BIG-IP Automation Workflows
It’s no secret that automation of networking, security, and application development processes offers a laundry list of benefits—reduced deployment time, lowered cost, fewer errors, and more resilient systems, to name a few. One of the most popular tools for building automation workflows is Ansible. Ansible is a powerful, open-source tool that simplifies and automates many common tasks and enables infrastructure as code for creating, deploying, and managing F5 application delivery and security services. This is accomplished through playbooks and roles available on Ansible Galaxy. Another way to streamline working with BIG-IP is with BIG-IQ Centralized Management. BIG-IQ combines deep, app-centric visibility and dashboarding together with device, configuration, and policy management in a unified, intuitive user interface. From BIG-IQ, you can create new BIG-IP Virtual Editions (VEs), provision them with Declarative Onboarding, create advanced AS3 services, move deployments, upgrade software, and much more. Together Ansible and BIG-IQ make automation and management of your BIG-IP environment simple and straightforward—enabling an effective, intuitive, data-rich, and highly visual solution that offers value to networking/F5 gurus, security practitioners, and application owners/developers alike. To make things even easier, the F5 team has developed several community-supported Ansible roles that are designed to inject automation into workflows and make BIG-IQ’s simple app-centric management functionality even better. Please note that this workflow assumes that you already have a BIG-IQ Centralized Management deployment up and running. The end result will be a fully provisioned BIG-IP deployment that can be fully managed—client-to-server visibility, troubleshooting, object level configuration, etc.—from BIG-IQ’s intuitive, role-specific GUI. You can get started with these roles and workflows today by checking out F5’s repository on Ansible Galaxy. To use these Ansible roles and playbooks, you’ll need to download and install them to a local workstation that will be used for managing F5 deployments. Use the Ansible roles for BIG-IQ below to: Create new VEs Onboard VEs with DO Create and deploy common objects such as SSL certs and WAF policies Create AS3 application delivery and security services Move deployments across BIG-IPs For additional how-to-use resources, guidance, and labs for BIG-IQ, check out the video library and the BIG-IQ labs. Create a BIG-IP VE in AWS tasks: - name: Create a VE in AWS include_role: name: f5devcentral.bigiq_create_ve vars: cloud_environment: "BIG-IQ AWS US-East" ve_name: "bigipvm01" register: status - name: Get AWS BIG-IP VE IP address (port 8443) debug: msg: "{{ ve_ip_address }}" - name: Get AWS BIG-IP VE private Key Filename debug: msg: "{{ private_key_filename }}" Onboard the New BIG-IP VE with Declarative Onboarding tasks: - name: Onboard BIG-IP VE with DO include_role: name: f5devcentral.atc_deploy vars: atc_service: Device atc_method: POST atc_declaration: "{{ lookup('template','do_bigip_aws.j2') }}" atc_delay: 30 atc_retries: 15 register: atc_DO_status do_bigip_aws.j2: { "class": "DO", "declaration": { "schemaVersion": "1.5.0", "class": "Device", "async": true, "Common": { "class": "Tenant", "myLicense": { "class": "License", "licenseType": "licensePool", "licensePool": "byol-pool", "bigIpUsername": "admin", "bigIpPassword": "secret" }, "myProvision": { "class": "Provision", "ltm": "nominal", "avr": "nominal" }, "myNtp": { "class": "NTP", "servers": [ "169.254.169.123" ], "timezone": "UTC" }, "admin": { "class": "User", "shell": "bash", "userType": "regular", "partitionAccess": { "all-partitions": { "role": "admin" } }, "password": "secret" }, "hostname": "bigipvm01.example.com" } }, "targetUsername": "admin", "targetHost": "{{ ve_ip_address }}", "targetPort": 8443, "targetSshKey": { "path": "{{ private_key_filename }}" }, "bigIqSettings": { "conflictPolicy": "USE_BIGIQ", "deviceConflictPolicy": "USE_BIGIP", "failImportOnConflict": false, "versionedConflictPolicy": "KEEP_VERSION", "statsConfig": { "enabled": true } } } Create SSL Certificate and Key on BIG-IQ tasks: - name: Authenticate to BIG-IQ uri: url: https://{{ provider.server }}:{{ provider.server_port }}/mgmt/shared/authn/login method: POST headers: Content-Type: application/json body: username: "{{ provider.user }}" password: "{{ provider.password }}" loginProviderName: "{{ provider.auth_provider | default('tmos') }}" body_format: json timeout: 60 status_code: 200, 202 validate_certs: "{{ provider.validate_certs }}" register: auth - name: Create SSL Certificate and Key on BIG-IQ uri: url: https://{{ provider.server }}:{{ provider.server_port }}/mgmt/cm/adc-core/tasks/certificate-management method: POST headers: Content-Type: application/json X-F5-Auth-Token: "{{ auth.json.token.token }}" body: | { "issuer": "Self", "itemName": "mywebapp.crt", "itemPartition": "Common", "durationInDays": 365, "country": "US", "commonName": "mywebapp.example.com ", "division": "MyDiv", "organization": "MyOrg", "locality": "Seattle", "state": "WA", "subjectAlternativeName": "DNS: mywebapp.example.com", "securityType": "normal", "keyType": "RSA", "keySize": 2048, "command": "GENERATE_CERT" } body_format: json timeout: 60 status_code: 200, 202 validate_certs: "{{ provider.validate_certs }}" register: json_response Pin and Deploy SSL Certificates and Key to BIG-IP tasks: - name: Pin and deploy SSL certificate and key to BIG-IP include_role: name: f5devcentral.bigiq_pinning_deploy_objects vars: bigiq_task_name: "Deployment through Ansible/API - mywebapp" modules: - name: ltm pins: - { type: "sslCertReferences", name: "mywebapp.crt" } - { type: "sslKeyReferences", name: "mywebapp.key" } device_address: "{{ ve_ip_address }}" register: status Deploy an AS3 Service to BIG-IP tasks: - name: Deploy AS3 application services to BIG-IP include_role: name: f5devcentral.atc_deploy vars: atc_service: AS3 atc_method: POST atc_declaration: "{{ lookup('template','as3_bigiq_https_app.j2') }}" atc_delay: 30 atc_retries: 15 register: atc_AS3_status as3_bigiq_https_app.j2: { "class": "AS3", "action": "deploy", "declaration": { "class": "ADC", "schemaVersion": "3.12.0", "target": { "address": "{{ ve_ip_address }}" }, "myorg": { "class": "Tenant", "mywebapp": { "class": "Application", "schemaOverlay": "AS3-F5-HTTPS-offload-lb-existing-cert-template-big-iq-default-v1", "template": "https", "serviceMain": { "class": "Service_HTTPS", "pool": "Pool", "enable": true, "serverTLS": "TLS_Server", "virtualPort": 443, "profileAnalytics": { "use": "Analytics_Profile" }, "virtualAddresses": [ "0.0.0.0" ] }, "Pool": { "class": "Pool", "members": [ { "adminState": "enable", "servicePort": 80, "serverAddresses": 10.1.3.23 } ] }, "TLS_Server": { "class": "TLS_Server", "certificates": [ { "certificate": "Certificate" } ] }, "Certificate": { "class": "Certificate", "privateKey": { "bigip": "/Common/mywebapp.key" }, "certificate": { "bigip": "/Common/mywebapp.crt" } }, "Analytics_Profile": { "class": "Analytics_Profile", "collectIp": false, "collectGeo": false, "collectUrl": false, "collectMethod": false, "collectUserAgent": false, "collectOsAndBrowser": false, "collectPageLoadTime": false, "collectResponseCode": true, "collectClientSideStatistics": true } } } } } Move an AS3 Service Within BIG-IQ Dashboard tasks: - name: Move an AS3 application service in BIG-IQ dashboard. include_role: name: f5devcentral.bigiq_move_app_dashboard vars: apps: - name: myWebApp pins: - name: "myorg_mywebapp" register: status1.4KViews2likes0Comments